A maximum-severity vulnerability dubbed 'Ni8mare' is putting nearly 60,000 exposed n8n workflow automation instances at risk of complete takeover. The flaw allows unauthenticated attackers to hijack servers, steal credentials, and potentially execute arbitrary commands. Security researchers warn that the vulnerability is being actively exploited in the wild, urging immediate patching.
A critical security vulnerability tracked as CVE-2026-21858, and nicknamed "Ni8mare," is threatening nearly 60,000 exposed n8n instances. n8n is an open-source workflow automation platform that allows users to connect different applications and services via pre-built connectors and a visual, node-based interface to automate repetitive tasks without writing code. The automation platform is widely used in AI development to automate data ingestion and build AI agents and RAG pipelines. It has over 100 million pulls on Docker Hub and over 50,000 weekly downloads on npm.
The Vulnerability: A Technical Breakdown
The Ni8mare flaw stems from an improper input validation weakness that allows remote, unauthenticated attackers to take control over locally deployed n8n instances after gaining access to files on the underlying server. According to security researchers at Cyera who discovered the vulnerability, it is a content-type confusion issue in how n8n parses data. This confusion can be exploited to:
- Expose secrets stored on the instance
- Forge session cookies to bypass authentication
- Inject sensitive files into workflows
- Execute arbitrary commands
The n8n team explained, "A vulnerable workflow could grant access to an unauthenticated remote attacker. This could potentially result in exposure of information stored on the system and may enable further compromise depending on deployment configuration and workflow usage."
Who Is Affected?
An n8n instance is potentially vulnerable if it has an active workflow with a Form Submission trigger accepting a file element, and a Form Ending node returning a binary file. Since n8n serves as a central automation hub, it often stores API keys, OAuth tokens, database credentials, cloud storage access, CI/CD secrets, and business data, making it an attractive target for threat actors.
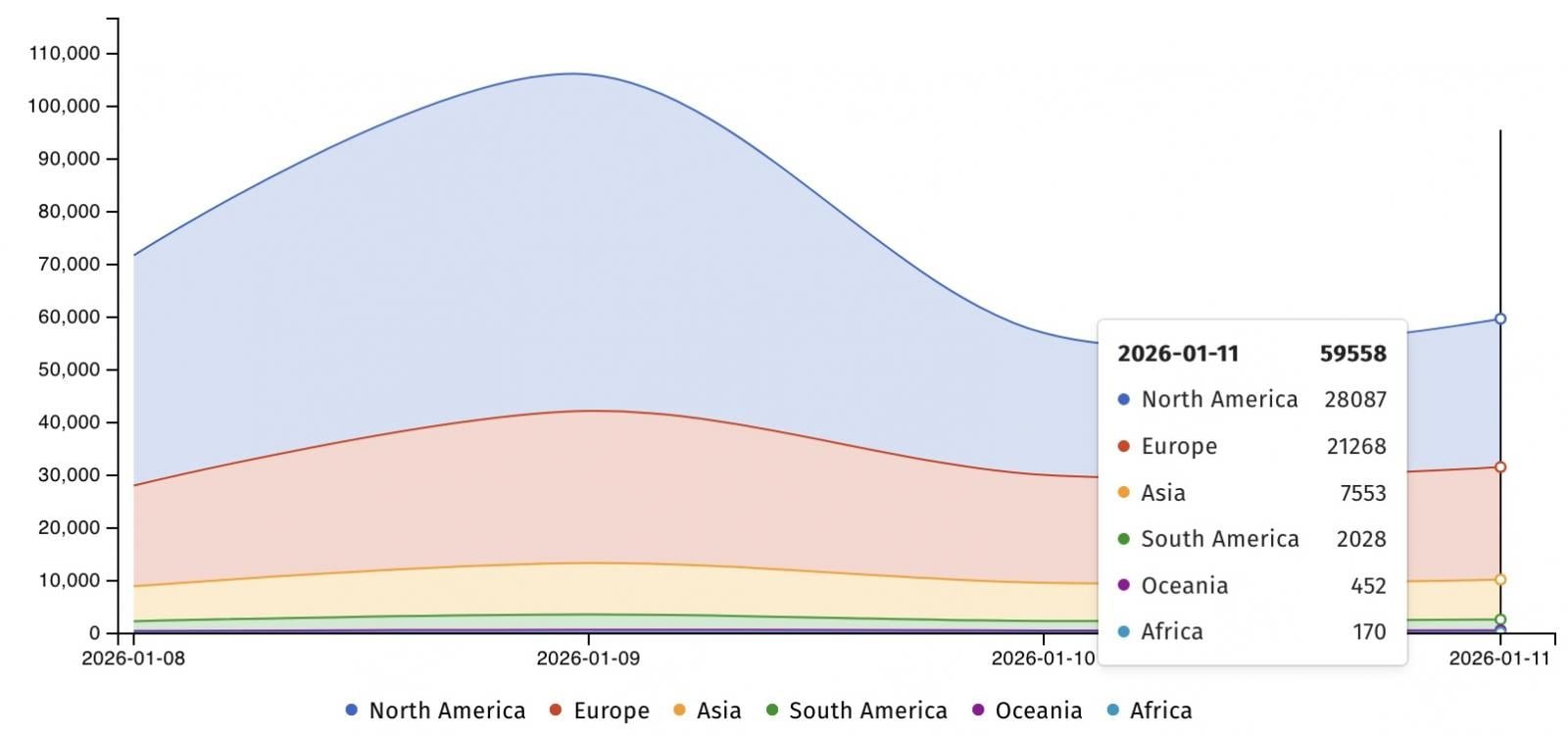
The Scale of Exposure
Over the weekend, the Internet security watchdog group Shadowserver found 105,753 unpatched instances exposed online and 59,558 still exposed on Sunday. The United States had over 28,000 IPs affected, while Europe had over 21,000.
Remediation and Mitigation
To block potential attacks, admins are advised to upgrade their n8n instances to version 1.121.0 or later as soon as possible. While n8n developers said that there is no official workaround available for Ni8mare, admins who can't immediately upgrade may be able to block potential attacks by restricting or disabling publicly accessible webhook and form endpoints.
The n8n team also provides a workflow template for admins who want to scan their instances for potentially vulnerable workflows. For more information on the vulnerability and patching instructions, visit the official n8n security advisory.
Broader Implications
This vulnerability highlights the risks associated with widely-used automation platforms that centralize sensitive data and access. As organizations increasingly rely on these tools for AI development and workflow automation, securing them becomes paramount. The Ni8mare flaw serves as a reminder that even open-source platforms with large user bases are not immune to critical security issues.
Conclusion
The Ni8mare vulnerability is a severe threat that requires immediate attention from n8n administrators. Patching to version 1.121.0 or later is the only sure way to mitigate the risk. For those unable to patch immediately, restricting access to vulnerable endpoints is a temporary measure. The widespread exposure of n8n instances underscores the importance of regular security audits and prompt patching in the DevOps and AI toolchain.
Comments
Please log in or register to join the discussion