Microsoft introduces an automated script for exporting MITRE ATT&CK mappings from Sentinel analytic rules, enabling SOC teams to streamline threat detection coverage analysis across multi-cloud environments.
The New Automation Frontier in Cloud Security
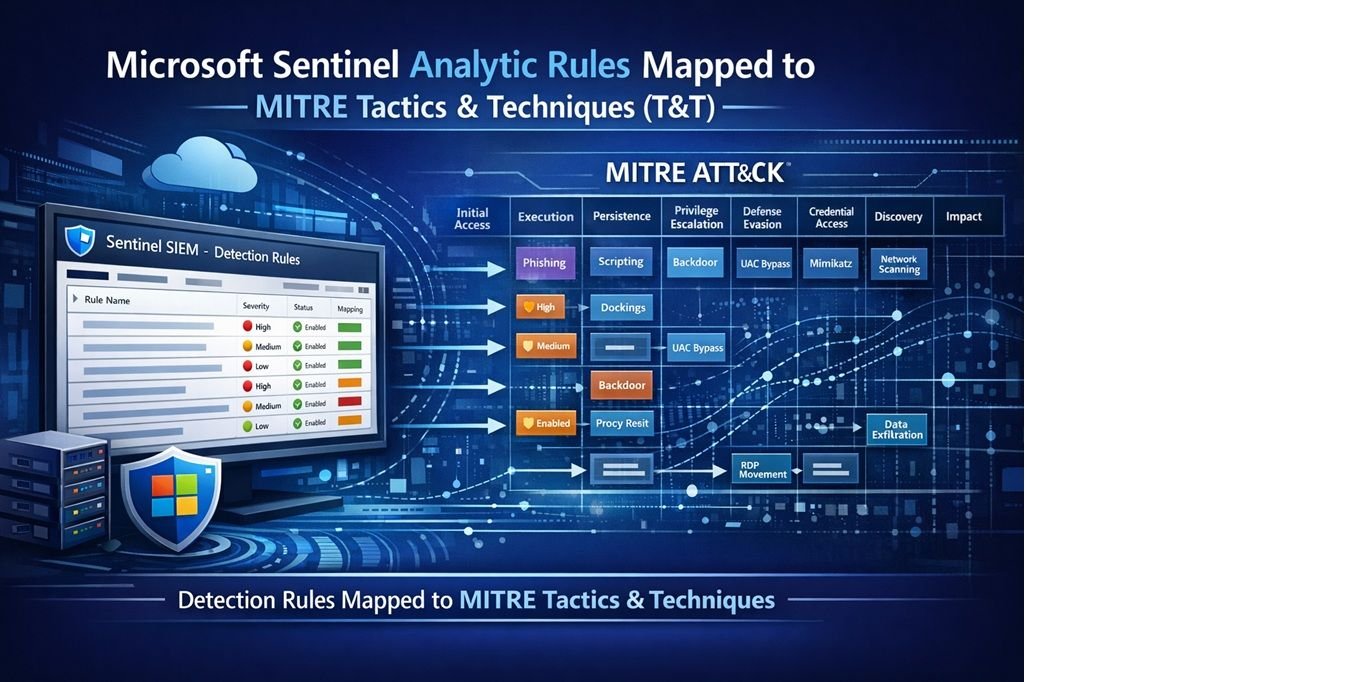
Microsoft has released a Bash script that automatically exports MITRE ATT&CK framework mappings from Microsoft Sentinel analytic rules into CSV format. This development addresses a critical need for security teams operating in complex, multi-cloud environments where visibility into detection coverage is paramount.
What Changed: From Manual to Automated Mapping
Previously, SOC analysts had to:
- Manually check each analytic rule for MITRE mappings
- Maintain spreadsheets for compliance reporting
- Visually inspect detection coverage gaps
The new script automates:
- Bulk extraction of Tactics (TA####) and Techniques (T####)
- Severity level reporting
- Rule enablement status
- KQL query exports
This aligns with Microsoft's broader strategy to enhance cloud-native security operations through automation.
Provider Comparison: ATT&CK Mapping Capabilities
| Platform | Automated Export | MITRE Visualization | Cross-Cloud Support | API Access |
|---|---|---|---|---|
| Microsoft Sentinel | ✅ (New Script) | Portal Only | Azure-First | REST API |
| AWS GuardDuty | ❌ | ❌ | AWS Native | Limited |
| Google Chronicle | Partial | Built-in Heatmaps | Multi-Cloud | GraphQL |
Key differentiators:
- Sentinel's new automation fills a critical gap in operational workflows
- Chronicle offers superior visualization but lacks full export capabilities
- GuardDuty remains focused on AWS-native threat detection
Business Impact for Multi-Cloud Organizations
For enterprises using multiple cloud providers, this automation enables:
- Unified Threat Coverage Analysis
- Compare detection capabilities across Azure/AWS/GCP
- Identify provider-specific coverage gaps
- Compliance Efficiency
- Generate audit-ready reports in minutes instead of days
- Maintain version-controlled detection catalogs
- Detection Engineering at Scale
- Benchmark against MITRE Engenuity
- Support purple team exercises across cloud boundaries
- Cost Optimization
- Eliminate redundant rules across cloud SIEMs
- Focus engineering efforts on high-risk ATT&CK techniques
Strategic Recommendations
- Implementation Best Practices
- Run the script as part of CI/CD pipelines
- Store outputs in Azure Storage for historical tracking
- Integrate with Power BI for executive dashboards
- Multi-Cloud Considerations
- Combine with AWS Security Hub findings
- Correlate with GCP Security Command Center alerts
- Roadmap Suggestions
- Push Microsoft to add sub-technique mapping
- Advocate for cross-provider ATT&CK benchmarking
This automation represents a significant step toward enterprise-grade threat-informed defense in multi-cloud environments. While other providers offer pieces of the puzzle, Microsoft's programmatic access to detection metadata gives organizations using Sentinel a strategic advantage in building mature, measurable security operations.
Featured image shows Microsoft Sentinel's analytics interface with MITRE ATT&CK mappings.

Comments
Please log in or register to join the discussion