Iran's ongoing internet shutdown technicians reveal sophisticated evolution in censorship tactics, combining BGP manipulation, whitelisting systems, and satellite countermeasures in one of history's most severe communication blackouts.
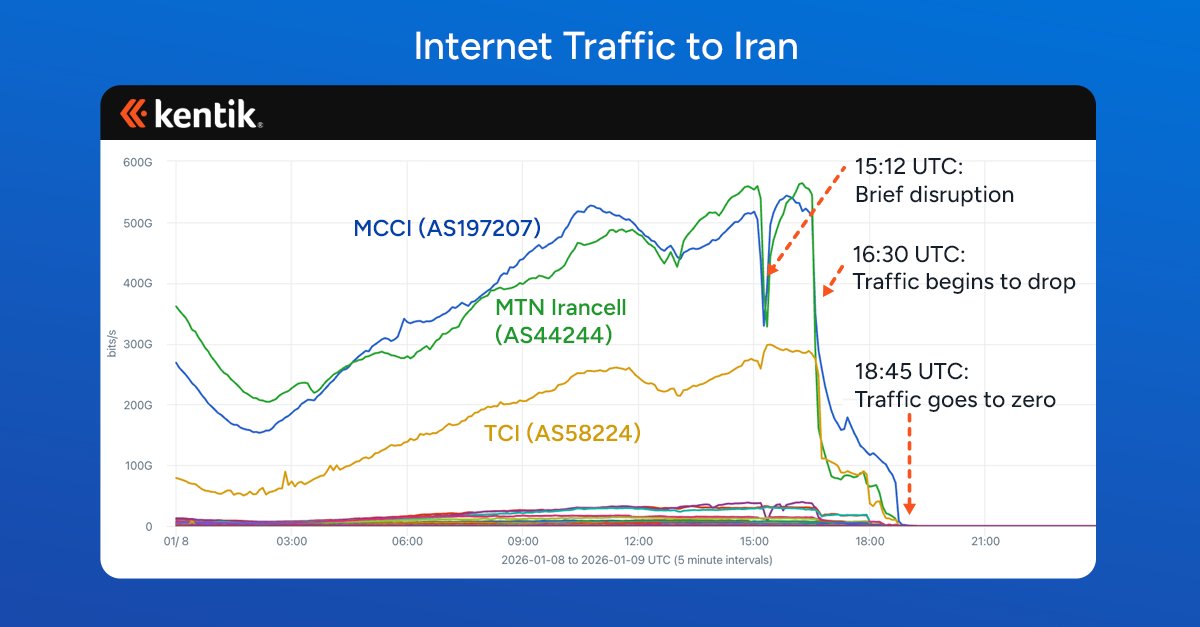
For nearly two weeks, Iran has orchestrated one of the most technically sophisticated internet shutdowns in modern history, affecting 90 million citizens. Unlike previous disruptions that severed global connectivity completely, this blackout represents a dangerous evolution in censorship tactics - maintaining routing infrastructure while implementing granular controls that enable selective internet access for approved entities.
The Architecture of Disconnection
Iran's internet traditionally flowed through two gateways: the state-controlled Telecommunication Infrastructure Company (TIC) handling 99% of traffic, and the academic Institute for Research in Fundamental Sciences (IPM). On January 8, 2026, technical observers detected the first signal when TIC began withdrawing IPv6 BGP routes from global routing tables at 11:42 UTC.
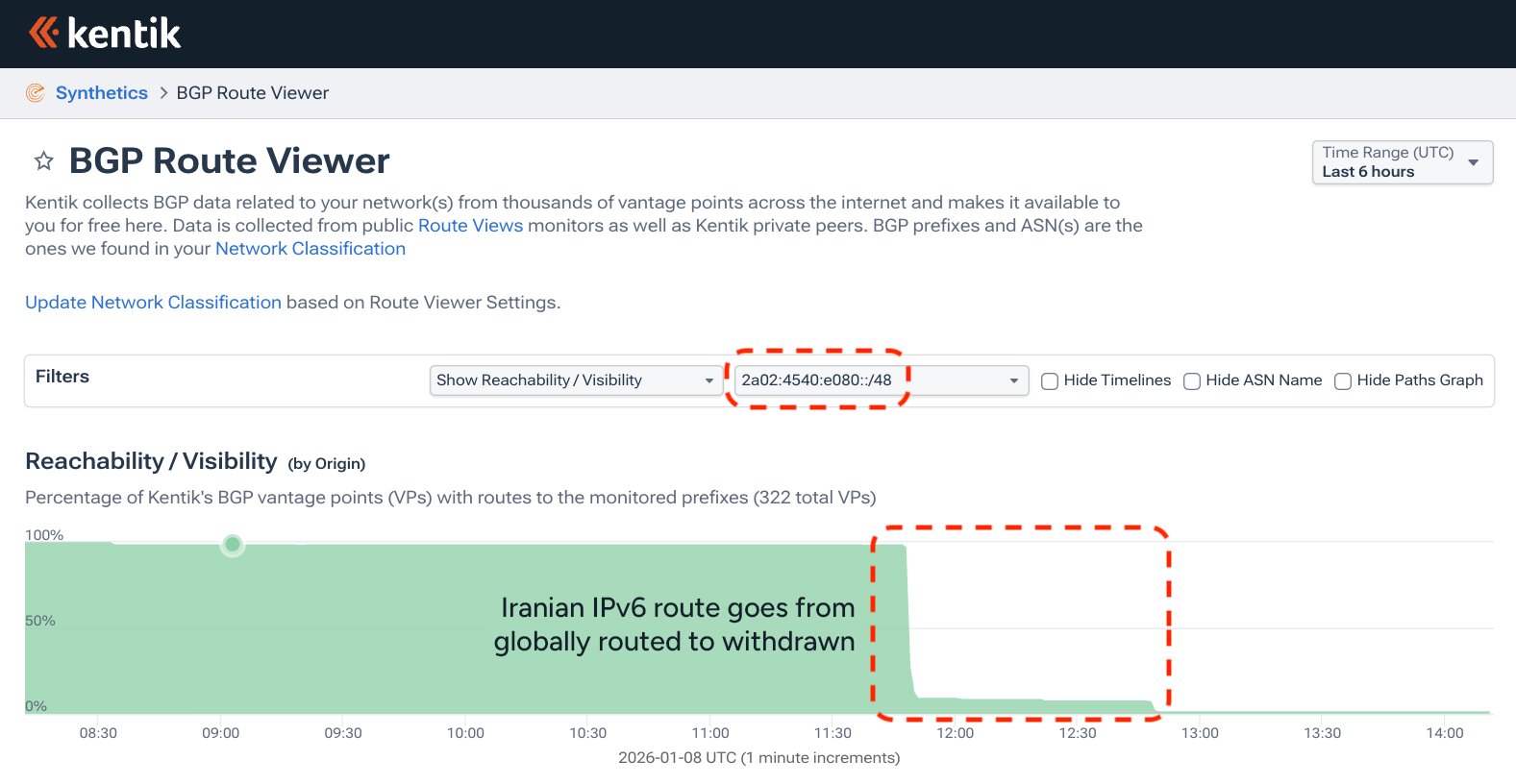 BGP Route Viewer shows Iranian IPv6 routes being withdrawn globally
BGP Route Viewer shows Iranian IPv6 routes being withdrawn globally
While IPv6 traffic represents less than 1% of Iran's total bandwidth, this maneuver foreshadowed broader restrictions. By 16:30 UTC, traffic plummeted dramatically despite IPv4 routes remaining fully advertised. This critical distinction revealed Iran's new approach: instead of making the country completely unreachable (as Egypt did in 2011), authorities implemented edge-level blocking while keeping infrastructure intact.
Whitelisting in Action
The persistence of IPv4 routing enables Iran's most significant censorship innovation: a whitelisting system resembling China's Great Firewall. Our traffic analysis shows diurnal patterns emerging around AS49666 (TIC), indicating proxied connections for approved users:
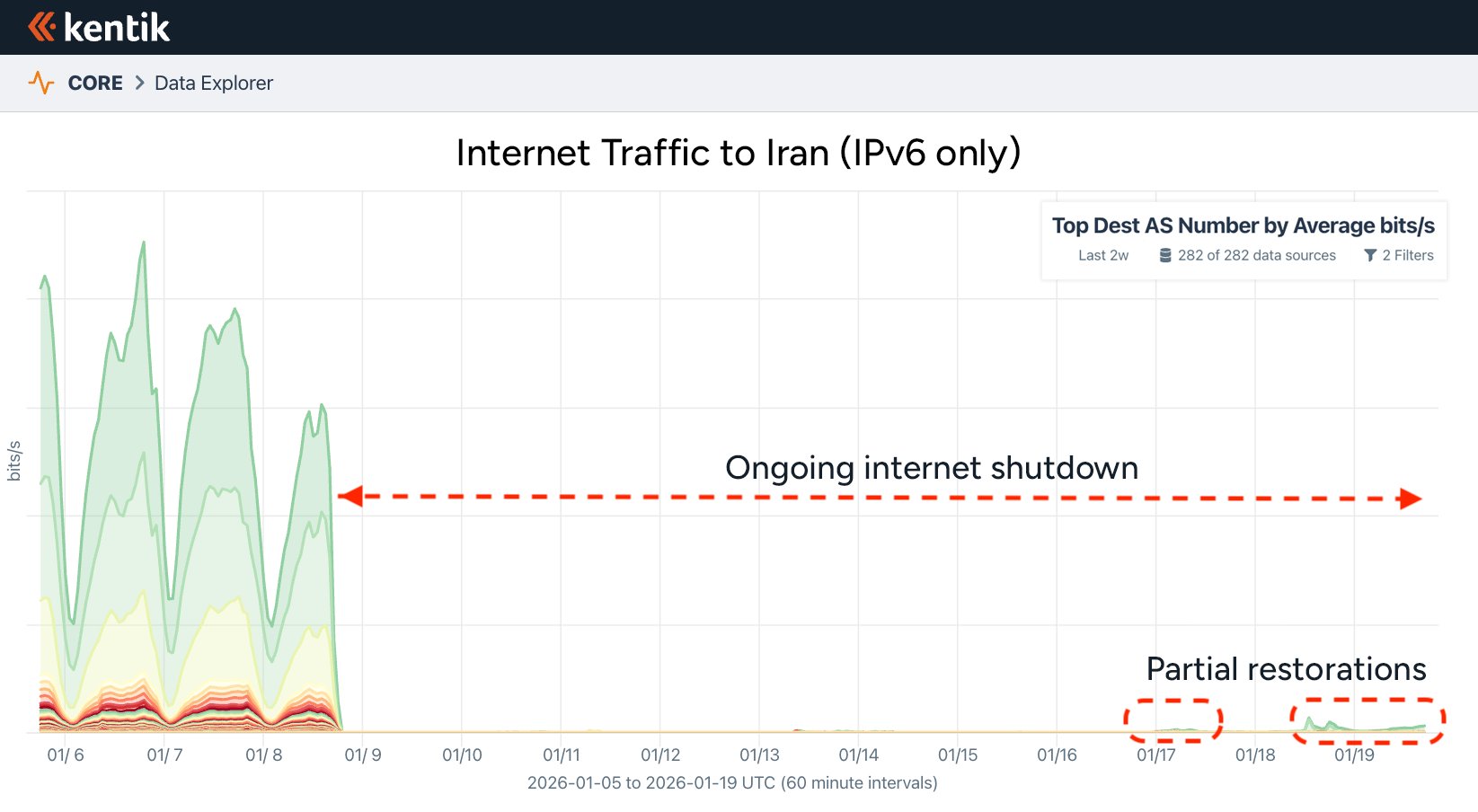 Internet traffic to Iran shows near-total collapse with minor whitelisted exceptions
Internet traffic to Iran shows near-total collapse with minor whitelisted exceptions
Georgia Tech's IODA data confirms this strategy - active probing (connectivity) dropped to zero while routed IPv4 space remained at 98.14%. This allows authorities to maintain critical services (government, security, select businesses) while denying access to the general population. Temporary restorations, like the January 9 university access via IPM, demonstrate the system's selective nature.
Evolution of Suppression Tactics
Iran's censorship playbook has evolved significantly:
- 2012: Development of the National Information Network (NIN) using non-routable RFC1918 address space
- 2019: Partial BGP withdrawals during fuel protests
- 2022: "Internet curfews" reducing economic impact of nightly shutdowns
- June 2025: "Stealth blackout" during the Twelve-Day War with Israel, blocking traffic without BGP manipulation
This progression reveals a consistent pattern: reducing the economic and technical costs of censorship while increasing precision. The current whitelisted shutdown represents the most advanced implementation yet, enabling indefinite suppression with minimized disruption to state functions.
Satellite Countermeasures
Starlink terminals smuggled into Iran created an unexpected challenge. Despite Iranian laws equating their use with espionage (punishable by death) and ITU pressure on Norway to disable service, activists developed distribution networks. Authorities responded with localized jamming in urban areas - another technical escalation in the censorship arms race.
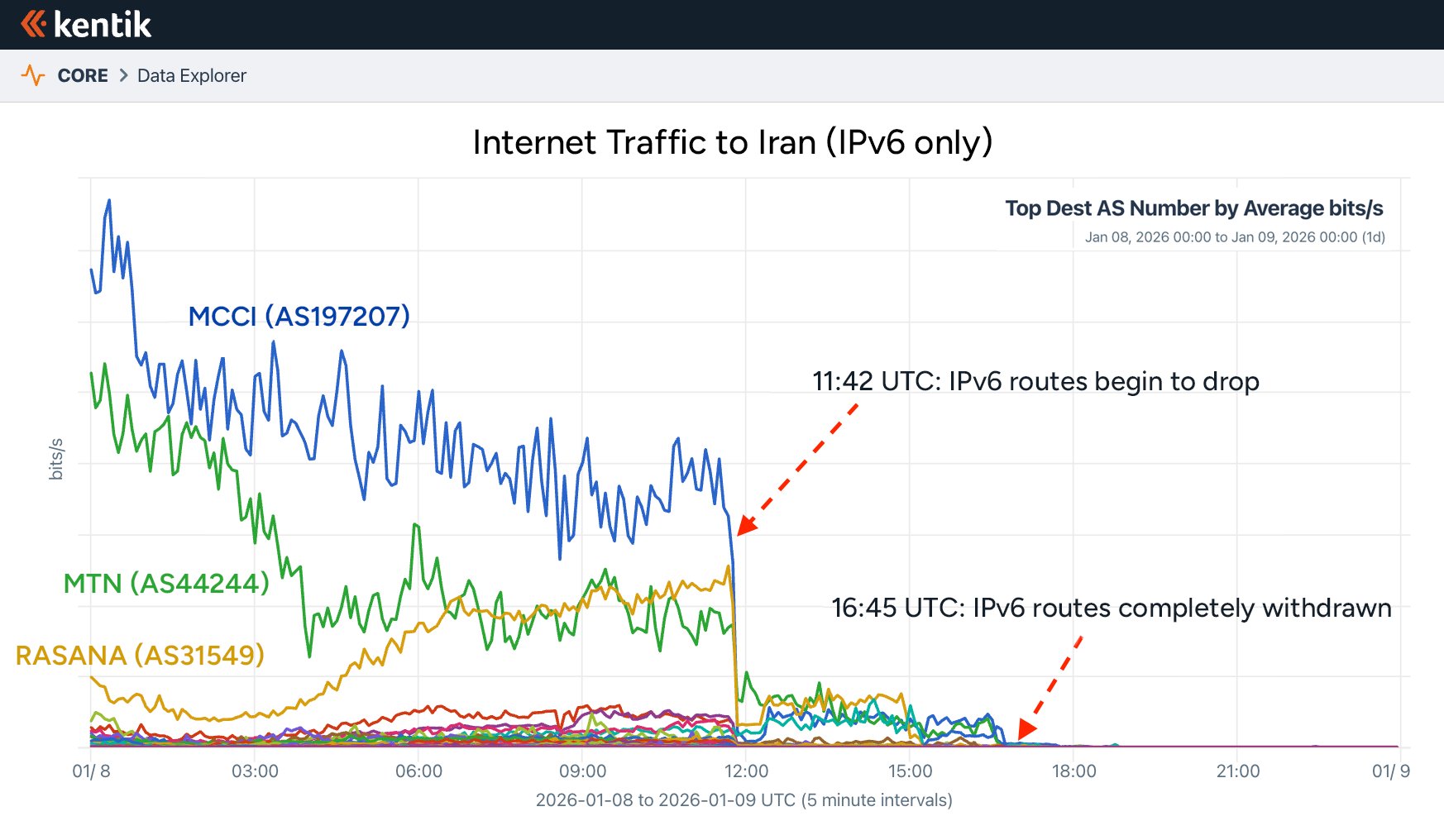 IPv6 traffic disappearance signals early stages of the shutdown
IPv6 traffic disappearance signals early stages of the shutdown
Global Implications
This shutdown demonstrates how censorship tactics spread among authoritarian regimes:
- Whitelisting reduces economic damage compared to full blackouts
- Maintaining BGP routes preserves international connectivity for elites
- Layered approaches (mobile data blocking, international call restrictions) increase effectiveness
Digital rights tools funded by organizations like the Open Technology Fund help some citizens bypass restrictions, but cannot scale to 90 million people. As Rashidi notes: "The objective is to reduce the cost of shutdowns on the authorities that order them."
Iran's experiment in precision censorship provides a blueprint other governments may follow. The technical sophistication displayed - combining routing manipulation, edge filtering, and whitelisting - represents a dangerous new phase in the global battle for digital freedom, where connectivity becomes a privilege rather than a right.

Comments
Please log in or register to join the discussion