A new AI-powered tool that identifies exposed cloud files and sensitive data leaks has achieved a Proof of Usefulness score of 13, helping organizations prevent breaches through automated risk classification.
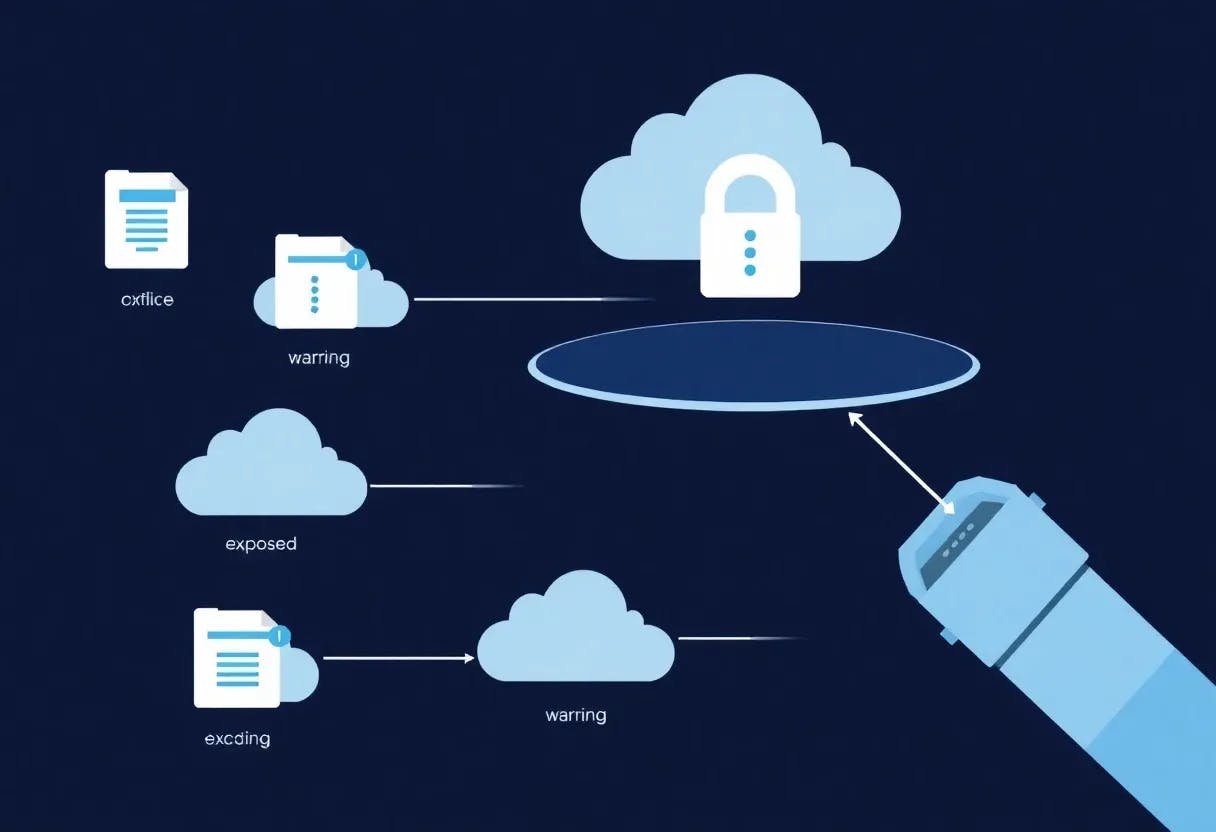
Nishant Kumar's AI Security Exposure Detector has earned a notable Proof of Usefulness score of 13 in HackerNoon's ongoing hackathon. This web-based solution addresses a critical gap in cloud security by automatically scanning public cloud storage systems for misconfigured files and sensitive data exposures.
The tool operates by analyzing publicly accessible cloud storage links, using machine learning to classify data types and assign risk scores based on sensitivity. Users receive actionable security reports highlighting vulnerabilities like unprotected customer databases or exposed API keys. With cloud storage misconfigurations causing over 15% of data breaches according to industry reports, Kumar's timing addresses an urgent need for automated monitoring.
Currently in beta testing, the platform serves developers, security teams, and small businesses lacking dedicated security resources. Early adopters are validating its core functionality through real-world scans, with Kumar prioritizing feature development based on their feedback. The integration with Bright Data enables comprehensive web scraping to identify exposed data across multiple platforms.
What distinguishes Kumar's approach is its practical focus. Rather than theoretical security models, the detector emphasizes immediate utility: 'It delivers tangible value by helping users make faster, safer decisions through AI-powered insights,' he explains. The 13-point usefulness score reflects its capacity to convert raw data into preventive actions.
As cloud adoption accelerates, tools bridging AI and security operations show significant potential. Kumar's solution demonstrates how targeted automation can mitigate human configuration errors – currently the origin of most cloud data leaks. With continuous refinement driven by user input, the detector represents an evolving approach to proactive data protection.
Explore the full technical assessment of Kumar's tool.
Comments
Please log in or register to join the discussion