Chinese state-sponsored hackers have enhanced their CoolClient malware with browser credential theft, clipboard monitoring, and novel evasion techniques targeting government organizations across Asia.

The Chinese state-sponsored threat group Mustang Panda (aka Earth Preta) has significantly upgraded its CoolClient backdoor with sophisticated data theft capabilities, according to new research from Kaspersky. The updated malware now targets browser credentials, monitors clipboard contents, and leverages legitimate cloud services for stealthy data exfiltration.
Evolution of a Persistent Threat
CoolClient has served as Mustang Panda's secondary backdoor since 2022, operating alongside better-known tools like PlugX and LuminousMoth. Recent campaigns have targeted government agencies in:
- Myanmar
- Mongolia
- Malaysia
- Russia
- Pakistan
The attackers deployed the malware through compromised installations of legitimate software from Sangfor Technologies, a Chinese cybersecurity and cloud infrastructure provider. This marks a shift from previous delivery methods that abused signed binaries from Bitdefender, VLC Media Player, and Ulead PhotoImpact via DLL side-loading.
Technical Capabilities Revealed
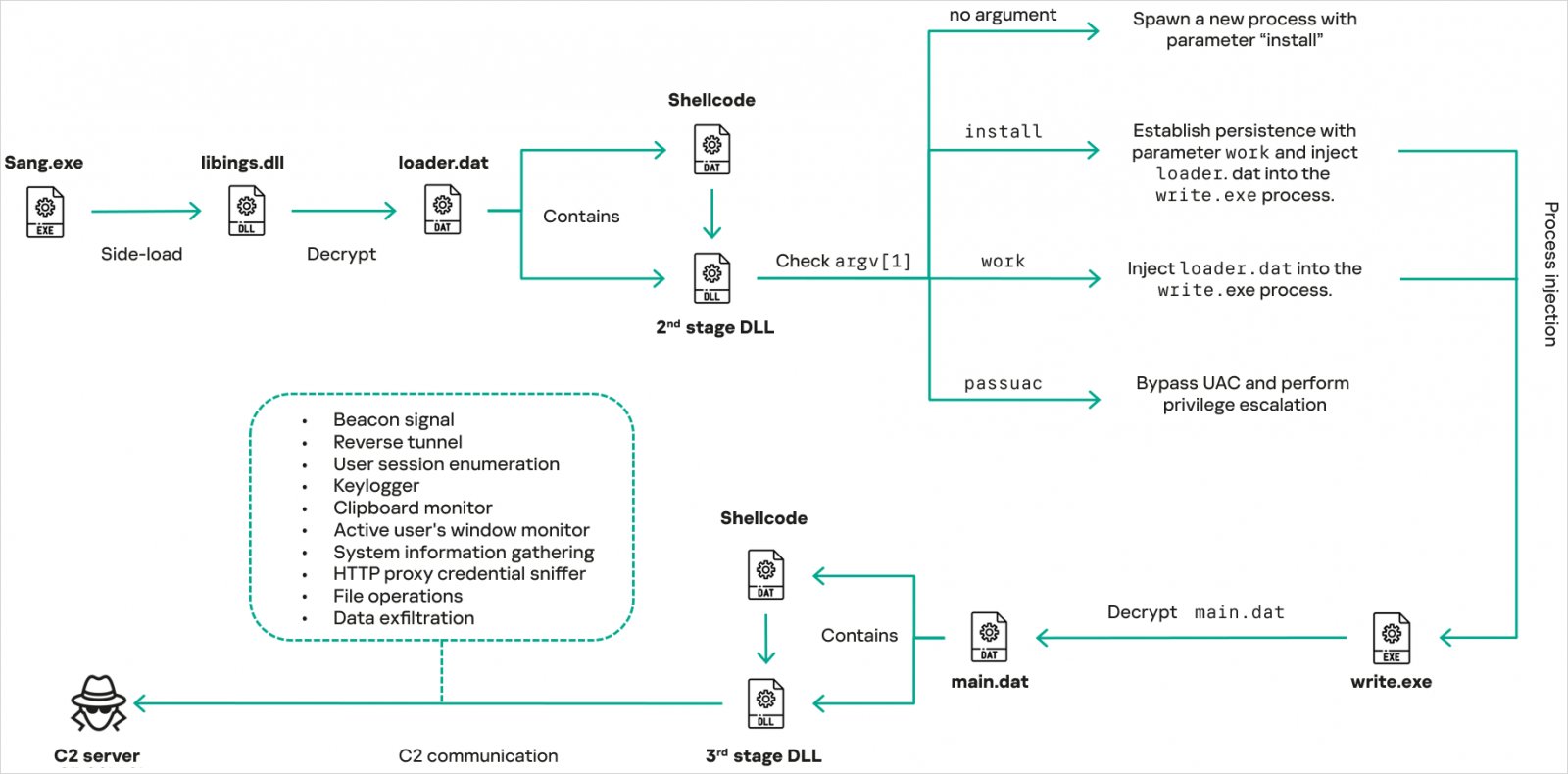
The updated CoolClient employs a multi-stage execution process using encrypted .DAT files, achieving persistence through:
- Windows Registry modifications
- Service creation
- Scheduled tasks
- UAC bypass techniques
Its core functionality resides in a DLL embedded within main.dat, which manages:
- System profiling (OS version, RAM, network config)
- File operations
- Keylogging
- TCP tunneling
- In-memory plugin execution
New Attack Modules
Kaspersky researchers identified three major upgrades:
1. Browser Credential Theft Three specialized infostealers target:
- Variant A: Chrome
- Variant B: Edge
- Variant C: All Chromium-based browsers
The malware copies login data to local temporary files before exfiltration.
2. Enhanced Monitoring
- Clipboard content tracking
- Active window title logging
- HTTP proxy credential harvesting via raw packet inspection
3. Expanded Plugin Ecosystem
- Remote Shell Plugin: Hidden cmd.exe execution with C2 channel control
- Service Management Plugin: Full Windows service manipulation
- Advanced File Plugin: Network drive mapping, ZIP compression, and file search
Evasion Techniques
Mustang Panda now uses hardcoded API tokens for legitimate services including:
- Google Drive
- Pixeldrain
to blend exfiltrated data with normal traffic, bypassing traditional data loss prevention systems.
Operational Context
This upgrade follows recent Mustang Panda activity including:
- Kernel-mode loader deployment for ToneShell backdoor (December 2025)
- Tenfold increase in attacks on Taiwan's energy sector (January 2026)
Taiwan's National Security Bureau recently ranked the group among the most prolific threats to its critical infrastructure.
Mitigation Strategies
Security leaders should implement:
- Application Control: Block execution from Temp directories and unsigned paths
- Network Monitoring: Detect anomalous connections to cloud storage APIs
- Browser Protection: Regular credential rotation and session management
- DLL Verification: Validate signed binaries against vendor hashes
- Privilege Management: Remove local admin rights where possible
"CoolClient's evolution shows how state-sponsored actors increasingly weaponize legitimate tools and cloud services," notes Kaspersky researcher Ivan Shevchenko. "Defenders need layered monitoring that combines process behavior analysis with cloud egress inspection."
Organizations in Mustang Panda's target sectors should review their detection capabilities for:
- Unusual service creations
- Scheduled tasks modifying system binaries
- Unexpected network drives appearing in file operations
Kaspersky expects to publish full technical analysis of CoolClient's new rootkit capabilities in the coming weeks.

Comments
Please log in or register to join the discussion