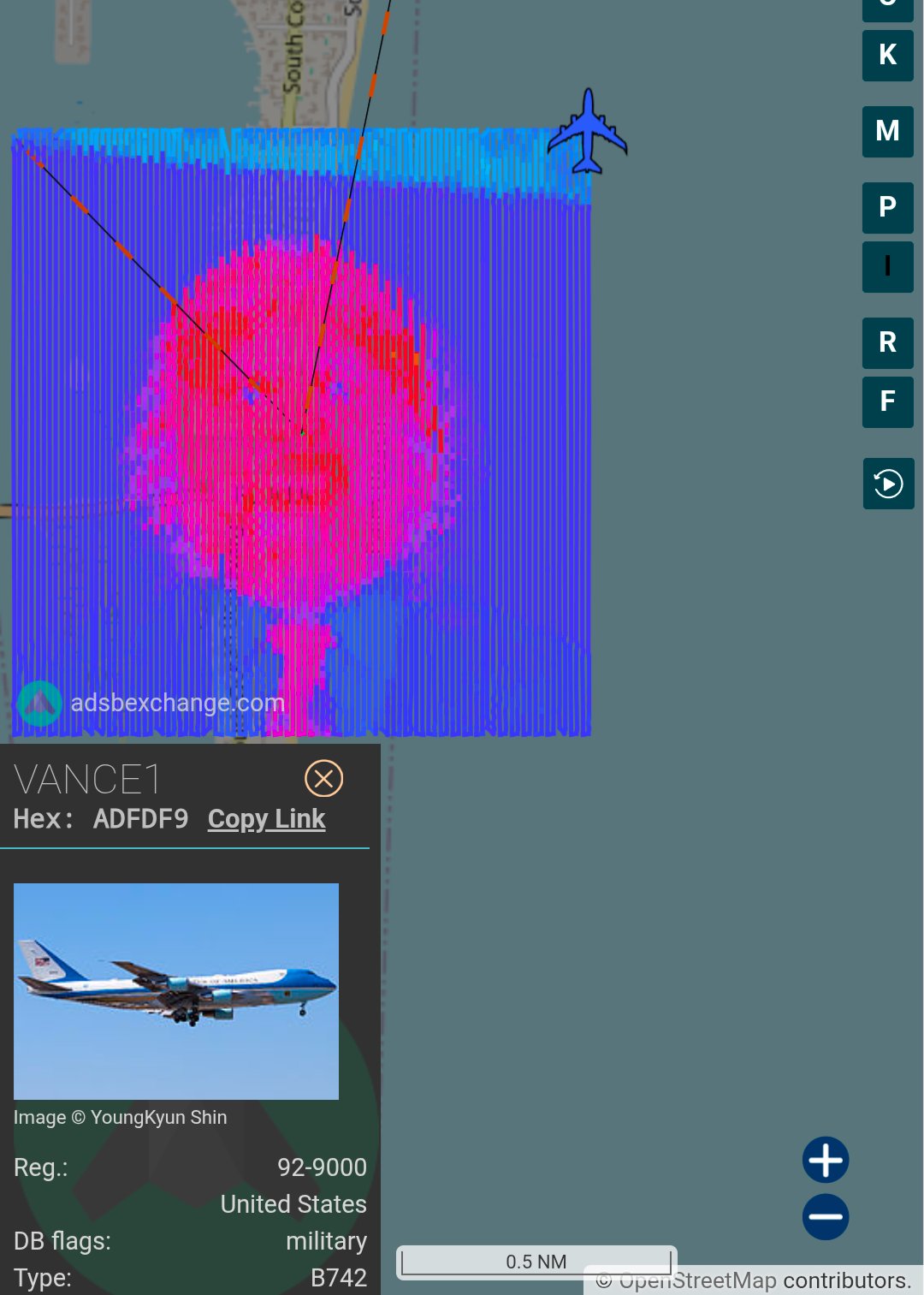
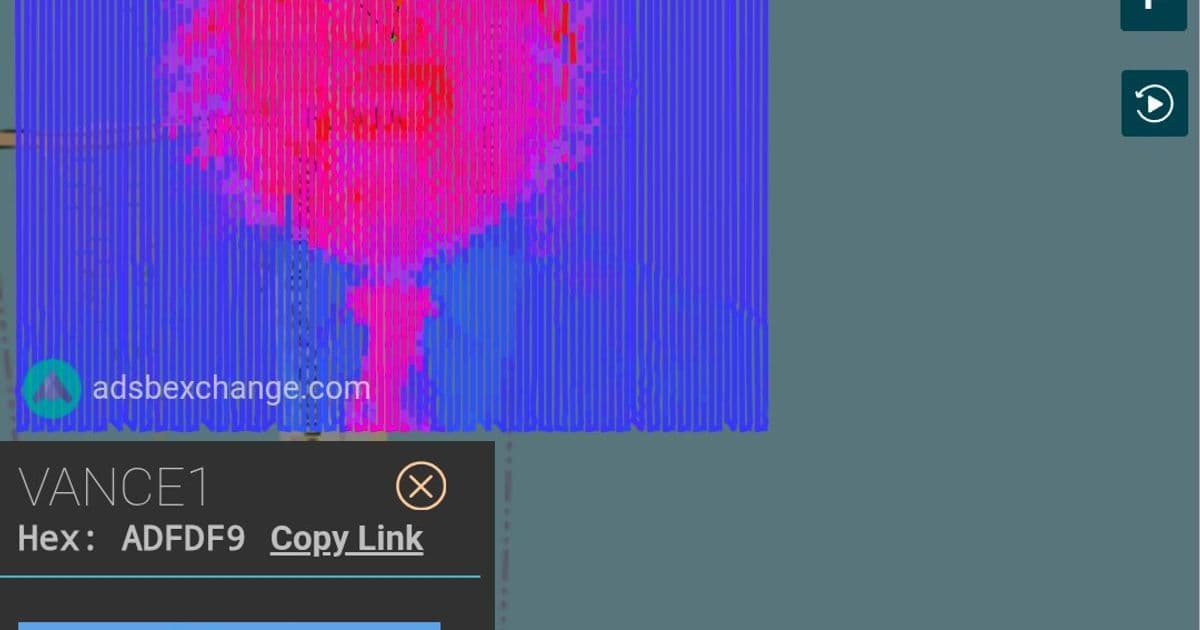
An unknown actor used ADS-B signal spoofing to create a rasterized image of JD Vance over Mar-a-Lago by hijacking the ICAO identity of Air Force Two, raising serious questions about aviation security and the vulnerability of aircraft tracking systems.
Somebody used spoofed ADS-B signals to raster the meme of JD Vance over Mar-a-Lago using AF2 ICAO identity. This incident, if it is still visible, can be viewed at this tracking link, which shows the flight path created by the spoofed signals on January 28, 2026.
The Technical Achievement
The attack demonstrates a sophisticated understanding of both ADS-B protocols and raster graphics. By carefully controlling the position and timing of spoofed aircraft signals, the attacker was able to create a recognizable image of JD Vance over the airspace near Mar-a-Lago. The use of Air Force Two's ICAO identifier (ADFDF9) adds another layer of complexity and potential disruption to the attack.
ADS-B (Automatic Dependent Surveillance-Broadcast) is a critical component of modern air traffic control systems. Aircraft broadcast their position, altitude, velocity, and identification information, which ground stations and other aircraft receive to maintain situational awareness. The system was designed without strong authentication mechanisms, making it vulnerable to various forms of spoofing and interference.
Security Implications
This incident raises several serious security concerns:
Authentication gaps: The ability to spoof ADS-B signals using legitimate aircraft identifiers demonstrates that the system lacks adequate authentication mechanisms. While some regions have implemented ADS-B In/Out requirements, the fundamental security model remains vulnerable.
Presidential security concerns: Using Air Force Two's identity to create a visible pattern over Mar-a-Lago, the residence of the sitting president, could potentially be used to mask real aircraft movements or create confusion during critical situations.
Infrastructure vulnerability: The incident shows that critical aviation infrastructure can be manipulated for non-traditional purposes, including political messaging and meme creation.
The Broader Context
This isn't the first time ADS-B spoofing has been demonstrated, but it represents one of the most creative and visible uses of the technique. Previous research has shown how ADS-B can be spoofed to create ghost aircraft, but using it to create raster graphics is a novel application.
Aviation security experts have long warned about the vulnerabilities in ADS-B systems. The lack of encryption and authentication was a deliberate design choice to keep the system simple and ensure universal compatibility, but this incident highlights the trade-offs involved.
Potential Responses
The incident may prompt several responses from aviation authorities:
Enhanced monitoring: More sophisticated anomaly detection systems could be deployed to identify unusual flight patterns that don't match expected aircraft behavior.
Authentication mechanisms: While difficult to implement retroactively, some form of aircraft authentication could be added to the ADS-B protocol.
Legal frameworks: New regulations might be needed to address the unique challenges posed by ADS-B spoofing, particularly when it involves sensitive airspace or government aircraft identities.
Technical Analysis
The rasterization technique used in this attack likely involved:
- Precise control of spoofed position reports to create the desired image pattern
- Timing coordination to ensure the pattern was visible over the target area
- Use of legitimate ICAO codes to avoid immediate detection
- Possibly multiple spoofed aircraft to create more complex images
The choice of JD Vance as the subject and Mar-a-Lago as the location suggests political motivations, though the exact intent remains unclear. The use of Air Force Two's identity adds a layer of political commentary or provocation.
Industry Reaction
Aviation security professionals are likely to view this incident with concern, as it demonstrates both the vulnerability of ADS-B systems and the creative ways attackers can exploit them. The incident may accelerate discussions about ADS-B security that have been ongoing for years.
Meanwhile, the broader tech community may see this as another example of how security vulnerabilities can be exploited for creative or political expression, similar to how other system vulnerabilities have been used for art projects or political statements.
The incident has already sparked discussions about the need for age verification for ADS-B systems, though the connection between age verification and ADS-B security remains unclear. This may be a humorous reference to the often-proposed but rarely implemented solution of age verification for various online services.
Looking Forward
This incident serves as a reminder that critical infrastructure systems designed without security as a primary concern remain vulnerable to creative exploitation. As aviation continues to rely more heavily on digital systems like ADS-B, the tension between accessibility, simplicity, and security will need to be addressed.
The use of ADS-B for political messaging or meme creation may become more common if the security issues aren't addressed. This could lead to a situation where aviation authorities must balance the legitimate uses of ADS-B with the need to prevent its misuse for non-aviation purposes.
{{IMAGE:2}}
For now, the incident stands as a unique intersection of aviation security, political expression, and technical creativity, highlighting the unexpected ways that technology vulnerabilities can be exploited in the modern era.
Comments
Please log in or register to join the discussion