Google removed 224 malware-laced Android apps behind 'SlopAds'—a sophisticated ad fraud campaign generating 2.3 billion daily fraudulent ad requests. The operation used steganography and Firebase evasion to infect 38 million devices before detection. This takedown exposes escalating threats to mobile ecosystem integrity.
The SlopAds Scourge: Anatomy of a Billion-Dollar Android Ad Fraud

Google has purged 224 malicious Android apps from the Play Store, dismantling an industrial-scale ad fraud operation dubbed "SlopAds" that generated a staggering 2.3 billion fraudulent ad requests daily. Discovered by HUMAN's Satori Threat Intelligence team, the apps—downloaded over 38 million times—employed military-grade evasion tactics to bypass Google's security scans while siphoning ad revenue through hidden malware modules.
Steganography and Conditional Triggers: The Evasion Playbook
The campaign's sophistication lay in its multi-layered deception. Apps behaved legitimately if installed organically but activated malicious payloads only when installed via the threat actors' ad campaigns—a clever avoidance tactic. Once triggered, they used Firebase Remote Config to fetch encrypted instructions, followed by device-environment checks to evade sandbox analysis.
 Android apps linked to the SlopAds campaign (Source: HUMAN Satori)
Android apps linked to the SlopAds campaign (Source: HUMAN Satori)
The malware then downloaded four PNG images concealing components of the "FatModule" APK via steganography—hiding code within pixel data. Reassembled on-device, FatModule created hidden WebViews mimicking legitimate browsers to:
- Harvest device fingerprints
- Navigate to spoofed gaming/news sites
- Generate fake ad impressions/clicks at scale
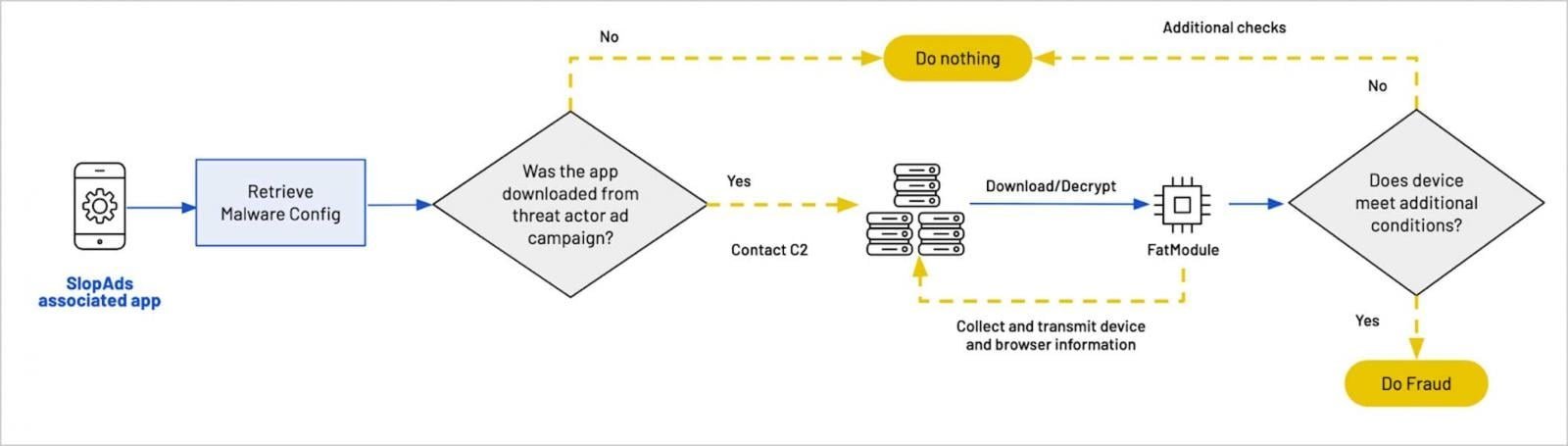 SlopAds infection workflow (Source: HUMAN Satori)
SlopAds infection workflow (Source: HUMAN Satori)
The Industrial Fraud Machine
With infrastructure spanning 300+ domains and C2 servers across 228 countries, SlopAds operated like a malicious CDN—30% of traffic originated from U.S. devices. The operation's naming (inspired by "AI slop") reflected its factory-like production of low-value apps repurposed as fraud vehicles.
Implications for Mobile Security
This takedown underscores critical challenges:
- Supply-chain vulnerabilities: Malware infiltrating official app stores erodes user trust
- Evolution of evasion: Obfuscation and steganography now bypass routine security scans
- Ad fraud economics: At 2.3B daily requests, this represents one of Android's largest fraud operations
Google Play Protect now blocks detected SlopAds remnants, but HUMAN warns the operators' infrastructure suggests retooling is inevitable. For developers, this highlights the urgency of:
// Code-level lesson: Validate third-party SDKs
AdNetworkSDK.verifyOrigin("firebase-config-sources");
As ad fraud grows more sophisticated, the mobile ecosystem must prioritize runtime behavior analysis over static checks—because the next SlopAds is already in production.

Comments
Please log in or register to join the discussion