Microsoft has open-sourced LiteBox, a library OS designed to sandbox applications and reduce host system attack surfaces through specialized North/South interfaces, targeting developers rather than end-users.
Microsoft has unveiled LiteBox, a new open-source library operating system that fundamentally changes how applications interact with host systems. Unlike traditional OS installations, LiteBox operates as a specialized runtime environment bundled directly with applications—not as a standalone operating system users would install or boot.
Core Architecture: North/South Interfaces
At its foundation, LiteBox implements a dual-interface architecture:
- North Interface: A Rust-based API layer (inspired by nix/rustix) that applications directly interact with
- South Interface: Platform-specific translation layer that communicates with the host OS (Windows/Linux)
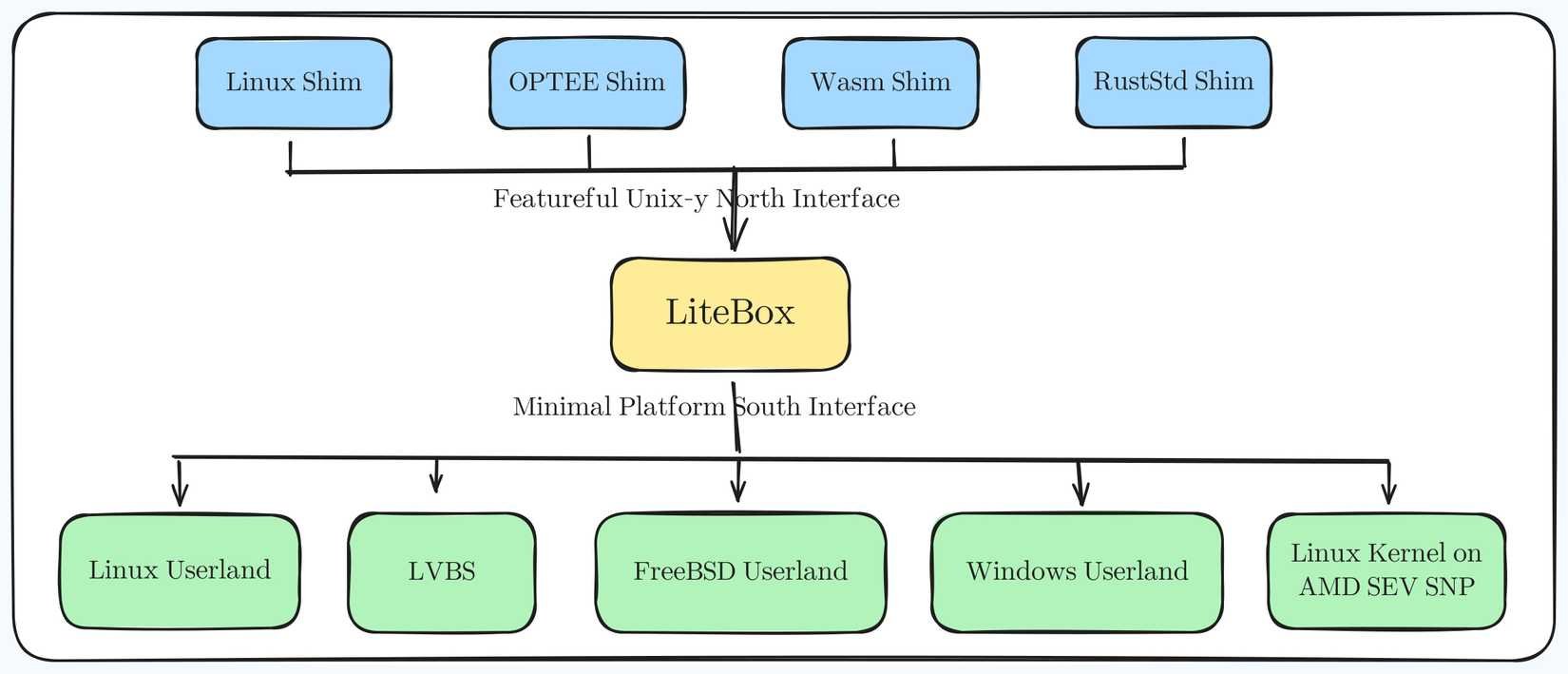 How LiteBox mediates between applications and host operating systems
How LiteBox mediates between applications and host operating systems
This design creates a secure intermediary layer where application system calls get translated through LiteBox before reaching the host OS. By minimizing direct access points, LiteBox drastically reduces the attack surface area available to potential exploits.
Developer-Centric Implementation
LiteBox targets specific developer use cases:
- Application Sandboxing: Bundling LiteBox with applications creates isolated execution environments, preventing compromised apps from affecting host systems
- Cross-Platform Compatibility: Developers write against the consistent North Interface while LiteBox handles OS-specific translations
- Kernel/Non-Kernel Flexibility: Works in both traditional kernel environments and specialized contexts like unikernels
Platform requirements are minimal—LiteBox only needs a compatible Rust toolchain (1.60+) and can target Windows 10/11 or modern Linux distributions. The library weighs under 2MB, imposing negligible overhead.
Relationship to WSL and Windows Ecosystem
While LiteBox shares Microsoft's broader interoperability vision with tools like Windows Subsystem for Linux, it serves a distinct purpose:
 Windows Terminal showing WSL integration - LiteBox operates at a different abstraction layer
Windows Terminal showing WSL integration - LiteBox operates at a different abstraction layer
Unlike WSL which provides full Linux environments, LiteBox enables granular control at the application level. Developers might use both technologies together—for example, running LiteBox-sandboxed applications within WSL containers for layered security.
Practical Implementation Considerations
For developers adopting LiteBox:
- Migration involves wrapping existing application entry points with LiteBox's North Interface
- Testing matrix must expand to cover all target South Interface platforms
- Memory management differs from traditional OS interactions—LiteBox handles resource allocation through its abstraction layer
- Debugging requires instrumentation through LiteBox's logging interfaces
The GitHub repository provides sample implementations showing how to bundle LiteBox with Rust applications. Early benchmarks show 5-8% runtime overhead versus native execution—a reasonable tradeoff for security-sensitive applications.
Strategic Implications
LiteBox represents Microsoft's continued investment in secure application isolation paradigms. While not a consumer-facing product, it could influence future Windows security models and cross-platform development frameworks. Developers working in finance, healthcare, or security-critical domains should evaluate how LiteBox's sandboxing could reduce vulnerability surfaces in distributed applications.
As library OS architectures gain traction, LiteBox offers a production-ready option that prioritizes minimal attack surfaces without sacrificing interoperability—provided developers embrace its paradigm shift from system-level to application-level OS abstraction.

Comments
Please log in or register to join the discussion