The AMOS infostealer is targeting macOS users through poisoned AI app extensions, demonstrating how cybercriminals weaponize trusted platforms and emerging technologies to harvest credentials at scale.

Security researchers have uncovered a sophisticated campaign distributing the Atomic macOS Stealer (AMOS) through compromised extensions for OpenClaw, a popular AI assistant platform. Dubbed ClawHavoc by Koi Security analysts, this operation exploits OpenClaw's skill marketplace to distribute malicious extensions disguised as legitimate tools—including cryptocurrency utilities, productivity enhancers, and YouTube integrations. Once installed, these extensions deploy AMOS to harvest Keychain passwords, browser sessions, crypto wallet data, and SSH keys.
"Infostealers like AMOS aren't standalone malware—they're data collection engines feeding a sprawling underground economy," explains Flare's threat intelligence team in their 2026 Enterprise Infostealer Identity Exposure Report. "Attackers continuously adapt to technology trends, abusing trusted platforms to trick users into executing malware themselves."
Evolution of a Persistent Threat
AMOS first surfaced in May 2023 on Telegram channels, advertising macOS-specific data theft capabilities for $1,000/month subscriptions paid in cryptocurrency. 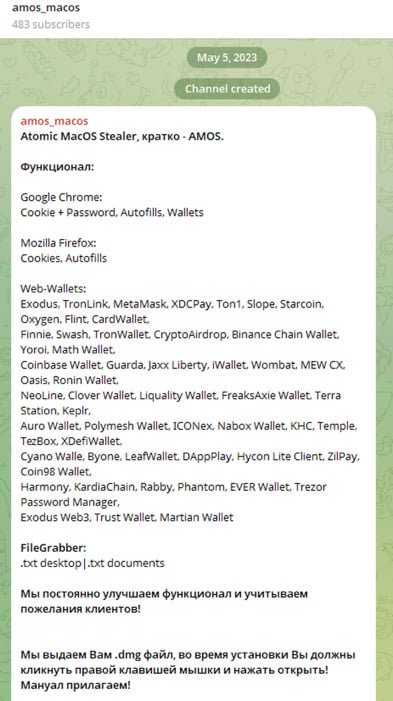 demonstrates its advertised features, including system information extraction and Telegram-based command control. Since then, AMOS has evolved into a persistent threat with multiple dissemination vectors:
demonstrates its advertised features, including system information extraction and Telegram-based command control. Since then, AMOS has evolved into a persistent threat with multiple dissemination vectors:
- AI Ecosystem Exploitation: Beyond ClawHavoc, AMOS operators used ChatGPT's shared chat feature in late 2025 to host fake installation guides for a "ChatGPT Atlas browser," leveraging OpenAI's domain credibility to trick users into executing malicious terminal commands.
- Brand Impersonation: A recent campaign impersonated LastPass through fraudulent GitHub repositories, using SEO poisoning to push victims toward terminal-based execution scripts. Attackers automate repository creation to maintain persistence.
- Traditional Social Engineering: Fake installers for popular software (Photoshop, Microsoft Office) distributed via malvertisements on search engines, coupled with "ClickFix" techniques where users paste malicious commands into Terminal.
The Industrialized Cybercrime Pipeline
AMOS operates on a Malware-as-a-Service model:
- Developers maintain the stealer platform ($1k/month subscriptions)
- Distributors create lures (malvertising, poisoned extensions)
- Log Buyers purchase stolen credentials for follow-on attacks
Flare researchers note: "Unlike traditional malware focused on persistence, infostealers prioritize speed and data coverage. The resulting logs become commodities sold to access brokers for account takeovers, ransomware deployment, or crypto theft—making AMOS a foundational layer in the cybercrime supply chain."
Protection Strategies for macOS Users
- Verify Marketplace Items: Before installing AI extensions, confirm developer legitimacy through official channels. OpenClaw has since strengthened marketplace vetting.
- Terminal Command Scrutiny: Never paste commands from unverified sources. macOS's
curl | bashpatterns are frequently abused. - Credential Management: Use hardware security keys or dedicated password managers with local-only encryption options. Regularly rotate high-value credentials.
- Monitor for Exposure: Services like Flare's free trial track stealer logs on dark web markets, alerting organizations to compromised credentials before attackers weaponize them.
- Installation Sources: Download software exclusively from official vendors or App Store. Browser extensions should be validated on developer portals like Chrome Web Store or Firefox Add-ons.
As Flare's report concludes: "The asymptotic adaptability of distributors—continuously refining social engineering around trends like AI—makes user education the critical defense layer. Organizations must assume credential exposure and prioritize rapid detection."

Comments
Please log in or register to join the discussion