Microsoft's introduction of Conditional Access for Agent Identities in Entra ID marks a significant shift in non-human identity management, offering limited but crucial controls for AI workloads while revealing gaps compared to AWS and Google Cloud's approaches.

Microsoft's Conditional Access for Agent Identities represents a fundamental rethinking of identity governance as AI systems become operational workforce components. Unlike traditional service principals or human users, these specialized identities require security models accounting for autonomous decision-making and continuous operation patterns.
What Changed: The Agent Identity Paradigm
Microsoft Entra now recognizes three new entity types:
- Agent Identity: AI systems performing autonomous tasks
- Agent User: Hybrid identities combining human-like interactions with AI capabilities
- Agent Blueprint: Templates for mass AI identity provisioning
This structural shift enables token-based access control specifically tailored to AI workloads, with Conditional Access policies triggering during token requests rather than interactive logins. However, current capabilities remain intentionally constrained:
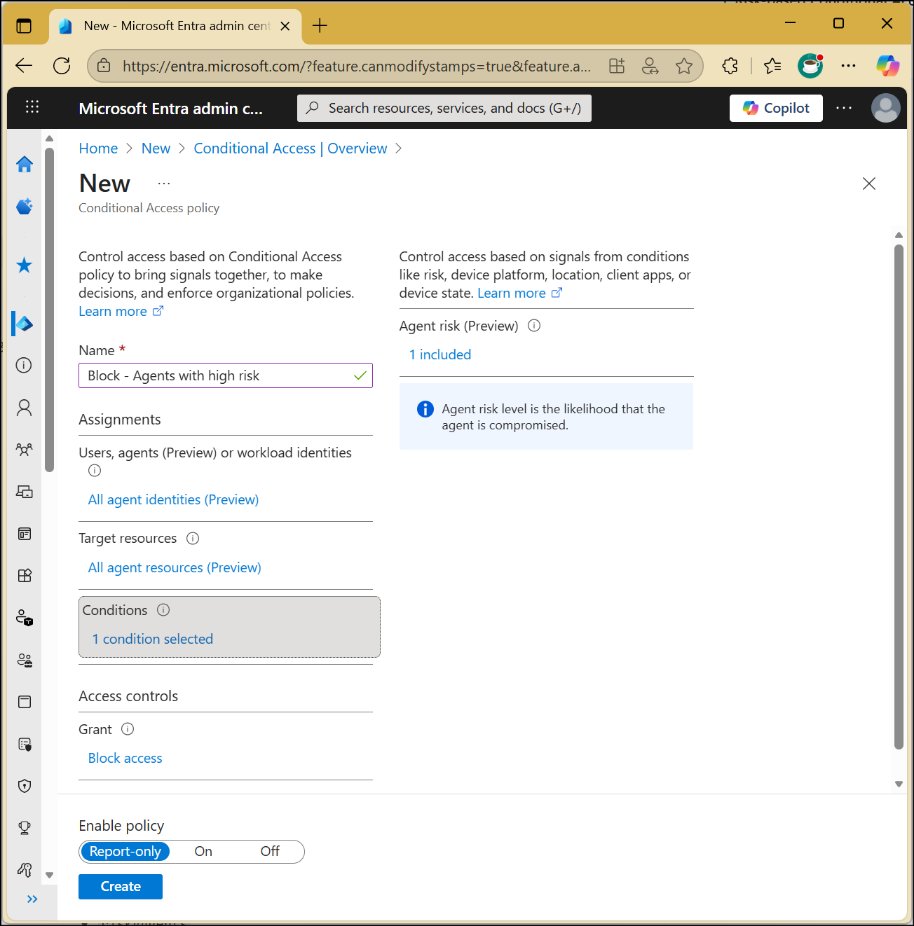 Diagram: Microsoft Entra's limited Conditional Access flow for agent identities
Diagram: Microsoft Entra's limited Conditional Access flow for agent identities
Provider Comparison: Cloud Identity Management Divergence
| Capability | Microsoft Entra Agents | AWS IAM Roles | Google Cloud Service Accounts |
|---|---|---|---|
| MFA Enforcement | ❌ Not supported | ❌ (Via boundary policies) | ❌ |
| Risk-Based Access Control | ✔ Preview agent risk scoring | ✔ Via IAM Access Analyzer | ❌ |
| Automated Secret Rotation | ❌ | ✔ Integrated with Secrets Manager | ✔ Service Account Key Rotation |
| Session Control | ❌ | ✔ IAM Roles Anywhere | ❌ |
| Cross-Service Access | ❌ | ✔ Cross-account assume-role | ✔ Cross-project delegation |
This comparison reveals Microsoft's focus on foundational token control versus AWS' policy-boundary approach and Google's service-centric model. Enterprises running multi-cloud AI workloads must now reconcile three distinct non-human identity governance frameworks.
Business Impact: Strategic Considerations
AI Sprawl Containment: The blueprint exclusion creates governance gaps. Organizations must implement compensating controls like Azure Policy for template governance.
Incident Response Limitations: Without session controls, terminating compromised AI agents requires full identity revocation rather than granular session termination available for human users.
Multi-Cloud Identity Bridging: Enterprises using AWS Bedrock or Google Vertex AI agents with Microsoft resources face policy synchronization challenges. Third-party solutions like Hashicorp Boundary may become necessary.
Compliance Implications: Financial services and healthcare sectors requiring MFA-equivalent for all privileged access must delay AI agent adoption or implement proxy authentication layers.
Migration Considerations
Organizations transitioning AI workloads to Azure should:
- Implement agent identity segmentation matching existing AWS IAM role or GCP service account structures
- Develop parallel monitoring using Microsoft Sentinel for agent activity correlation
- Establish blueprint governance workflows outside Conditional Access
Future Outlook
Microsoft's roadmap suggests coming enhancements:
- Agent behavior analytics
- Task-scoped access policies
- Blueprint governance integration
Until then, enterprises must treat Conditional Access for agents as a basic containment layer rather than comprehensive governance solution. The strategic imperative lies in developing cross-platform AI identity standards before operational complexity escalates.
As cloud providers diverge in non-human identity approaches, multi-cloud organizations face increasing operational overhead. Microsoft's current implementation provides essential Zero Trust foundations but requires supplementary controls for enterprise-grade AI governance.

Comments
Please log in or register to join the discussion