Microsoft Defender Researchers have identified a sophisticated new ClickFix variant ('CrashFix') combining browser crashes with social engineering to deploy Python-based remote access trojans, marking a significant shift in attacker tradecraft toward living-off-the-land techniques.

Microsoft's security team has uncovered a dangerous evolution in browser-based attacks with the CrashFix malware variant, demonstrating how threat actors are increasingly blending social engineering with legitimate system tools to bypass traditional defenses. This attack chain represents a strategic shift toward multi-phase compromises that leverage both cloud infrastructure and on-premise utilities.
Technical Breakdown: From Browser Crash to Domain Join Detection
The attack begins with a clever abuse of browser ecosystems: 
- Malicious Extension Delivery: Attackers poison search results for ad blockers, redirecting to the official Chrome Web Store to install a malicious extension masquerading as uBlock Origin Lite
- Delayed Execution: The payload activates hours/days later, crashing browsers via infinite loops before displaying fake error messages
- Living-off-the-Land Escalation: Uses renamed finger.exe (Windows utility) to fetch PowerShell scripts from attacker-controlled IPs
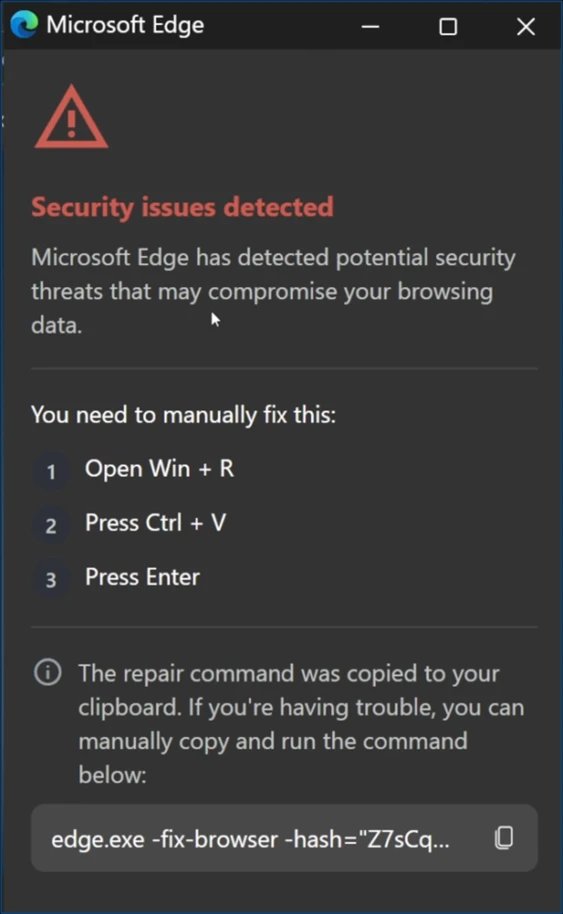
What makes CrashFix particularly concerning for cloud environments:
- Python RAT Deployment: Downloads portable WinPython distributions (WPy64-31401) to ensure cross-system compatibility
- Conditional Payloads: Only deploys full RAT capabilities on domain-joined machines, indicating enterprise targeting
- Dropbox Abuse: Uses legitimate cloud storage for payload delivery (extensions.py)
Comparative Analysis: Cloud Defense Considerations
| Defense Layer | Traditional Malware | CrashFix Approach | Protection Strategy |
|---|---|---|---|
| Initial Infection | Exploit kits | Browser extension abuse | Web protection + extension vetting |
| Payload Delivery | Direct binary downloads | PowerShell + Python bundles | Script monitoring |
| Persistence | Registry modifications | Scheduled tasks + Run keys | Behavioral detection |
| C2 Communication | Dedicated malware servers | Blend with cloud services | Egress filtering |
Business Impact: Multi-Cloud Security Implications
- Extended Attack Surface: Abuse of Dropbox and Web Store platforms complicates perimeter defense
- Detection Challenges: Python-based payloads often bypass signature-based AV solutions
- Credential Risks: Extensive reconnaissance targets cloud identity systems
Microsoft recommends:
- Enabling Defender for Endpoint EDR in block mode
- Implementing ASR rules against script-based attacks
- Restricting legacy utilities like finger.exe through network protection
Strategic Recommendations
- Cloud Workload Protection: Monitor Python execution in containerized environments
- Identity Hygiene: Enforce MFA across all cloud services
- Browser Isolation: Consider remote browsing solutions for high-risk activities
This attack demonstrates how modern threats bridge on-premise and cloud environments, requiring defense strategies that address both legacy system utilities and modern cloud services simultaneously.

Comments
Please log in or register to join the discussion