A critical macOS vulnerability patched in March allows attackers to bypass privacy safeguards and access sensitive Apple Intelligence data. Dubbed 'Sploitlight,' the flaw exploits Spotlight plugins to harvest geolocation, facial recognition, and user activity. Microsoft warns the breach could extend to all devices on a victim's iCloud account.
Microsoft security researchers have uncovered a significant macOS vulnerability that bypasses Apple's core privacy framework, leaking sensitive user data—including cached Apple Intelligence information. Tracked as CVE-2025-31199 and dubbed Sploitlight, the flaw exploits macOS's Spotlight plugins to circumvent Transparency, Consent, and Control (TCC) protections. Apple patched the issue in macOS Sequoia 15.4, describing it as a "logging issue" with "improved data redaction."
How Sploitlight Breaches macOS Privacy
TCC is Apple's foundational privacy layer, restricting app access to private user data without explicit permission. While Apple restricts TCC access to apps with full disk access, Microsoft's team—Jonathan Bar Or, Alexia Wilson, and Christine Fossaceca—discovered that Spotlight plugins operate with privileged permissions. Attackers could abuse this to access and exfiltrate:
- Precise geolocation data and photo/video metadata
- Facial and person recognition information
- User search history, preferences, and activity context
- Deleted photos/videos and shared library contents
- Apple Intelligence-cached insights
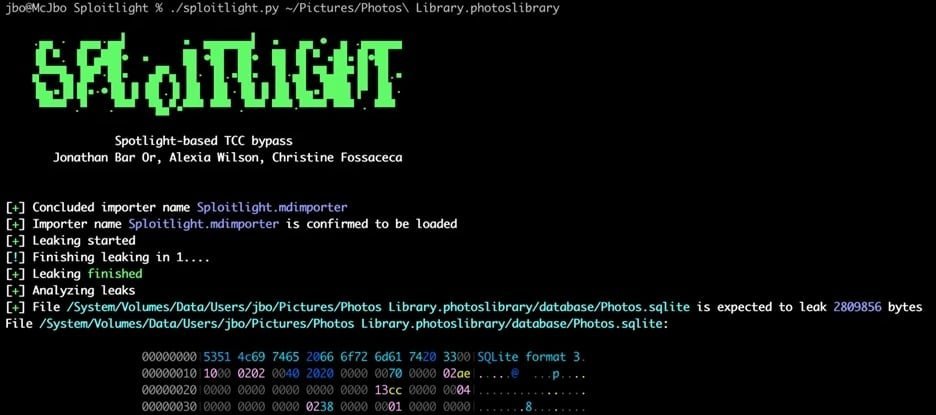 Spoitlight exploit diagram (Microsoft)
Spoitlight exploit diagram (Microsoft)
iCloud Amplification and Historical Context
Crucially, the vulnerability extends beyond a single device. As Microsoft warns:
"An attacker with access to a user's macOS device could exploit the vulnerability to determine remote information of other devices linked to the same iCloud account."
Sploitlight follows a pattern of TCC bypasses Microsoft has exposed since 2020, including:
- powerdir (CVE-2021-30970)
- HM-Surf
- Time Machine mount exploits (CVE-2020-9771)
However, Sploitlight's ability to harvest Apple Intelligence data makes it uniquely severe. Microsoft notes this marks an escalation in macOS privacy threats, coinciding with Apple's push into AI-driven features.
Broader Implications for macOS Security
This discovery continues Microsoft's streak of uncovering critical macOS flaws, including:
- Shrootless (CVE-2021-30892): SIP bypass enabling rootkits (2021)
- Achilles (CVE-2022-42821): Gatekeeper bypass for malware installation
- Migraine (CVE-2023-32369): SIP bypass patched in 2023
- CVE-2024-44243: Kernel extension vulnerability (2024)
While patched, Sploitlight underscores the persistent challenge of securing privileged macOS subsystems against determined adversaries. Developers and security teams should prioritize updating to macOS 15.4+ and audit third-party Spotlight plugins. As Apple Intelligence adoption grows, safeguarding its data pipelines becomes increasingly critical—not just for individual users, but entire interconnected device ecosystems.
Source: BleepingComputer (Microsoft vulnerability analysis)
Comments
Please log in or register to join the discussion