Cross-subscription Azure PostgreSQL Flexible Server deployments face Private Endpoint approval failures due to resource provider gaps, requiring coordinated subscription-level configuration.
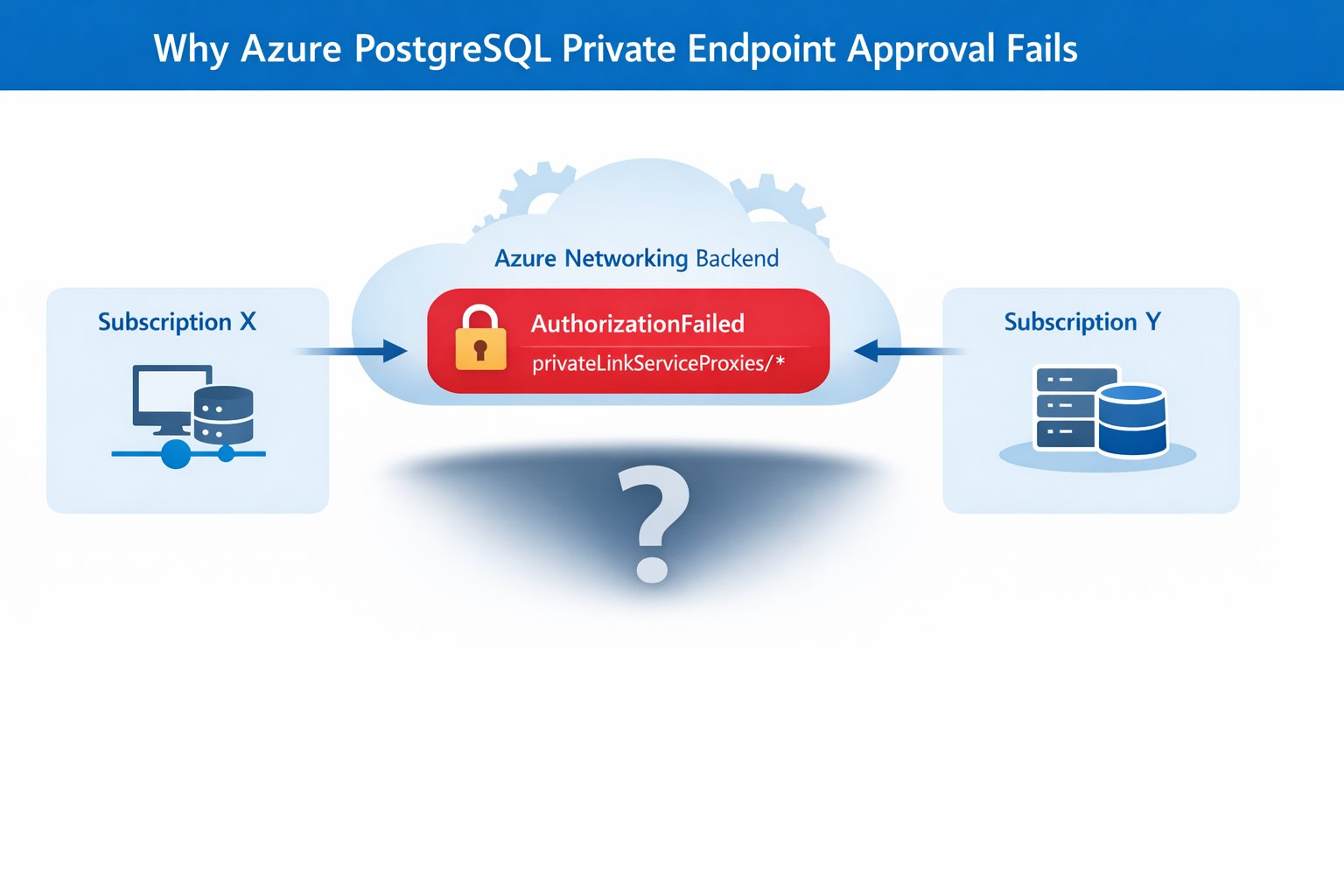
Organizations implementing Azure Database for PostgreSQL Flexible Server across multiple subscriptions or tenants encounter persistent Private Endpoint approval failures – a configuration hurdle causing significant deployment delays. These failures manifest as perpetually pending connections, silent approval reversals, and misleading "No Access" errors despite correct RBAC permissions. The core issue stems from Azure's backend authorization requirements during Private Link establishment, demanding specific subscription-level configurations often overlooked in multi-subscription architectures.
Authorization Failure Mechanics
When approving Private Endpoints for PostgreSQL Flexible Server, Azure performs dual operations:
- Service Provider Side: PostgreSQL resource approval initiation
- Consumer Side: Private Link Service Proxy update on the Private Endpoint resource
The critical failure point occurs during step 2 when the Private Endpoint resides in a separate subscription or tenant. Azure requires:
- Registered Resource Providers: Both
Microsoft.NetworkandMicrosoft.DBforPostgreSQLmust be activated in both subscriptions (Resource Provider documentation) - Network Write Permissions: Approving identities need
Microsoft.Network/privateEndpoints/privateLinkServiceProxies/writerights on the Private Endpoint scope
Without these, authorization errors like AuthorizationFailed: The client '<object-id>' does not have authorization... appear despite correct PostgreSQL permissions. This differs from services like Azure Key Vault, which have simpler approval workflows.
Resolution Protocol
| Step | Action | Verification Method |
|---|---|---|
| 1 | Register Microsoft.Network & Microsoft.DBforPostgreSQL in both subscriptions |
Azure Portal > Subscriptions > Resource providers |
| 2 | Assign Network Contributor role to approver identity on Private Endpoint scope | Access Control (IAM) blade |
| 3 | Refresh authentication tokens | Sign out/in of Azure Portal/Azure CLI |
Post-correction, Private Endpoints transition from Pending to Approved within minutes without retry errors.
Strategic Prevention Framework
- Landing Zone Pre-Registration: Automate provider registration via Azure Policy or Terraform in management groups
- Cross-Subscription Readiness Checklist:
- Validate provider registrations
- Verify network permissions matrix
- Test approval workflow before production deployment
- Service-Specific Documentation: Note PostgreSQL's dual-operation requirement differs from other Azure services (Private Endpoint comparisons)
Business Impact Analysis
Unresolved approval failures cause:
- 48+ hour troubleshooting cycles for network/DB teams
- Project delays during critical migration phases
- Resource dependency deadlocks in CI/CD pipelines
Financial implications include wasted engineering hours and delayed application deployments. A financial services client reduced Private Endpoint deployment time from 72 hours to 15 minutes after implementing provider registration automation.
Architectural Recommendations
- Treat subscription resource providers as foundational infrastructure
- Implement cross-subscription permission audits during tenant onboarding
- Use service principals with predefined roles for approval workflows
- Monitor Private Endpoint state transitions via Azure Monitor alerts
Proactive configuration prevents opaque authorization errors that traditionally require Microsoft Support intervention. Enterprises managing complex Azure environments should prioritize these checks before implementing Private Link for PostgreSQL or other database services across subscription boundaries.
References:

Comments
Please log in or register to join the discussion