The Lumma infostealer malware operation has rapidly rebuilt its infrastructure and infection capabilities just weeks after a major international law enforcement takedown disrupted its operations. Despite the seizure of 2,300 domains, Lumma's operators leveraged cloud infrastructure shifts and new social engineering tactics to regain prominence, highlighting the limitations of infrastructure-only disruption against determined cybercriminals.
In May 2025, a coordinated law enforcement operation delivered a significant blow to the notorious Lumma infostealer, seizing 2,300 domains and disrupting key infrastructure for this Malware-as-a-Service (MaaS) platform. Early reports suggested a major victory. Yet, Lumma's operators signaled their resilience almost immediately, posting on cybercrime forums that their core server—though remotely wiped—remained intact, and restoration was underway. 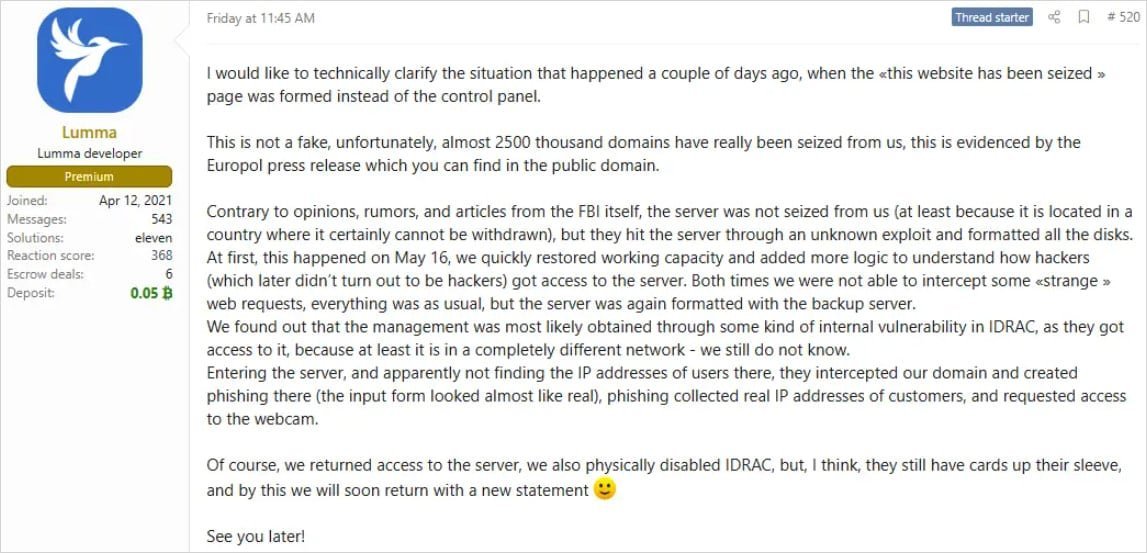
A Swift and Calculated Rebuild
Telemetry from Trend Micro now confirms Lumma has staged a significant comeback. "Following the law enforcement action against Lumma Stealer and its associated infrastructure, our team has observed clear signs of a resurgence in Lumma's operations," states a recent Trend Micro report. "Network telemetry indicates that Lumma's infrastructure began ramping up again within weeks of the takedown." Activity levels are nearing pre-disruption benchmarks, demonstrating remarkable operational agility. 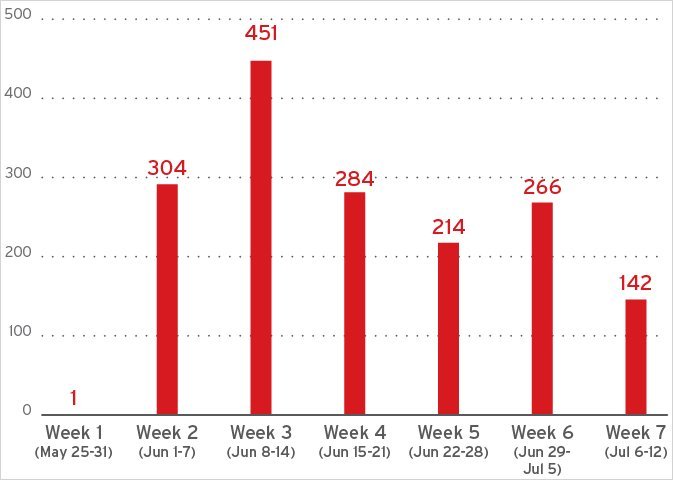
Evolving Infrastructure and Evasion Tactics
To mitigate future takedown risks, Lumma has shifted its command-and-control (C2) infrastructure away from Cloudflare, now heavily utilizing Russian-based provider Selectel. This move complicates future enforcement actions and underscores the threat actors' adaptability in leveraging legitimate services.
Four Pronged Attack Strategy Returns
Lumma's resurgence is marked by a diversified infection strategy targeting users across multiple platforms:
- Fake Cracks/Keygens: Malvertising and manipulated search results lure victims to sites employing Traffic Detection Systems (TDS) before delivering the Lumma downloader.
- ClickFix CAPTCHA Scams: Compromised websites display fake CAPTCHAs tricking users into executing malicious PowerShell commands that load Lumma directly into memory, bypassing file-based detection.
- Abusing GitHub: Attackers create repositories with AI-generated content promoting fake game cheats, hosting Lumma payloads (e.g.,
TempSpoofer.exe) within executables or ZIP files. - Social Media Lures (YouTube/Facebook): Videos and posts promoting cracked software lead to external sites, often abusing trusted domains like
sites.google.com, to host the final Lumma payload. {{IMAGE:4}}
The Futility of Disruption Without Deterrence
Lumma's rapid recovery starkly illustrates a critical weakness in combating financially motivated cybercrime: infrastructure seizures alone, without accompanying arrests or indictments of key operators, are largely temporary setbacks. The immense profitability of MaaS operations like Lumma ensures that determined threat actors treat law enforcement actions as manageable operational hurdles. The resilience shown by Lumma underscores the need for sustained, multi-faceted strategies targeting the individuals and financial flows underpinning these criminal enterprises to achieve lasting impact.
Source: Analysis based on reporting by Bill Toulas at BleepingComputer and technical data from Trend Micro.

Comments
Please log in or register to join the discussion