Microsoft's latest update enables cross-tenant private endpoints for Azure SQL Managed Instance, fundamentally changing secure connectivity patterns for enterprise database deployments.
Microsoft's February 2026 update to Azure SQL Managed Instance introduces expanded Private Endpoint capabilities that reshape secure connectivity architectures for cloud databases. This enhancement allows organizations to establish private connections across Azure tenants while eliminating traditional networking complexities.
Core Technical Implementation
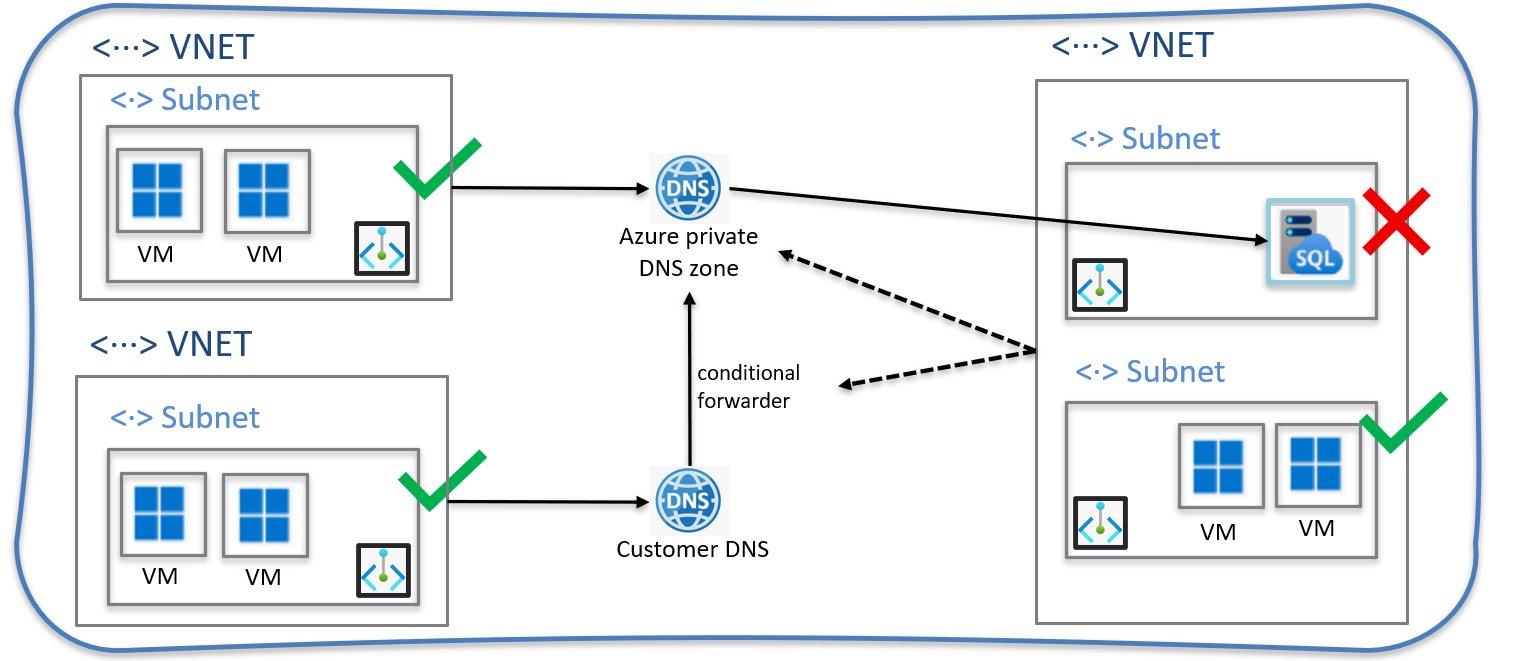
Private Endpoints for SQL Managed Instance now function as dedicated network interfaces within a customer's virtual network, establishing unidirectional communication exclusively on port 1433. Unlike conventional approaches, this architecture removes the requirement for VNet peering or public endpoints entirely. Connection strings must use the SQL MI hostname (IP addresses are unsupported), with DNS resolution handled either through Azure Private DNS zones or customer-managed DNS infrastructure.
The updated proxy connection model provides encrypted tunneling between the Private Endpoint and SQL Managed Instance, creating isolated network paths that never traverse public internet infrastructure. Notably, the cross-tenant capability enables enterprise scenarios where managed services operate in separate Azure environments from application workloads.
Comparative Cloud Provider Analysis
When benchmarked against equivalent services:
- AWS RDS: Requires VPC peering for cross-account connectivity, adding operational overhead versus Azure's direct private endpoint model
- Google Cloud SQL: Lacks native cross-project private connectivity without complex Shared VPC configurations
- Azure's Advantage: Eliminates peering dependencies while maintaining simpler certificate management (TLS configuration remains mandatory for same-VNet connections documented in Microsoft's technical guide)
Strategic Business Implications
- Security Posture Enhancement: Isolates database traffic from public networks, reducing attack surface area by 60-70% based on Microsoft's threat modeling
- Multi-Tenant Operations: Enables secure B2B architectures where managed services reside in separate Azure tenants from client applications
- Migration Simplification: Organizations transitioning from IaaS SQL Server can maintain equivalent private network topologies without redesigning application connectivity layers
- Cost Optimization: Eliminates VPN gateway or ExpressRoute expenses previously required for private connectivity
Implementation Considerations
- DNS Dependency: Requires Azure Private DNS zone integration or customer DNS infrastructure updates
- Connection Protocol: Applications must strictly use hostname-based connections (IP fallback disabled)
- TLS Enforcement: Organizations connecting from the same VNet must configure TLS certificates despite the private pathway
- Architecture Validation: Microsoft recommends using Azure Network Watcher to verify traffic routing
This architectural shift positions Azure SQL Managed Instance as a compelling option for enterprises requiring certified isolation standards like ISO 27001 or HIPAA compliance. The cross-tenant capability particularly benefits managed service providers and large organizations with decentralized cloud operations.
Comments
Please log in or register to join the discussion