The Python Software Foundation warns developers of an ongoing phishing campaign using a counterfeit PyPI website to steal credentials. Attackers are sending fake 'email verification' requests to package maintainers, aiming to compromise accounts and inject malware into legitimate Python libraries. This incident highlights escalating threats against open-source infrastructure and supply chain security.

Python developers are under targeted attack by threat actors operating a sophisticated phishing scheme impersonating the official Python Package Index (PyPI). According to an advisory from the Python Software Foundation, attackers are sending fraudulent "[PyPI] Email verification" messages from [email protected]—a domain deliberately mimicking PyPI's legitimate pypi.org address.
The Attack Mechanics
- Phishing Lure: Maintainers of PyPI packages received emails urging them to verify their email via a link, capitalizing on trust in PyPI's brand.
- Counterfeit Portal: The link directs victims to
pypj[.]org, a near-perfect replica of PyPI's login page designed to harvest credentials. - Credential Theft: Stolen credentials enable attackers to hijack developer accounts, potentially injecting malware into existing packages or uploading new malicious libraries to PyPI.
PyPI administrator Mike Fiedler emphasized, "This is not a security breach of PyPI itself, but rather a phishing attempt that exploits the trust users have in PyPI." The platform has since added a prominent warning banner to its homepage and is coordinating with CDN providers and domain registrars to dismantle the phishing infrastructure.
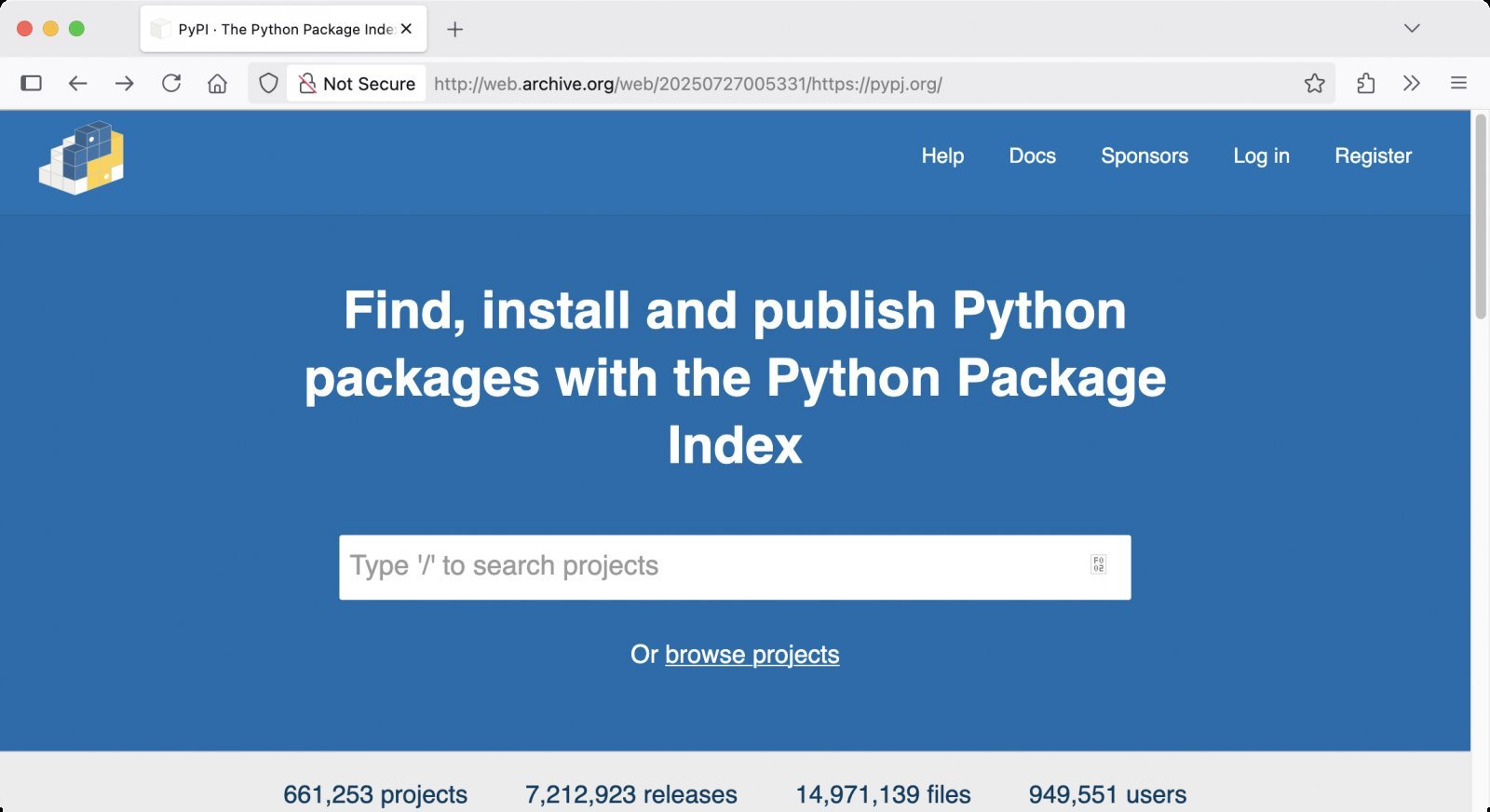 Fake PyPI phishing site (Source: BleepingComputer)
Fake PyPI phishing site (Source: BleepingComputer)
Immediate Mitigation Steps
- Delete Suspicious Emails: Any "verification" requests from
@pypj.orgshould be trashed immediately. - Password Reset: Compromised users must change PyPI passwords and enable two-factor authentication.
- Audit Accounts: Review Security History logs in PyPI accounts for unauthorized activity.
Broader Implications
This incident underscores persistent vulnerabilities in open-source ecosystems:
- Supply Chain Risks: Compromised maintainer accounts could lead to widespread malware distribution, echoing the March 2024 incident where PyPI halted new registrations after malicious package uploads.
- Trust Exploitation: Sophisticated lookalike domains (
pypj[.]orgvs.pypi[.]org) bypass traditional security awareness training. - Ecosystem Pressure: PyPI hosts over 500,000 packages, making it a high-value target. The foundation recently introduced "Project Archival" features to denote inactive projects, but credential security remains critical.
As Fiedler noted, the team is "waiting for CDN providers and name registrars to respond" to takedown requests. For developers, this attack is a stark reminder that vigilance extends beyond code—protecting foundational infrastructure demands equal rigor in identity management and threat detection. With software supply chains increasingly weaponized, the integrity of open-source repositories hinges on collective security hygiene.
Source: BleepingComputer

Comments
Please log in or register to join the discussion