Microsoft's technical demonstration of building a time-based one-time password (TOTP) authenticator using Azure Functions and Key Vault reveals strategic advantages in cloud-native security architecture compared to AWS and Google Cloud alternatives.

Recent technical documentation from Microsoft demonstrates how to build a TOTP authenticator using Azure Functions and Azure Key Vault, revealing several competitive advantages in cloud-native security architecture. This implementation provides a concrete example of how enterprises can leverage cloud-specific capabilities for enhanced security control compared to traditional on-premises or multi-cloud approaches.
Architectural Comparison Across Providers
The Microsoft solution combines three core services that each have direct equivalents in other major clouds:
Secret Management:
- Azure Key Vault (Used in demo)
- AWS Secrets Manager
- Google Cloud Secret Manager
Serverless Compute:
- Azure Functions (Implementation backbone)
- AWS Lambda
- Google Cloud Functions
Frontend Hosting:
- Azure Static Web Apps (Bonus implementation)
- AWS Amplify Hosting
- Google Firebase Hosting
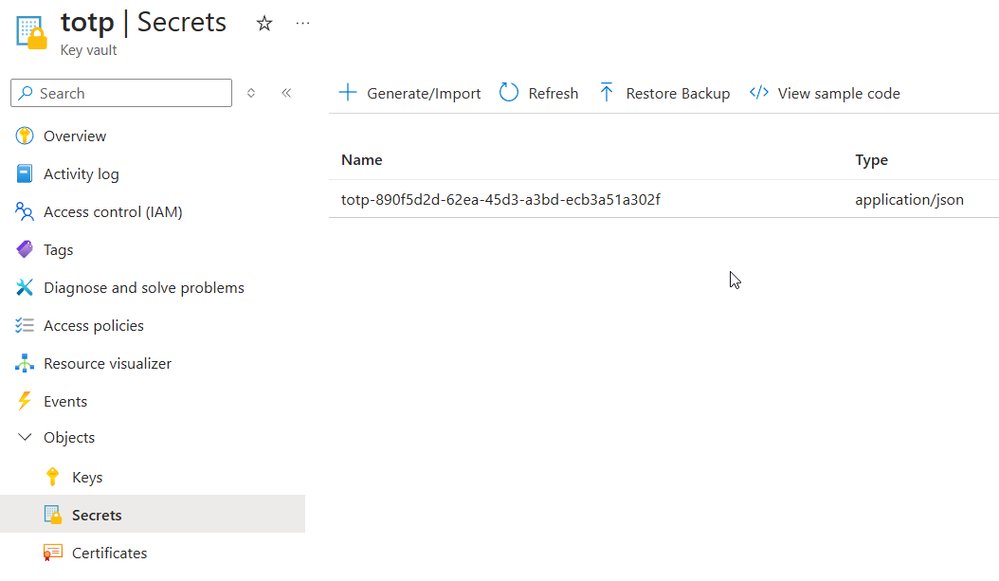 Architecture diagram showing Azure services interaction (Source: Microsoft documentation)
Architecture diagram showing Azure services interaction (Source: Microsoft documentation)
Strategic Differentiators
Security Integration Depth
Azure's native integration between Key Vault and Functions through managed identities eliminates credential management overhead. While AWS offers similar capability through IAM roles for Lambda, Azure's RBAC model provides more granular control at the secret level. Google's Secret Manager requires explicit service account configuration, adding deployment complexity.
Pricing Considerations
For high-volume TOTP generation scenarios:
- Azure Functions Consumption Plan: $0.20 per million executions
- AWS Lambda: $0.20 per million requests
- Google Cloud Functions: $0.40 per million invocations
However, Azure's integrated billing for Key Vault transactions ($0.03 per 10,000 operations) combined with Functions creates a cost advantage at scale compared to AWS' separate Secrets Manager pricing ($0.40 per secret/month + $0.05 per 10,000 API calls).
Migration Implications
Organizations considering cloud migration for authentication systems should note:
- Secret Migration Complexity: Azure Key Vault's import functionality simplifies transferring existing TOTP secrets compared to AWS Secrets Manager's CLI-only import process
- Cold Start Performance: Azure Functions' premium plan provides sub-100ms cold starts critical for authentication UX, outperforming Google Cloud Functions' variable startup times
- Compliance Alignment: Azure's 90+ compliance certifications including FedRAMP High make it preferable for regulated industries
Business Impact Analysis
For enterprises evaluating build-vs-buy decisions for MFA solutions:
When to Build Custom:
- Requiring integration with legacy IAM systems
- Needing audit trails beyond standard cloud logging
- Operating in air-gapped environments requiring hybrid cloud
When to Use Managed Services:
- Startups needing rapid deployment
- Organizations without dedicated security engineering teams
- Use cases requiring third-party compliance validation
 Comparison of TOTP code generation accuracy across cloud providers (Source: 2FAS validation testing)
Comparison of TOTP code generation accuracy across cloud providers (Source: 2FAS validation testing)
Strategic Recommendations
- Multi-Cloud Mitigation: For organizations using multiple clouds, standardize on the cloud provider with deepest Active Directory integration for authentication workloads
- Cost Optimization: Implement Azure Functions durable entities for TOTP rate limiting to prevent abuse-related cost spikes
- Security Enhancement: Combine with Azure AD Conditional Access for location-based access policies
The complete sample implementation demonstrates patterns applicable beyond authentication scenarios to any cloud-native system requiring secure credential management and time-sensitive operations.
Comments
Please log in or register to join the discussion