Security researchers collected $439,250 in cash awards on the second day of Pwn2Own Automotive 2026, exploiting 29 unique zero-day vulnerabilities in electric vehicle chargers, in-vehicle infotainment systems, and car operating systems. The contest, held in Tokyo, Japan, has already awarded $955,750 for 66 zero-day exploits across two days, highlighting the growing attack surface in modern vehicles.
On the second day of Pwn2Own Automotive 2026, security researchers collected $439,250 in cash awards after exploiting 29 unique zero-days. The Pwn2Own Automotive hacking contest focuses on automotive technologies and takes place this week in Tokyo, Japan, from January 21 to January 23, during the Automotive World auto conference. Throughout the competition, security researchers target fully patched electric vehicle (EV) chargers, in-vehicle infotainment (IVI) systems, and car operating systems (e.g., Automotive Grade Linux).

The Exploit Landscape: What Was Hacked
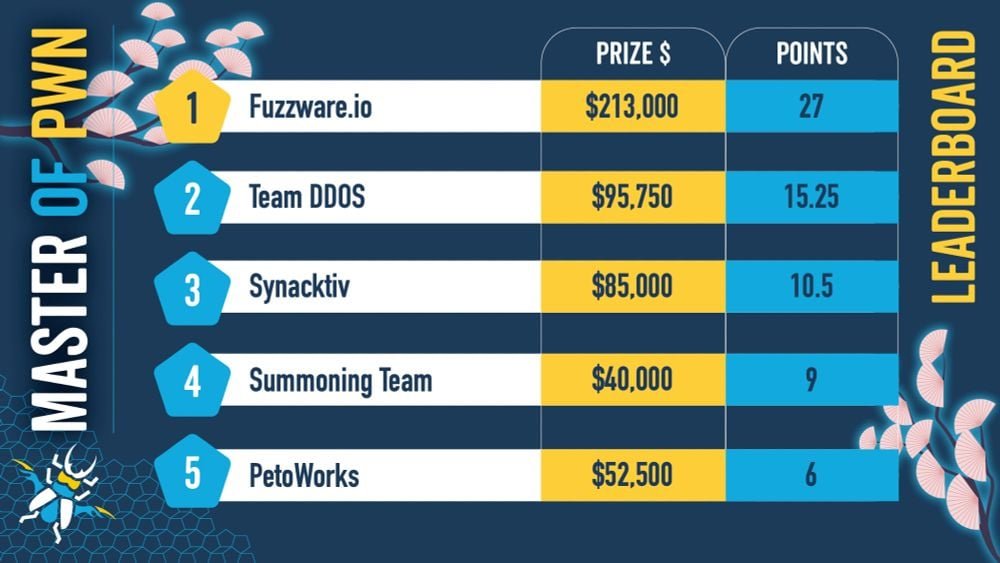
Fuzzware.io currently leads the competition's leaderboard with $213,000 earned after the first two days, and has earned another $95,000 by hacking the Phoenix Contact CHARX SEC-3150 charging controller, the ChargePoint Home Flex EV charger, and the Grizzl-E Smart 40A EV charging station. Sina Kheirkhah of Summoning Team collected another $40,000 after rooting the Kenwood DNR1007XR navigation receiver, the ChargePoint Home Flex, and the Alpine iLX-F511 multimedia receiver. Rob Blakely of Technical Debt Collectors and Hank Chen of InnoEdge Labs were also awarded $40,000 each after demonstrating zero-day exploit chains targeting Automotive Grade Linux and the Alpitronic HYC50 charging station.
After the first two days of the contest, security researchers have earned $955,750 in cash awards after exploiting 66 zero-day vulnerabilities. The progression from day one to day two shows an accelerating pace of discovery, with researchers finding new vulnerabilities in systems that were already considered secure.
Technical Deep Dive: Attack Vectors and Methods
The exploits demonstrated at Pwn2Own Automotive reveal several critical patterns in automotive security. On the first day, Synacktiv Team earned $35,000 after successfully chaining an information leak and an out-of-bounds write flaw to obtain root permissions on the Tesla Infotainment System via a USB-based attack. This attack vector is particularly concerning because it leverages a common physical interface—USB ports—that are typically accessible to drivers and passengers.
The team also received an additional $20,000 cash award for chaining three zero-day flaws to gain root-level code execution on the Sony XAV-9500ES digital media receiver. This multi-layered approach demonstrates how attackers combine multiple vulnerabilities to bypass security controls that would otherwise stop a single exploit.
Automotive Grade Linux Vulnerabilities
Rob Blakely's exploit chain targeting Automotive Grade Linux (AGL) is significant because AGL is an open-source platform used by multiple automotive manufacturers. The operating system, maintained by the Linux Foundation, is designed specifically for automotive applications and powers infotainment systems, instrument clusters, and other vehicle functions. AGL's architecture includes multiple security layers, but the exploit chain suggests that privilege escalation paths exist between different system components.
The Alpitronic HYC50 charging station exploit by Hank Chen highlights vulnerabilities in high-power EV charging infrastructure. These charging stations often run embedded Linux systems with web interfaces for configuration and monitoring. The exploit likely targeted either the web application layer or the underlying operating system services, potentially allowing an attacker to manipulate charging parameters or gain network access.
EV Charger Exploits: A Growing Concern
The Phoenix Contact CHARX SEC-3150 charging controller, ChargePoint Home Flex, and Grizzl-E Smart 40A represent different segments of the EV charging market. The CHARX SEC-3150 is an industrial-grade charging controller used in commercial installations, while the ChargePoint Home Flex and Grizzl-E Smart 40A are residential units. The diversity of targets suggests that vulnerabilities exist across the entire EV charging ecosystem, from consumer home chargers to commercial infrastructure.
These chargers typically communicate with vehicles using protocols like ISO 15118 or proprietary implementations. Vulnerabilities in these communication protocols could allow attackers to manipulate charging sessions, potentially causing battery damage or creating safety hazards. Additionally, many smart chargers connect to home networks and cloud services, creating additional attack surfaces.
What's Coming on Day Three
On the third day of Pwn2Own, the Grizzl-E Smart 40A will be targeted again by Slow Horses of Qrious Secure and the PetoWorks team, while the Juurin Oy team will go after the Alpitronic HYC50, and Ryo Kato will attempt to exploit the Autel MaxiCharger. This continued focus on charging infrastructure suggests that researchers believe there are still significant vulnerabilities to discover in these systems.
The Bigger Picture: Automotive Security Trends
During last year's Pwn2Own Automotive competition, hackers collected $886,250 after exploiting 49 zero-days. The previous year, during the Pwn2Own Automotive 2024 contest, they collected another $1,323,750 after demoing 49 zero-day bugs and hacking a Tesla car twice. The trend shows increasing investment in automotive security research, but also indicates that the attack surface continues to expand as vehicles become more connected and autonomous.
Vendor Response Timeline
Vendors have 90 days to develop and release security fixes for zero-day flaws that are exploited and reported during the Pwn2Own contest, before TrendMicro's Zero Day Initiative publicly discloses them. This timeline creates a critical window where vulnerabilities remain unpatched in the wild. The 90-day period is standard for coordinated vulnerability disclosure, but for automotive systems, it represents a significant challenge due to the complexity of automotive software and the lengthy certification processes required for safety-critical systems.
Practical Implications for Automotive Security
For automotive manufacturers and suppliers, the Pwn2Own results highlight several critical areas for improvement:
USB Interface Security: The Tesla infotainment exploit via USB suggests that physical interfaces need better validation and sandboxing. Manufacturers should implement strict USB device whitelisting and consider disabling unnecessary USB functionality in production vehicles.
Multi-Layer Exploit Chains: The Sony XAV-9500ES exploit chain demonstrates that single-layer security is insufficient. Defense-in-depth strategies must account for how vulnerabilities can be chained together across different system components.
Charging Infrastructure Security: The variety of exploited chargers indicates that EV charging security needs standardization and better security testing. Industry groups should develop common security benchmarks for charging equipment.
Open Source Platform Security: Automotive Grade Linux vulnerabilities show that even well-maintained open-source platforms require continuous security auditing and prompt patching of discovered issues.
Looking Ahead
The Pwn2Own Automotive contest serves as a critical stress test for the automotive industry's security posture. As vehicles become increasingly software-defined, the attack surface expands beyond traditional mechanical systems to include complex software stacks, network interfaces, and cloud connectivity.
For consumers, these findings underscore the importance of keeping vehicle software updated and being cautious about connecting unknown devices to vehicle systems. For manufacturers, the competition provides valuable data on which systems are most vulnerable and where security investments should be prioritized.
The full schedule for the second day and the results for each challenge are available here, while the complete schedule for Pwn2Own Automotive 2026 is available here.

Related Security Context
These automotive vulnerabilities exist alongside broader security challenges in the technology ecosystem. Recent reports show Tesla was hacked with 37 zero-days demoed at Pwn2Own Automotive 2026, while other security events like Zeroday Cloud hacking have awarded $320,000 for 11 zero days. Infrastructure vulnerabilities continue to be exploited, with VMware ESXi zero-days likely exploited a year before disclosure, and Cisco fixing Unified Communications RCE zero days that were exploited in attacks. Even security vendors are affected, with Fortinet admins reporting patched FortiGate firewalls getting hacked.
The automotive sector's security challenges mirror broader trends in connected systems, where the convergence of IT and operational technology creates new vulnerabilities that require specialized attention and expertise.

Comments
Please log in or register to join the discussion