An IT worker's failed attempt to destroy an SSD with a drill left sensitive data intact and circulating in the market, highlighting critical gaps in data destruction procedures.
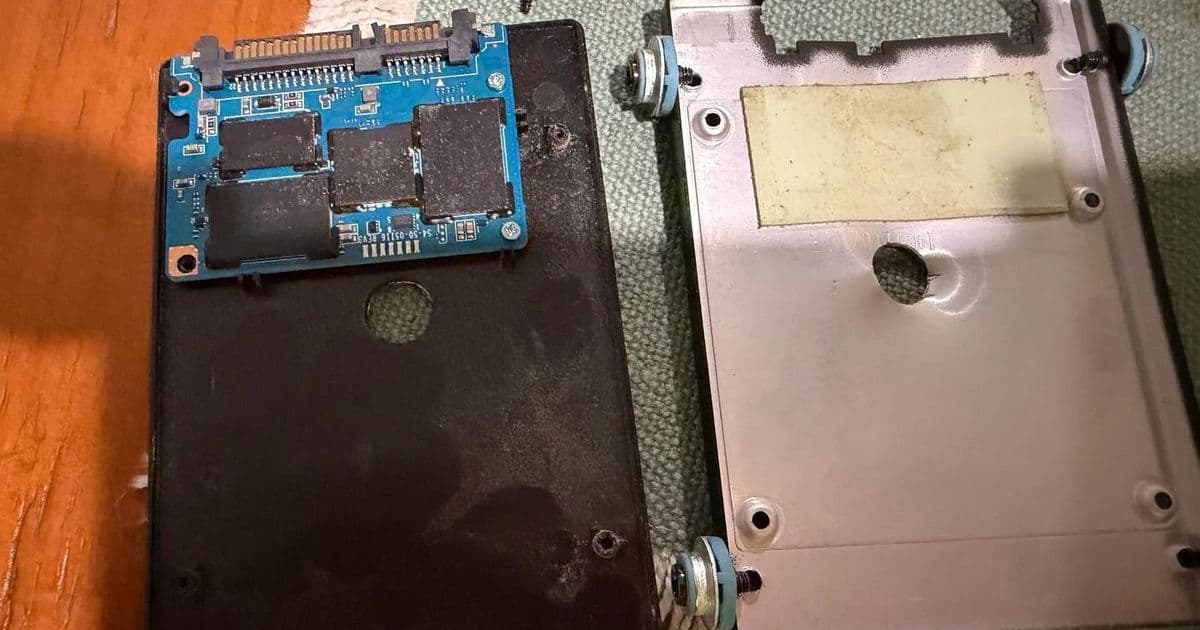
When an IT worker attempted to destroy a SATA SSD by drilling through it, the drive emerged virtually unscathed - and its data intact. This incident, which recently went viral on Reddit, serves as a stark reminder that modern storage destruction methods need updating for the SSD era.

The Anatomy of a Failed Destruction
The drive in question had a shorter PCB than traditional designs, causing the drill to miss the NAND chips entirely. This oversight left the storage medium functional and the data accessible - a serious security lapse for any organization handling sensitive information.
Drilling has long been a go-to method for destroying traditional hard drives, where a single hole through the platters effectively renders the device unusable. However, SSDs present unique challenges:
- Component placement: NAND chips are often distributed across the PCB, not concentrated in one area
- Smaller form factors: Modern drives have more compact layouts that can evade imprecise drilling
- Data persistence: Unlike HDDs, SSDs can sometimes retain data even with physical damage
Professional Destruction Alternatives
For organizations managing multiple drives, manual destruction quickly becomes impractical. Several professional solutions offer more reliable data destruction:
Automated destruction systems:
- DiskMantler uses targeted vibrations to destroy drives in 90 seconds
- Puncher P30 creates multiple perforations through the drive
- MediaGone 500 can process hundreds of SSDs, USB drives, and smartphones hourly
High-speed data wiping:
- NVMe Destroyinator wipes up to 16 M.2 SSDs simultaneously
- Achieves speeds up to 64 GB/s
- Eliminates physical destruction risks entirely
Best Practices for SSD Destruction
Organizations should update their data destruction procedures to account for SSD-specific vulnerabilities:
- Multiple targeting points: Drill through NAND chips and controller locations
- Physical verification: Inspect drives post-destruction to confirm effectiveness
- Alternative methods: Consider hammer destruction for internal components
- Professional services: Engage specialized destruction companies for large-scale operations
The Security Implications
This incident highlights a critical security gap. When sensitive data survives intended destruction, it can enter secondary markets - as happened here when the Redditor acquired the drive. While the finder had no malicious intent, the potential for data breaches remains significant.
The lesson is clear: proper data destruction requires understanding the technology being destroyed. What worked for decades with HDDs may be entirely ineffective against modern SSDs, potentially leaving organizations vulnerable to data exposure and compliance violations.
Comments
Please log in or register to join the discussion