The Aisuru botnet has set a new DDoS record with a 31.4 Tbps attack targeting telecommunications providers, highlighting the growing threat of hyper-volumetric attacks and the critical need for robust mitigation strategies.
The Aisuru botnet has shattered previous records by launching a massive distributed denial of service (DDoS) attack that peaked at 31.4 terabits per second and 200 million requests per second, marking the largest DDoS attack ever publicly disclosed. The attack, which occurred on December 19, 2025, was part of a coordinated campaign dubbed "The Night Before Christmas" that specifically targeted telecommunications service providers and IT organizations.
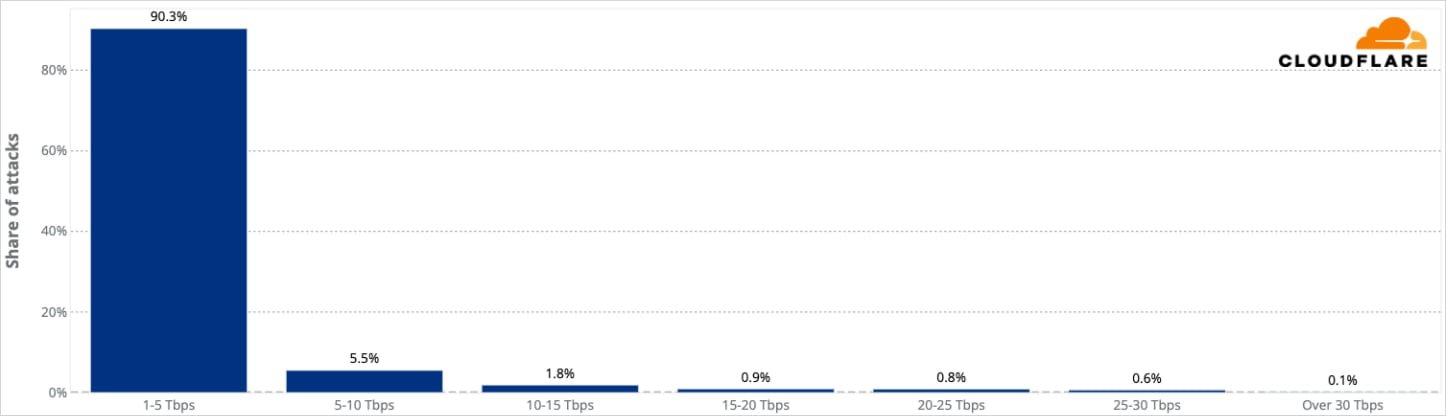
This latest assault surpasses Aisuru's own previous record of 29.7 Tbps set earlier in 2025 and demonstrates the rapidly escalating scale of DDoS threats facing organizations worldwide. Cloudflare, which detected and mitigated the attack, characterized it as an "unprecedented bombardment" on critical infrastructure providers.
The Growing Scale of Aisuru Attacks
Aisuru has established itself as one of the most formidable DDoS threats in recent years. The botnet was responsible for another massive attack in 2025 that peaked at 15.72 Tbps and originated from 500,000 IP addresses, according to Microsoft's attribution. The botnet's power stems from compromised IoT devices and routers, though Cloudflare noted that the December attacks specifically utilized Android TVs as attack sources.
What makes these hyper-volumetric attacks particularly concerning is their brevity and intensity. According to Cloudflare's analysis, more than half of the attacks in the Aisuru campaign lasted between one and two minutes, with only 6% taking longer than that. Despite their short duration, these attacks deliver devastating impact through concentrated bursts of traffic.
2025: A Record Year for DDoS Activity
The Aisuru campaign is part of a broader trend that saw DDoS attacks increase by 121% in 2025 compared to the previous year, with Cloudflare recording 47.1 million incidents throughout the year. The company mitigated an average of 5,376 DDoS attacks per hour, with 73% being network-layer attacks and the remainder HTTP-based.

Q4 2025 showed particularly concerning growth, with a 31% quarter-over-quarter increase and 58% year-over-year growth in DDoS activity. This sustained upward trajectory indicates that organizations cannot afford to become complacent about DDoS protection.
Industry Impact and Geographic Distribution
The telecommunications sector bore the brunt of DDoS attacks in Q4 2025, followed by IT and services firms, gambling and casinos, and gaming companies. The geographic distribution of attacks revealed interesting patterns, with Bangladesh emerging as the largest source of DDoS attacks, followed by Ecuador and Indonesia. Argentina jumped to fourth place while Russia dropped five positions to number 10.
From the victim perspective, organizations in China, Hong Kong, Germany, Brazil, and the United States were the most targeted countries during the quarter. This global distribution underscores the borderless nature of DDoS threats and the need for international cooperation in addressing them.
The Botnet Problem
Cloudflare's report highlighted a particularly troubling statistic: more than 71.5% of all recorded HTTP DDoS attacks in 2025 came from known and documented botnets. This concentration of attacks from established botnet infrastructure suggests that while new botnets like Aisuru continue to emerge, existing botnets remain highly effective and active.
The report also noted a 600% increase in network-layer attacks exceeding 100 million packets per second and a 65% quarter-over-quarter increase in attacks larger than 1 Tbps. These metrics demonstrate the arms race between attackers developing more powerful botnets and defenders implementing more sophisticated mitigation techniques.
Implications for Organizations
For organizations, particularly those in the telecommunications and IT services sectors, the Aisuru attacks serve as a wake-up call about the evolving DDoS threat landscape. The ability of these attacks to overwhelm infrastructure with terabit-scale traffic, even for short durations, can cause significant disruption to services and damage to reputation.
Cloudflare noted that despite the scale of these hyper-volumetric attacks, they were detected and mitigated automatically without triggering internal alerts. This highlights the importance of having robust, automated DDoS protection in place that can respond to threats faster than human operators can react.
Organizations should review their DDoS mitigation strategies, ensuring they have adequate bandwidth, filtering capabilities, and response procedures in place. The concentration of attacks from known botnets also suggests that threat intelligence sharing and collaborative defense efforts could be particularly effective in combating these threats.
The Aisuru botnet's record-breaking attack represents not just a technical milestone but a clear signal that DDoS attacks are becoming more powerful, more frequent, and more targeted. As attackers continue to innovate and compromise new types of devices, organizations must remain vigilant and proactive in their defensive measures.

Comments
Please log in or register to join the discussion