As the holiday shopping season approaches, Chinese-based phishing groups are launching sophisticated SMS attacks that not only steal payment card information but also convert it into mobile wallets, creating a double threat for unsuspecting consumers.
Holiday Season Brings Wave of Sophisticated SMS Phishing Attacks Targeting Consumers
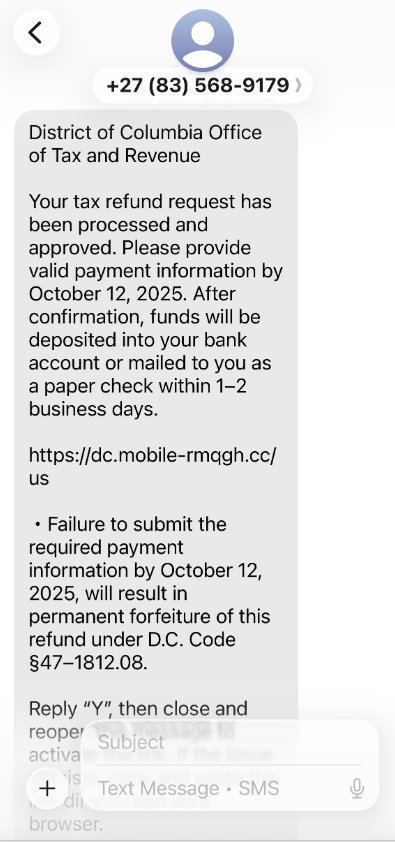
As the holiday shopping season approaches, cybersecurity experts are warning of a surge in sophisticated SMS phishing attacks designed to steal consumer payment information and convert it into mobile wallets. Chinese-based cybercriminal groups are increasingly targeting U.S. consumers with messages about unclaimed rewards points, tax refunds, and delivery issues—tactics that have proven effective during the high-volume shopping period.
Mobile Points and Tax Refunds: The New Lures
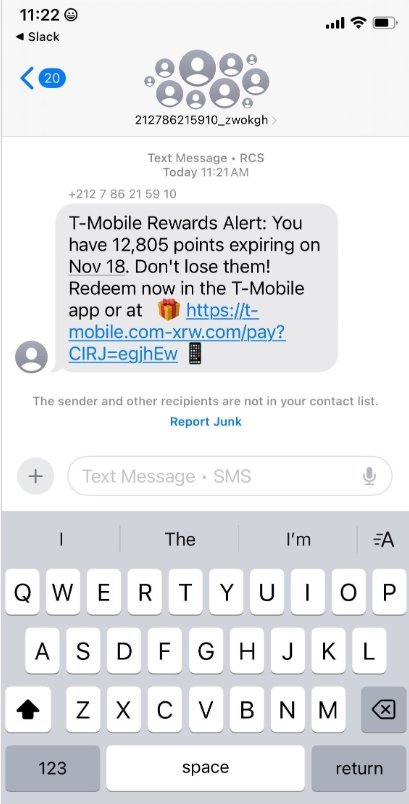
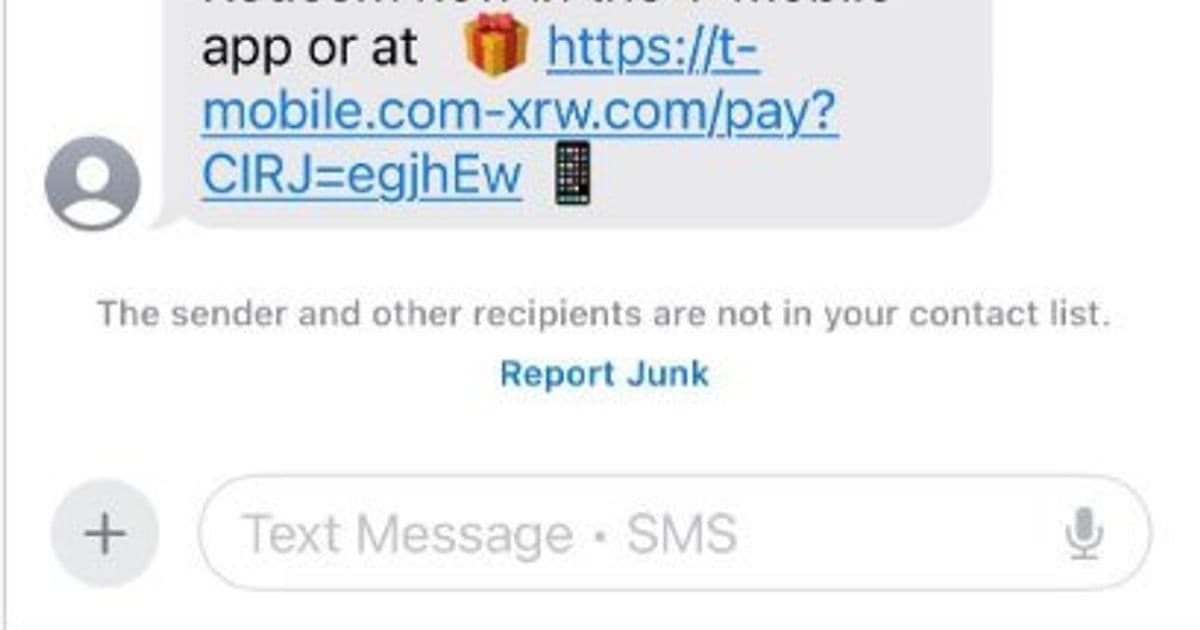
Over the past week, thousands of domain names have been registered for scam websites targeting T-Mobile customers with promises of thousands of unclaimed rewards points. These phishing domains are promoted via Apple's iMessage and Google's RCS messaging services, with instant messages spoofing T-Mobile claiming recipients are eligible to claim points.
"These points redemption schemes have not been very popular in the U.S., but have been in other geographies like EU and Asia for a while now," said Ford Merrill, security researcher at SecAlliance, a CSIS Security Group company.
The phishing websites, which only load on mobile devices, ask visitors for their name, address, phone number, and payment card information to claim the supposed rewards. Once card data is submitted, the site prompts users to share a one-time code sent by their financial institution—a clear sign that fraudsters are attempting to enroll the victim's card in a mobile wallet.
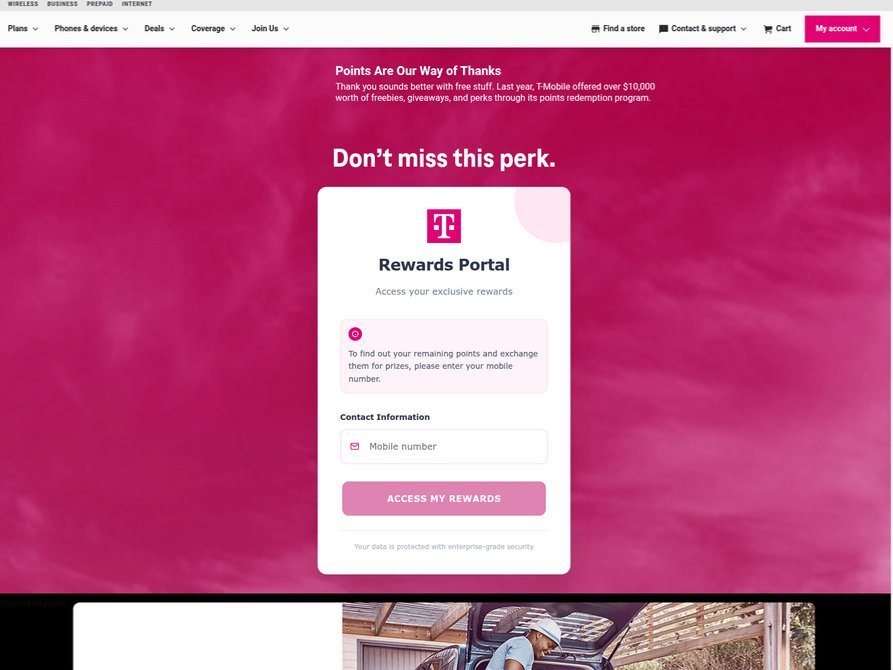
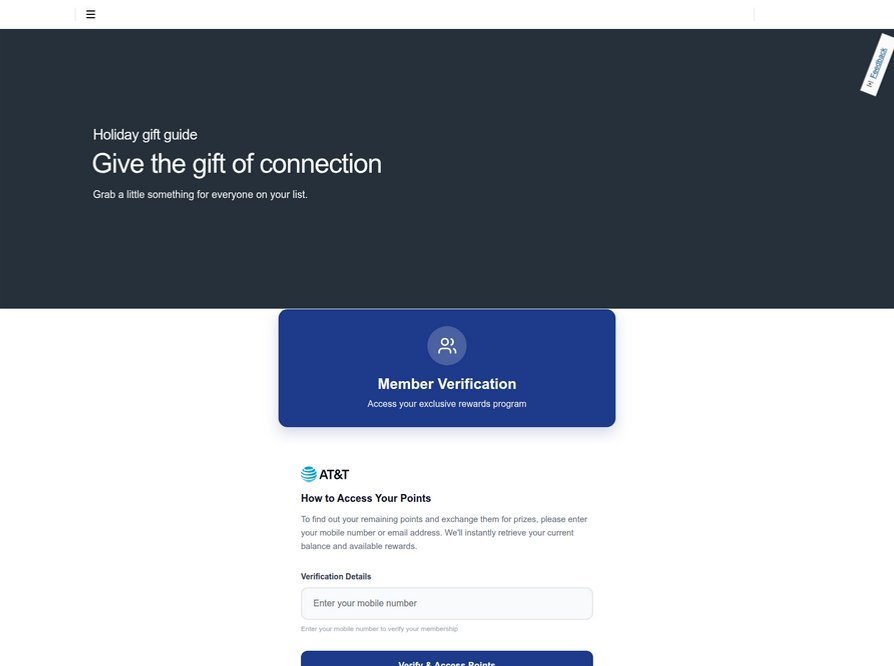
A similar pattern has emerged with AT&T customers, as well as with messages spoofing U.S. state tax authorities claiming recipients have unclaimed refunds. In all cases, the end goal remains the same: obtaining payment card details and the corresponding one-time codes that authorize mobile wallet enrollment.
The Technical Mechanics of Mobile Wallet Phishing
The technical sophistication of these attacks represents a significant evolution in phishing tactics. When victims submit their card information, the fraudsters immediately attempt to enroll those details in either Apple Pay or Google Wallet using the victim's bank's one-time verification system.
"If the victim also provides that one-time code, the phishers can then link the victim's card to a mobile device that they physically control," explained security researchers analyzing the campaign.
This approach allows criminals to bypass traditional credit card fraud detection mechanisms, as mobile wallet transactions often have different authentication requirements and spending limits than regular card payments.
The Rise of Fake E-commerce Stores
Beyond direct smishing attacks, the same Chinese phishing groups are now offering "phishing kits" for creating convincing fake e-commerce websites. These kits, which have been available for some time in other regions, are now being marketed to U.S. consumers.

"These fake e-commerce sites are tough because a lot of them can fly under the radar," Merrill noted. "They can go months without being shut down, they're hard to discover, and they generally don't get flagged by safe browsing tools."
Unlike traditional phishing sites that blast messages to the entire internet, these fake e-commerce stores operate more stealthily. They're advertised on legitimate platforms like Google and Facebook, with consumers typically finding them through searches for specific products. The malicious code that reveals their fraudulent nature is only activated during the checkout process, making them difficult to detect through standard web scanning.
Seasonal Surge in Phishing Activity
Security researchers note that the final weeks of the calendar year typically see a significant increase in smishing attacks, particularly those involving package delivery notifications.
"Every holiday season there is an explosion in smishing activity," Merrill warned. "Everyone is in a bigger hurry, frantically shopping online, paying less attention than they should, and they're just in a better mindset to get phished."
This seasonal uptick creates a perfect storm for cybercriminals, who exploit the combination of increased online shopping and consumer distraction to launch more successful attacks.
Protecting Yourself During the Shopping Season
As these phishing tactics become more sophisticated, consumers need to remain vigilant while shopping online. Security experts recommend several precautions:
Verify merchants before purchasing: Research unfamiliar online stores, especially those offering unusually low prices. A quick WHOIS search can reveal when a domain was registered—recently created domains may indicate a scam.
Avoid clicking on links in messages: If you receive a notification about a package or account issue, visit the official website directly rather than clicking on links in messages.
Be skeptical of urgent requests: Phishers often create false urgency to bypass critical thinking. Be wary of messages requiring immediate action.
Review checkout processes carefully: Pay attention to requests for one-time verification codes during checkout, especially if they seem unusual.
Monitor financial statements closely: Regularly check your credit card statements for unauthorized charges, as criminals may delay fraudulent transactions until they can be buried among legitimate holiday purchases.
Reporting Phishing Attacks
Consumers who encounter smishing messages or phishing websites can help combat these threats by reporting them. Services like SURBL's smishreport.com allow users to submit screenshots of phishing messages, which helps security researchers identify and block malicious domains.
"If [a domain is] unlisted, we can find and add the new pattern and kill the rest of the matching domains," explained Raymond Dijkxhoorn, CEO and founding member of SURBL. "Just make a screenshot and upload. The tool does the rest."
As the holiday shopping season progresses, consumers and security researchers alike will need to remain vigilant against these evolving phishing tactics that continue to adapt to new technologies and consumer behaviors.
Comments
Please log in or register to join the discussion