A sophisticated malware framework targeting Linux cloud infrastructure has been uncovered, featuring cloud-native evasion techniques and modular plugins for persistent cyber espionage.
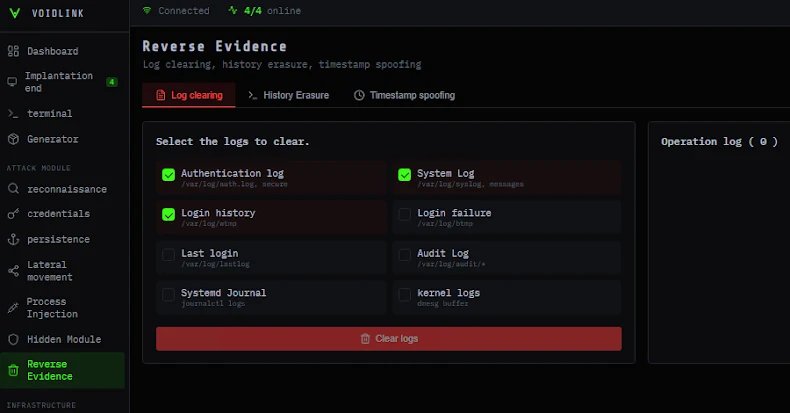
Security researchers have identified a previously undocumented malware framework targeting Linux-based cloud infrastructure, signaling a strategic shift toward compromising foundational cloud systems. Dubbed VoidLink by Check Point Research, this advanced toolkit demonstrates concerning evolution in cloud-focused cyber threats.
Modular Cloud-First Architecture
VoidLink operates as a cloud-native implant written in Zig, with architecture specifically engineered for containerized environments. Its core innovation lies in a custom Plugin API modeled after Cobalt Strike's Beacon Object Files, supporting over 30 interchangeable modules. This modular design enables attackers to dynamically adapt functionality based on objectives.
"The framework includes multiple cloud-focused capabilities and is engineered to operate reliably in cloud and container environments over extended periods," Check Point analysts noted. The malware automatically detects major cloud platforms including AWS, Azure, GCP, Alibaba Cloud, and Tencent Cloud, altering its behavior when running in Docker containers or Kubernetes pods.
Technical Capabilities
Key features make VoidLink particularly dangerous in cloud environments:
- Environment Awareness: Detects virtualization, container platforms, and security controls
- Stealth Mechanisms: Uses LD_PRELOAD hijacking, eBPF programs, and kernel modules for process hiding
- Credential Harvesting: Collects cloud credentials, SSH keys, Git configurations, and browser data
- Lateral Movement: Includes SSH-based worm propagation capabilities
- Self-Defense: Features runtime code encryption, debugger detection, and self-destruct triggers

The malware's dashboard interface allows operators to remotely manage compromised hosts, create customized payloads, and orchestrate attack phases from reconnaissance to data exfiltration. Its 37 plugins enable container escapes, Kubernetes privilege escalation, log manipulation, and timestamp forging.
Defensive Recommendations
Based on analysis of VoidLink's techniques, security teams should implement these protective measures:
Harden Container Environments:
- Enforce strict resource constraints via Kubernetes Pod Security Policies
- Regularly audit container images using tools like Trivy or Clair
- Implement container runtime protection with Falco or Aqua Security
Strengthen Credential Management:
- Rotate cloud access keys frequently using AWS IAM or Azure Key Vault
- Implement temporary credentials via AWS STS
- Enforce multi-factor authentication for all cloud accounts
Enhance Monitoring:
- Deploy runtime security agents that monitor eBPF and kernel module activity
- Configure cloud logging pipelines to detect unusual credential access patterns
- Establish baselines for container behavior using tools like Sysdig Secure
Network Protections:
- Implement microsegmentation to contain lateral movement
- Block unnecessary outbound DNS/ICMP traffic that could signal tunneling
- Monitor SSH connection patterns between cloud instances
Check Point's analysis suggests Chinese-affiliated actors likely developed VoidLink, noting: "The developers demonstrate high technical expertise across multiple programming languages... enabling advanced solutions for operating in cloud environments with adaptive stealth."
Cloud infrastructure teams should prioritize updating security configurations and validating detection capabilities against these emerging Linux-focused threats. Continuous monitoring of cloud credential usage and container behavior remains critical for early detection of such sophisticated frameworks.

Comments
Please log in or register to join the discussion