Engineer discovers his sleep mask can access other users' EEG data due to hardcoded credentials in poorly secured software
An engineer's attempt to fix his smart sleep mask's connectivity issues uncovered a serious security flaw that allowed him to access other users' brainwave data in real-time. The incident highlights the growing problem of inadequate software security in consumer IoT devices.
The Discovery
AI engineer Aimilios Hatzistamou purchased a smart sleep mask from a small Chinese research company, likely the SLEEPU DreamPilot, through Kickstarter. When he encountered connection problems with the device, he took the approach any engineer would - he decided to reverse-engineer the Bluetooth protocol and Android application.
Using Claude Opus 4.6, Hatzistamou decompiled the Android app and discovered something alarming: hardcoded access credentials embedded in the application binary. These credentials were apparently shared across all copies of the app, creating a universal backdoor to the device's functionality.
How the Flaw Worked
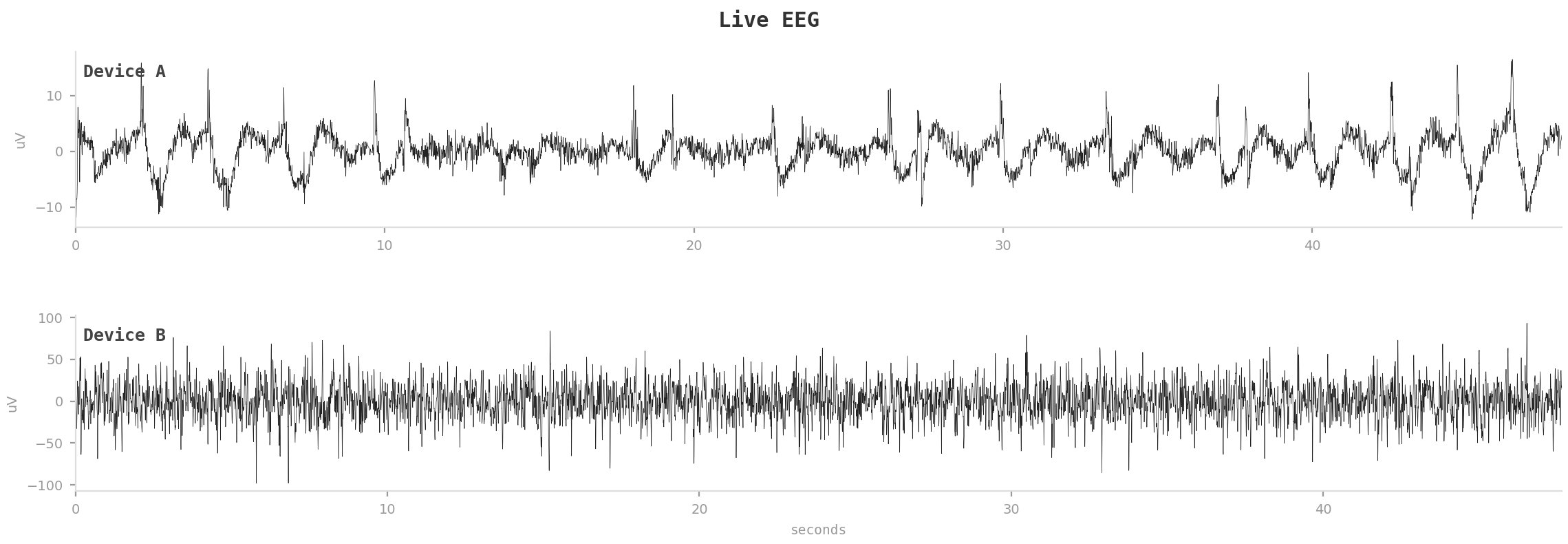
The sleep mask communicates with remote servers through MQTT services, using the hardcoded credentials for authentication. When Hatzistamou connected to these services with the discovered credentials, he gained access not only to his own device's data but to all connected masks using the same authentication.
During his investigation, he found approximately 25 masks were actively in use at that moment. More concerning, he could capture real-time EEG (electroencephalogram) readings from at least two other users somewhere in the world.
The Technical Details
The mask offers 15 different commands and functions that Hatzistamou and Claude were able to map out. These include:
- Sensor data retrieval
- Device control functions
- Electrical muscle stimulation (EMS) activation
Since the EMS feature can trigger electrical impulses through the mask, the security vulnerability potentially allowed unauthorized access to control this function on other users' devices.
The Broader Implications
This incident serves as yet another illustration of how software security is often treated as an afterthought in consumer IoT products. The use of hardcoded credentials is a well-known security anti-pattern that experienced developers typically avoid, yet it appears in numerous consumer devices.
Hatzistamou noted that as a developer himself, this situation doesn't appear to show malicious intent from the manufacturers. Instead, it demonstrates how low the bar has become for software development in consumer electronics, particularly for smaller companies or startups rushing products to market.
The case also highlights the risks of Kickstarter-funded hardware projects, where companies may lack the resources or expertise to implement proper security measures in their software development process.
Response and Resolution
Hatzistamou reported his findings to the company, despite actually being satisfied with the product overall. The incident underscores the importance of security researchers and ethical hackers in identifying vulnerabilities before they can be exploited maliciously.
This type of vulnerability could have been prevented through basic security practices such as:
- Unique device credentials instead of hardcoded ones
- Proper authentication mechanisms
- Regular security audits
- Secure software development lifecycle practices
As IoT devices become more prevalent in our homes and on our bodies, the need for robust security measures becomes increasingly critical. This sleep mask incident, while seemingly innocuous, could have been exploited for more nefarious purposes if discovered by malicious actors.

The case serves as a reminder that even seemingly simple consumer devices can contain sensitive personal data - in this case, brainwave patterns that could potentially reveal information about a user's mental state, sleep patterns, and other private information.
For consumers, this incident highlights the importance of researching the security practices of IoT device manufacturers before making purchases, particularly for devices that collect sensitive biometric data.

Comments
Please log in or register to join the discussion