Gartner's new Exposure Assessment Platforms category marks a fundamental shift from traditional vulnerability management to continuous threat exposure management, focusing on attack paths rather than isolated CVEs.
Gartner's introduction of the Exposure Assessment Platforms (EAP) category represents a formal admission that traditional Vulnerability Management (VM) is no longer a viable way to secure a modern enterprise. This shift from the Market Guide for Vulnerability Assessment to the Magic Quadrant for EAPs moves away from the "vulnerability hose"—the endless stream of CVEs—and toward a model of Continuous Threat Exposure Management (CTEM).
The move addresses a critical problem that has plagued security teams for a decade: the "Dead End" paradox. Data from over 15,000 environments shows that 74% of identified exposures are "dead ends," existing on assets with no viable path to critical systems. In the old model, security teams might spend 90% of remediation effort fixing these dead ends, yielding effectively zero reduction in risk to business processes.
Why Exposure Assessment Is Gaining Ground
Security tools have historically promised risk reduction but mostly delivered noise. One product reveals a misconfiguration, another logs privilege drift, a third flags vulnerable external-facing assets. The result is a crisis of volume leading to chronic alert fatigue in the SOC. Each tool provides a piece of the puzzle, yet none were able to put all the pieces together and explain how exposure forms or what to fix first to avoid it.
EAPs are designed to address this by pulling all those pieces into a unified view that tracks how systems, identities, and vulnerabilities interact in real environments. They show how an attacker could actually use these conditions to move from a low-risk dev environment to critical assets.
This model gains traction because it reflects how attackers operate. Threat actors don't limit themselves to a single flaw. They exploit weak controls, misaligned privileges, and blind spots in detection. The EAP model tracks how exposures accumulate across environments and lead attackers to reachable assets.
Gartner projects that organizations using this approach will reduce unplanned downtime by 30% by 2027. This dramatic outcome is based on an equally dramatic change in how exposure is defined, modeled, and operationalized across environments.
From Static Lists to Exposure in Motion
The shift in workflow begins with how EAPs detect and connect the conditions that lead to risk. Exposure assessment platforms take a fundamentally different approach than traditional vulnerability tools, built around distinct capabilities:
They consolidate discovery across environments. EAPs continuously scan internal networks, cloud workloads, and user-facing systems to identify both known and untracked assets, alongside unmanaged identities, misconfigured roles, and legacy systems that may not appear in standard inventories.
They prioritize based on context, not just severity. Exposure is ranked using multiple parameters—asset importance, access paths, exploitability, and control coverage. This allows teams to see which issues are reachable, which are isolated, and which enable lateral movement.
They integrate exposure data into operational workflows. EAP output is designed to support action. Platforms connect with IT and security tools so findings can be assigned, tracked, and resolved through existing systems—without waiting for a quarterly audit or manual review.
They support lifecycle tracking. Once exposures are identified, EAPs monitor them across remediation steps, configuration changes, and policy updates. That visibility helps teams understand what's been fixed, what remains, and how each adjustment affects risk posture.
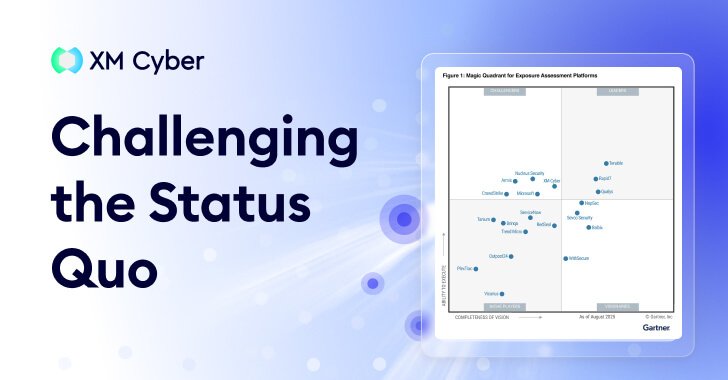
What the Magic Quadrant Reveals About Market Maturity
The new Magic Quadrant highlights a split in the market. On one side, you have legacy incumbents attempting to "bolt on" exposure features to their existing scanning engines. On the other, you have native Exposure Management players who have been modeling attacker behavior for years.
The maturity of the category is evidenced by a shift in the "definition of done." Success is no longer measured by how many vulnerabilities were patched, but by how many critical attack paths were eliminated. Platforms like XM Cyber, which were built on attack graph-based modeling, are now leading the way for this approach.
Practical Implications for Security Teams
Exposure assessment now stands as its own category, with defined capabilities, evaluation criteria, and a growing role in enterprise workflows. The platforms in the Magic Quadrant are identifying connected exposures, mapping which assets can be reached, and guiding remediation based on attacker movement.
For the practitioner, the immediate value is efficiency. These platforms are making decisions about what to fix first, how to assign ownership, and where risk reduction will have the most impact.
The key insight is that exposure assessment is now positioned as a core layer in how environments are secured, maintained, and understood. If you can mathematically prove that 74% of your alerts can be safely ignored, you aren't just "improving security"—you're returning time and resources to a team that is likely already at its breaking point.
The EAP category is finally aligning security metrics with business reality. The question is no longer "How many vulnerabilities do we have?" but "Are we safe from the attack paths that matter?"
What This Means for Your Security Strategy
When evaluating exposure assessment platforms, security teams should focus on several key capabilities:
- Attack path modeling: Can the platform show how exposures connect across your environment to create viable attack routes?
- Context-aware prioritization: Does it factor in asset criticality, exploitability, and control coverage rather than just CVSS scores?
- Integration with existing workflows: Can findings be pushed to your ticketing systems, SIEM, or SOAR platforms?
- Continuous monitoring: Does it provide ongoing visibility into how exposures evolve as your environment changes?
- Remediation guidance: Does it offer actionable steps to break attack paths rather than just listing vulnerabilities?
The Business Impact
The shift to exposure assessment represents more than a technical evolution—it's a business imperative. Traditional vulnerability management has become mathematically impossible to complete in modern, dynamic environments. The average enterprise manages thousands of assets across cloud and on-premises infrastructure, with identities, configurations, and vulnerabilities constantly changing.
EAPs address this by focusing on what actually matters: the attack paths that could lead to a breach. By eliminating 74% of "dead end" remediation efforts, organizations can redirect resources toward fixing the exposures that truly matter.
This approach also aligns security metrics with business outcomes. Instead of reporting on vulnerability counts, security teams can demonstrate risk reduction by showing eliminated attack paths and protected critical assets.
Looking Ahead
As the EAP category matures, we can expect several developments:
Increased integration with cloud-native security tools: As more organizations move to cloud-first architectures, EAPs will need to deeply integrate with cloud security posture management (CSPM) and cloud workload protection platforms (CWPP).
AI-enhanced attack path analysis: Machine learning will likely play a larger role in identifying novel attack paths and predicting how exposures might be exploited.
Regulatory alignment: As regulations like DORA and NIS2 emphasize risk-based approaches, EAPs will become essential for demonstrating compliance.
Convergence with other security functions: Exposure assessment will increasingly merge with threat intelligence, incident response, and security operations.

Conclusion
The introduction of the Exposure Assessment Platforms category by Gartner represents a watershed moment in cybersecurity. It acknowledges what practitioners have known for years: traditional vulnerability management is broken, and a new approach is needed.
EAPs offer a path forward by focusing on attack paths rather than isolated vulnerabilities, providing context-aware prioritization, and integrating with operational workflows. For security teams struggling with alert fatigue and impossible to-do lists, this shift offers hope of measurable risk reduction and more efficient use of limited resources.
The question is no longer whether to adopt exposure assessment, but how quickly organizations can make this transition. Those who embrace it will find themselves better equipped to protect their environments against modern threats, while those who cling to traditional approaches will continue to drown in noise and miss the exposures that truly matter.
This article was expertly written and contributed by Maya Malevich, Head of Product Marketing at XM Cyber.
Gartner Disclaimer: Gartner, Magic Quadrant for Exposure Assessment Platforms, By Mitchell Schneider, Dhivya Poole, and Jonathan Nunez, November 10, 2025. GARTNER is a registered trademark and service mark of Gartner, and Magic Quadrant is a registered trademark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and are used herein with permission. All rights reserved. Gartner does not endorse any vendor, product, or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.

Comments
Please log in or register to join the discussion