AdGuard releases its proprietary TrustTunnel VPN protocol as open-source software, challenging existing solutions with HTTPS-mimicking design but facing adoption hurdles.

The VPN protocol landscape shifted this week as AdGuard made its proprietary TrustTunnel technology publicly available on GitHub under a permissive MIT license. This move fulfills a long-standing promise to open-source the protocol powering AdGuard VPN clients, positioning TrustTunnel as an alternative to established protocols like WireGuard and OpenVPN. While framed as a win for transparency, the release raises questions about protocol proliferation and real-world viability.
TrustTunnel's core innovation lies in its traffic obfuscation approach. Unlike traditional VPN protocols that create detectable traffic patterns, TrustTunnel mimics standard HTTPS connections by leveraging HTTP/2 or HTTP/3 transport layers with TLS encryption. This design aims to circumvent deep-packet inspection systems used in restrictive regions. Each connection operates through dedicated streams that bundle packets for efficiency, particularly optimizing for mobile networks where instability often plagues VPN performance.
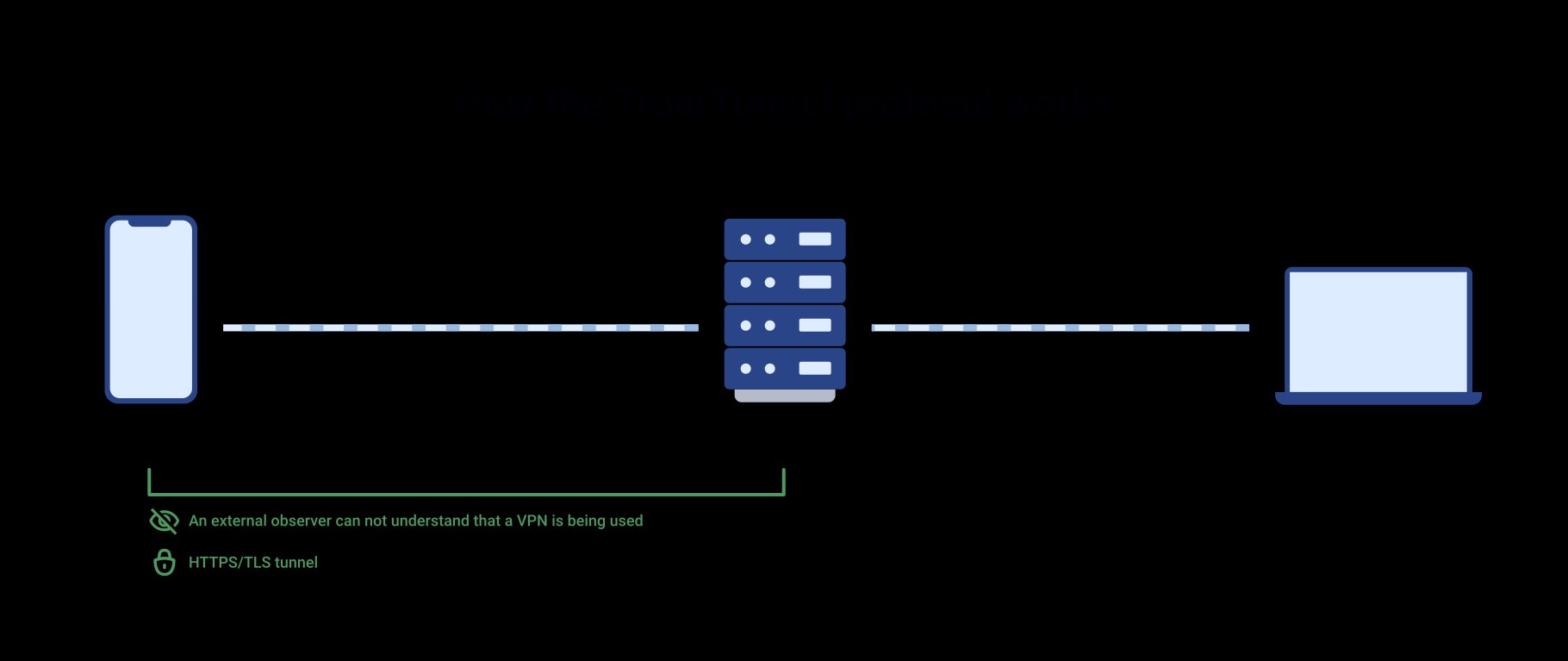 TrustTunnel protocol architecture diagram (Source: trusttunnel.org)
TrustTunnel protocol architecture diagram (Source: trusttunnel.org)
AdGuard positions TrustTunnel as solving critical weaknesses in incumbent protocols. "Solutions like WireGuard or OpenVPN are relatively easy to identify at the network level," explains the technical specification. When these protocols attempt to disguise themselves as regular traffic—often by wrapping data in TCP connections—they incur significant speed penalties due to TCP's acknowledgment requirements. TrustTunnel bypasses this by operating natively at the application layer, theoretically maintaining both stealth and performance.
The open-source release includes comprehensive resources: a full protocol specification, server implementation, and clients for iOS, Android, and desktop platforms (Windows, macOS, Linux). The command-line clients offer granular traffic control features, including:
- Domain/app-specific routing rules
- Real-time connection logging
- Split-tunneling configurations
- Local network traffic management
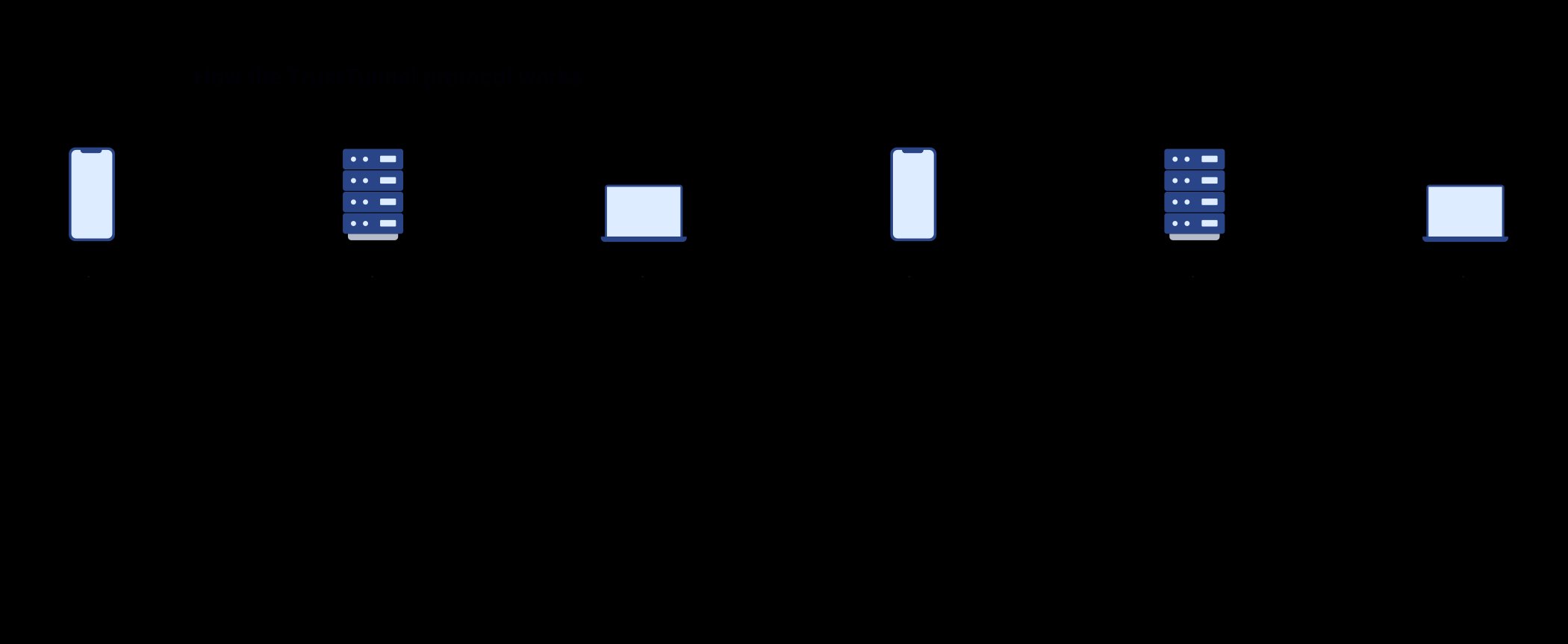 Protocol comparison highlighting TrustTunnel's HTTPS mimicry (Source: trusttunnel.org)
Protocol comparison highlighting TrustTunnel's HTTPS mimicry (Source: trusttunnel.org)
Despite the technical ambition, significant challenges confront TrustTunnel's adoption beyond AdGuard's ecosystem. VPN protocols thrive on network effects—WireGuard's success stems from widespread implementation across providers like Mullvad and IVPN. TrustTunnel enters a crowded field where even promising alternatives like Shadowsocks remain niche outside specific regions. Infrastructure costs present another barrier: Unlike client software, VPN protocols require server-side deployment, and AdGuard offers no managed hosting solution for third parties.
Security researchers also note potential tradeoffs. While TLS encryption provides robust protection, TrustTunnel's reliance on HTTP framing could introduce novel attack surfaces. "Any protocol that intentionally disguises its nature must be scrutinized for downgrade attacks or protocol-confusion vulnerabilities," cautions a network security engineer reviewing the codebase. The GitHub repository shows active issue tracking, but external audits remain pending.
AdGuard's commitment to truly open development appears genuine—the permissive license allows commercial reuse, and documentation encourages third-party implementations. Yet the VPN market's competitive dynamics may hinder adoption. Major providers have invested heavily in WireGuard optimizations, while censorship-resistant tools like Snowflake already address similar use cases through different architectures.
TrustTunnel's success ultimately hinges on two factors: whether its performance claims hold under independent testing in restricted networks, and whether other VPN services view its stealth capabilities as sufficiently compelling to warrant infrastructure overhaul. For now, it stands as a noteworthy experiment in protocol design—one that pushes transparency forward while testing the industry's appetite for innovation beyond the WireGuard paradigm.
Resources:
- TrustTunnel Specification
- GitHub Repository
- iOS Client (App Store)
- Android Client (Play Store)
Comments
Please log in or register to join the discussion