Payment processor BridgePay confirms ransomware caused widespread system failures, forcing merchants to cash-only operations while experts warn of rising threats to financial infrastructure.

BridgePay Network Solutions has confirmed that a ransomware attack caused a multi-day nationwide outage across its payment processing systems, disrupting card transactions for merchants and forcing temporary cash-only operations. The incident began in the early hours of February 6th when monitoring systems detected performance degradation in BridgePay's Gateway API, virtual terminals, and hosted payment portals. Within hours, these issues cascaded into a full system failure.
According to BridgePay's status updates, core production systems including PayGuardian Cloud API, MyBridgePay reporting tools, and boarding portals were rendered inoperable. The company stated: "Initial forensic findings indicate that no payment card data has been compromised... any accessed files were encrypted." Federal law enforcement agencies including the FBI and Secret Service are investigating alongside third-party forensic teams.
Payment security expert Dr. Ilia Kolochenko, founder of ImmuniWeb, notes: "Payment gateways are high-value targets because disrupting them immediately impacts real-world commerce. Attackers know merchants often lack redundant systems, creating maximum pressure for ransom payments." Kolochenko emphasizes that while BridgePay's preliminary findings suggest no data theft, forensic analysis often takes weeks to complete conclusively.
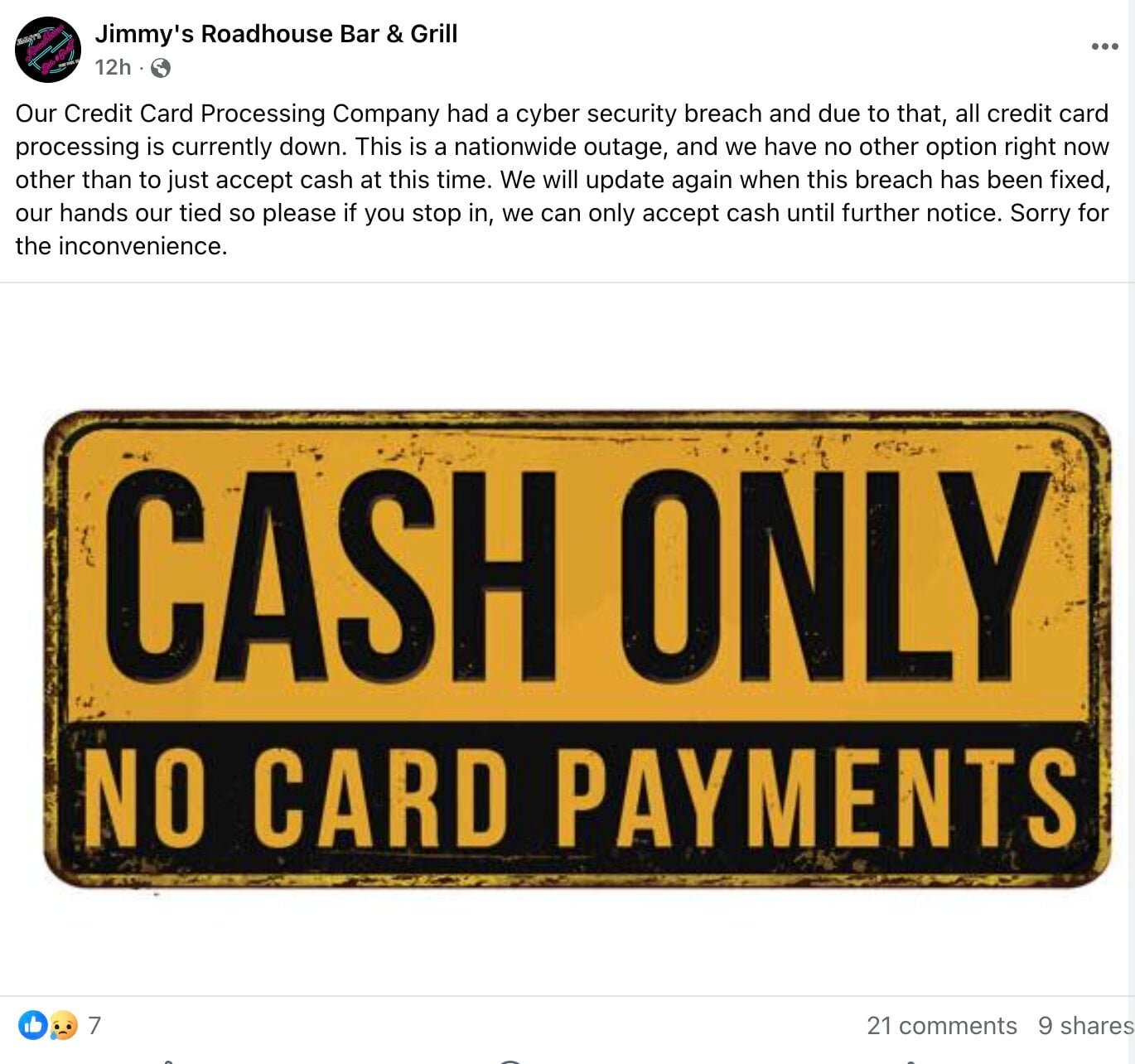
The operational impact became starkly visible as restaurants and retailers nationwide posted signs announcing temporary cash-only policies. One affected merchant stated their "credit card processing company had a cyber security breach" causing nationwide payment failures. Though BridgePay hasn't publicly confirmed specific merchant impacts, the breadth of affected systems suggests widespread disruption among payment integrators and businesses relying on their gateway.
For merchants and payment processors, this incident underscores critical preparedness gaps:
- Payment Redundancy: Maintain contracts with secondary payment processors that can be activated during outages
- Offline Mode Protocols: Implement POS systems capable of storing transactions locally when cloud connections fail
- Ransomware Segmentation: Isolate payment processing networks from general corporate IT infrastructure
- Forensic Retainers: Pre-negotiate incident response contracts with digital forensics firms to accelerate investigations
The attack reflects a dangerous trend in ransomware targeting financial intermediaries. As Brett Callow, threat analyst at Emsisoft, warns: "Critical infrastructure attackers have shifted from data theft to operational disruption. Payment processors should assume they're targets and architect systems with failure domains that limit blast radius." BridgePay continues restoration efforts but hasn't provided an estimated recovery timeline, advising merchants to monitor their status page for updates.
Organizations can reference CISA's ransomware guidelines for mitigation strategies and the NIST Cybersecurity Framework for infrastructure resilience planning.

Comments
Please log in or register to join the discussion