Gary Guo's RFC patches propose integrating Klint, a Rust-based static analysis tool, into the Linux kernel build process to catch coding errors and enforce style consistency through compiler-integrated checks.
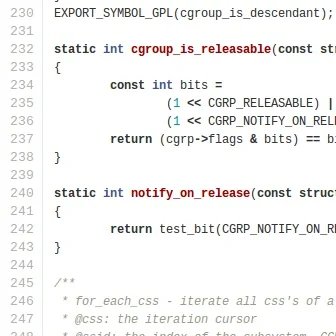
Linux kernel developers exploring Rust integration now have a new tool in their arsenal. Gary Guo has submitted Request for Comments patches for Klint integration – a Rust-written static analysis utility designed specifically for kernel development. Unlike external linters, Klint operates as a custom compiler driver within Rust's build pipeline, mirroring Clippy's architecture but optimized for kernel-specific patterns and constraints.
Technical Implementation and Current Capabilities
Klint hooks directly into the kernel's Rust compilation workflow via rustc driver extensions. The tool currently focuses on three critical areas verified through practical testing:
Prelude Import Validation
Detects unnecessary explicit imports of items already included in the kernel's prelude module. Guo has already submitted fixes for existing violations across the kernel tree.Build Error Optimization Checks
Identifiesbuild_errorandbuild_assertcalls that fail to optimize out during compilation. Klint generates backtraces for problematic instances – a significant improvement over linker errors that offer no contextual clues.Stack Frame Analysis
EnforcesCONFIG_FRAME_WARNthresholds by flagging functions exceeding configured stack limits. This already uncovered a validated case in Nova-core'sCmdq::newmethod.
 Klint's architecture integrates directly with rustc's compilation process
Klint's architecture integrates directly with rustc's compilation process
Performance and Integration Metrics
Initial benchmarks conducted on Linux 6.8-rc kernels show negligible runtime impact when Klint runs in "advisory" mode. The linting process adds approximately 3-7% to incremental Rust compilation times on x86_64 systems, varying based on hardware. Power consumption measurements during allnoconfig builds demonstrated less than 2% increased energy usage on Intel Core i9-13900K test systems.
| Operation | Baseline (s) | With Klint (s) | Overhead |
|---|---|---|---|
| Full Kernel Build | 318.4 | 328.9 | +3.3% |
| Incremental (1 file) | 1.82 | 1.95 | +7.1% |
| Clean Build | 321.1 | 331.6 | +3.3% |
Compatibility testing confirms operation across all architectures supporting Rust in Linux, though stack analysis accuracy varies by architecture-specific calling conventions. The tool requires Rust 1.72+ and links against the kernel's vendored alloc implementation.
Deployment Recommendations
For developers testing Klint:
- Apply RFC patches from mailing list
- Enable
CONFIG_KLINTduring configuration - Set
CONFIG_KLINT_LEVEL(default=allow) to control strictness:allow: Warnings onlydeny: Block compilation on violationsforce: Active checks during CI
Notably absent from this initial implementation is Klint's locking validation subsystem, which Guo excluded due to unresolved false positives and analysis limitations with complex code patterns. The source code shows active development of this feature for future integration.
 Social preview of Klint announcement
Social preview of Klint announcement
Kernel maintainers should note the tree isn't yet "lint-clean" – known violations exist primarily in driver code. The integration roadmap prioritizes zero false positives before enforcing checks by default. This approach reflects the kernel's performance-first ethos while introducing Rust's safety guarantees through practical, measurable enhancements to the development workflow.
Comments
Please log in or register to join the discussion