Researchers propose a new trusted third-party system for internet geolocation that balances service functionality with user privacy, enabling granular location disclosure while addressing sovereignty concerns.
The pervasive nature of geolocation on today's internet presents users with an impossible choice: sacrifice precise location privacy for service functionality, or embrace privacy tools that fundamentally break essential online services. This dilemma stems from the limitations of existing geolocation methods. Device-based GPS provides high accuracy but reveals excessive detail, while IP-based geolocation—though less intrusive—suffers declining accuracy due to widespread adoption of VPNs and privacy features like iCloud Private Relay. As these privacy tools become mainstream, they inadvertently undermine services requiring even coarse location data for regional compliance, content personalization, and security protocols.
This erosion of functional geolocation represents more than a technical inconvenience; it signals systemic failure. Current solutions treat location as binary—either fully disclosed or completely hidden—despite most services needing only approximate regional data. The resulting tension between utility and privacy grows increasingly untenable, demanding architectural reconsideration rather than incremental fixes.
A Verified Location Framework
Researchers from École Normale Supérieure de Lyon propose a certificate-based mechanism that operates through trusted third-party authorities. This system establishes a chain of verification where:
- Location Token Issuance: Devices periodically obtain encrypted tokens from certified authorities, derived from reliable signals (GPS, cellular triangulation)
- Service Requirements Declaration: Services present cryptographically signed certificates specifying their minimum required location accuracy
- Granular Disclosure: User devices verify service certificates and disclose only location tokens meeting the minimum precision threshold
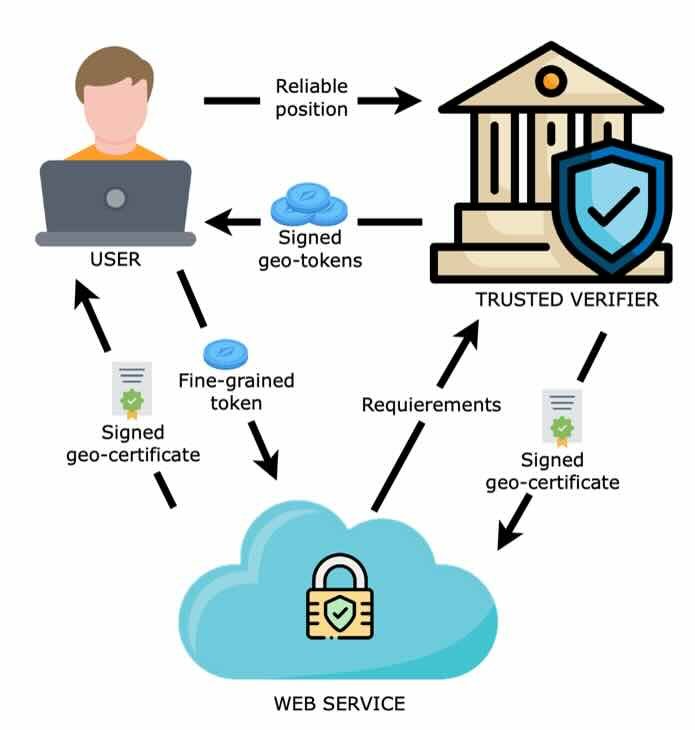
The architecture deliberately mirrors HTTPS certificate validation, enabling integration with existing security protocols without disrupting user experience. By decoupling location verification from disclosure, the system creates privacy-preserving granularity—a restaurant app might receive neighborhood-level verification while a banking service obtains city-level confirmation. Crucially, users maintain centralized control over which service categories may request location data at all.
Sovereignty and Ecosystem Alignment
This hierarchical trust model creates significant geopolitical advantages. Nations can operate sovereign certification authorities, ensuring citizens' precise location data never crosses borders unnecessarily—a critical consideration for data localization regulations. The framework simultaneously aligns incentives across the internet ecosystem:
- Users gain meaningful control without sacrificing functionality
- Services receive verified location data with accuracy guarantees
- Platforms (browsers/OS) position themselves as genuine privacy stewards
- Governments preserve jurisdictional control over sensitive data
Implementation challenges remain, particularly regarding authority governance. While private entities like CDNs could operate certification services, national governments possess strong incentives to maintain sovereign control. The research team acknowledges this unresolved question while emphasizing the system's adaptability to multiple governance models.
The proposed architecture represents more than technical refinement—it reconceives geolocation as a negotiated agreement rather than unilateral data extraction. By establishing accountability layers through cryptographic verification and granular disclosure thresholds, this framework could restore eroding trust in location-dependent services while respecting fundamental privacy boundaries. As the team advances toward prototyping and standardization, their work invites broader industry collaboration to rebuild this crumbling infrastructure pillar.


Comments
Please log in or register to join the discussion