As identity-based attacks become the primary threat vector, organizations must shift from prevention-only approaches to proactive detection and response. Identity Threat Detection & Response (ITDR) provides the visibility needed to identify compromised accounts and insider threats before they cause damage.

Security professionals face a fundamental shift in defensive tactics: attackers increasingly bypass traditional perimeter defenses by logging in with compromised credentials rather than breaking through firewalls. With phishing, password leaks, and social engineering enabling widespread account takeovers, identity threats now represent the most common attack vector against businesses.
"Attackers operate on scale and speed," explains a Tenfold Security researcher. "Automated credential stuffing or password spraying attacks mean thousands of login attempts can hit an organization daily. When just one succeeds, adversaries move laterally, escalate privileges, and often remain undetected for months."
While preventative measures like multi-factor authentication (MFA), email filtering, and strict access controls remain essential, they're no longer sufficient alone. Security teams increasingly confront a critical question: How would you know if attackers are already inside your environment?
This reality drives adoption of Identity Threat Detection & Response (ITDR) as a core security strategy. ITDR solutions continuously monitor and analyze user activity across systems to identify anomalies indicative of compromise. Key capabilities include:
- Behavioral baselining: Establishing normal activity patterns for users (typical login times, accessed resources)
- Real-time anomaly detection: Flagging deviations like off-hours logins, privilege escalation, or abnormal data access
- Centralized event correlation: Aggregating logs from Active Directory, cloud services, and applications into unified timelines
- Automated response workflows: Enabling rapid investigation and containment of suspicious sessions
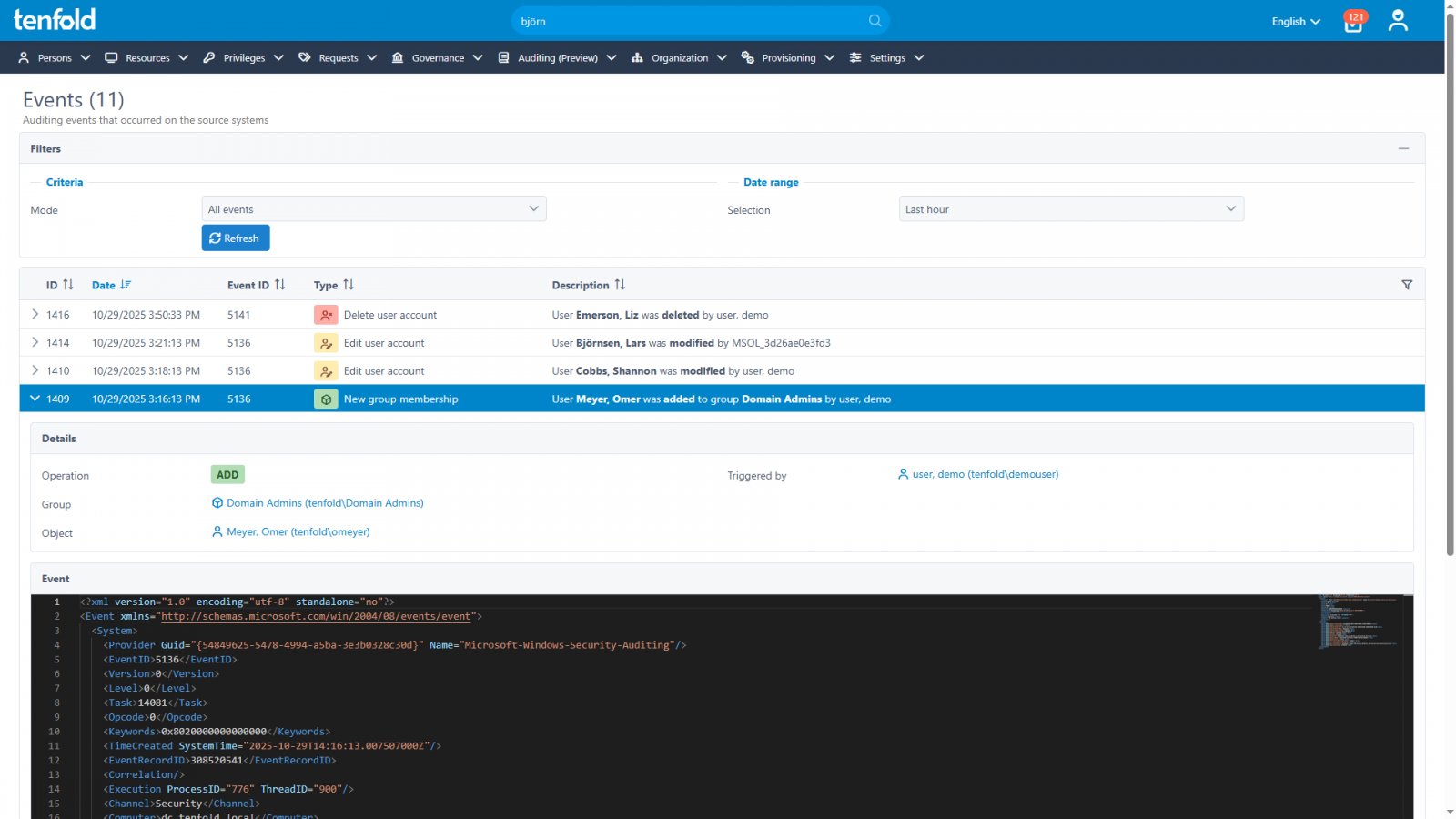
High-priority detection patterns include sudden spikes in failed logins, unauthorized security group modifications, privileged account access outside maintenance windows, and bulk file access unrelated to job functions. "Even benign anomalies warrant investigation," notes the Tenfold team. "The cost of missing a real threat far outweighs checking a false positive."
Implementing effective ITDR requires integrating three components:
- Comprehensive logging: Capturing authentication events, permission changes, and resource access across all systems
- Behavioral analytics: Applying machine learning to distinguish legitimate activity from malicious patterns
- Response automation: Containing threats through session termination or access revocation before damage occurs
Platforms like Tenfold combine ITDR with identity governance features—such as automated user provisioning and access reviews—in a unified console. This consolidation allows security teams to:
- Visualize permission relationships during threat investigations
- Immediately revoke excessive privileges exploited in attacks
- Validate whether detected anomalies violate access policies
As organizations plan 2026 security strategies, ITDR moves from optional to essential. The framework provides what firewalls and endpoint protection cannot: visibility into authorized but malicious activity. For implementation guidance, review the SANS Institute's ITDR whitepaper or Microsoft's security benchmarks.
This article is sponsored by Tenfold Software, which provided technical details and use cases.

Comments
Please log in or register to join the discussion