Attackers are actively exploiting an unauthenticated API vulnerability in SmarterMail that allows full admin account takeover, with evidence showing exploitation began within days of patching.

Security researchers confirm active exploitation of an authentication bypass vulnerability in SmarterMail, SmarterTools' email and collaboration platform. The flaw enables unauthenticated attackers to reset administrator passwords and gain complete control over email servers, with evidence showing attacks began just two days after the vendor released patches.
Vulnerability Mechanics
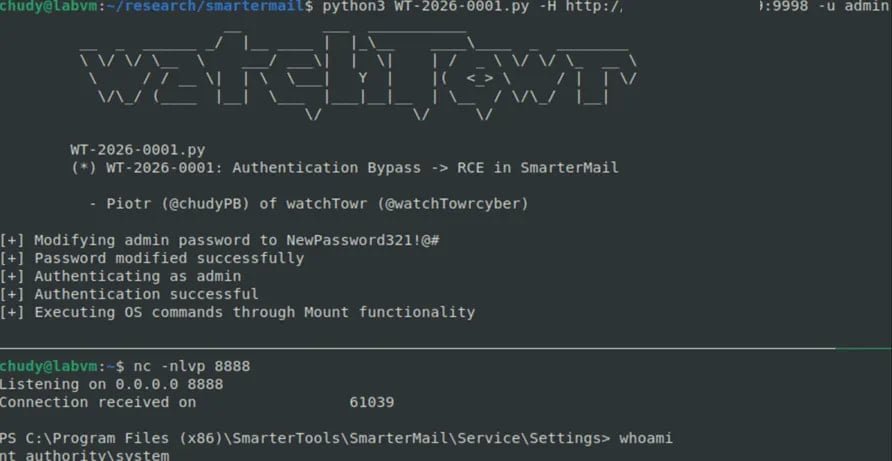
The vulnerability resides in the force-reset-password API endpoint, which improperly exposes administrative functions without authentication controls. According to researchers at watchTowr Labs, attackers can send specially crafted JSON requests containing the "IsSysAdmin": true parameter. Crucially, the system executes privileged password resets without:
- Verifying the attacker's identity
- Validating the existing password (despite an
OldPasswordfield in the request) - Implementing any authorization checks
"This allows anyone who knows or guesses an admin username to forcibly reset the password and assume complete control of the account," explained a watchTowr researcher familiar with the investigation. Unlike regular user accounts, this exploit exclusively targets administrative-level credentials.
Active Exploitation Timeline
The vulnerability follows a concerning exploitation pattern:
- January 8, 2026: watchTowr discloses flaw to SmarterTools
- January 15: SmarterTools releases Build 9511 patch (no CVE assigned)
- January 17: First evidence of in-the-wild exploitation appears
Researchers confirmed active attacks after analyzing server logs provided by an anonymous victim. The logs showed clear targeting of the vulnerable endpoint:
 Caption: Server logs showing exploitation attempts targeting the vulnerable endpoint (Source: watchTowr)
Caption: Server logs showing exploitation attempts targeting the vulnerable endpoint (Source: watchTowr)
"We observed attackers reverse-engineering the patch within 48 hours of its release," the watchTowr team noted. "The speed suggests threat actors either independently discovered the flaw or quickly analyzed the patch to recreate the exploit."
Critical Impact
Compromised admin accounts grant attackers alarming privileges:
- Full control over email services (SMTP/IMAP/POP)
- Access to calendars, contacts, and collaboration data
- Ability to execute operating system commands
- Complete remote code execution on host systems
SmarterMail is widely deployed by managed service providers (MSPs), hosting companies, and SMBs, with SmarterTools reporting over 15 million users across 120 countries. This broad install base makes the flaw particularly dangerous.
Mitigation and Best Practices
Immediate Patching: Upgrade to SmarterMail Build 9511 immediately (download here). This version addresses both this auth bypass and a separate pre-authentication RCE flaw (CVE-2025-52691) discovered earlier.
Credential Rotation: All administrative accounts should reset passwords immediately—even on patched systems—as previous credentials may be compromised.
API Monitoring: Monitor logs for unusual access patterns to
/force-reset-passwordendpoints. watchTowr has published detection signatures based on observed attack patterns.Network Segmentation: Restrict web management interfaces to dedicated admin VLANs or VPN-access only.
"This incident underscores how quickly unauthenticated vulnerabilities get weaponized," emphasized a security architect specializing in email infrastructure. "Administrators of self-hosted solutions like SmarterMail must prioritize patch deployment timelines measured in hours—not days—especially when privileged access is at stake."
SmarterTools has not assigned a CVE identifier for this vulnerability despite its critical nature and active exploitation status. Administrators should treat this with equivalent urgency to critical CVSS-rated flaws.

Comments
Please log in or register to join the discussion