A software archaeologist bypassed a 40-year-old parallel port dongle protecting RPG II compiler software through disassembly and patching, revealing surprisingly simple security mechanisms.
Legacy systems continue to haunt modern technology migrations, as demonstrated by a recent case where a 1980s-era copy protection dongle blocked access to critical accounting software. Dmitry Brant encountered this challenge while helping an accounting firm migrate from a Windows 98 machine running RPG II software that required a hardware dongle attached to the parallel port. The discovery highlights how obsolete security measures can complicate digital preservation efforts decades later.

The worn dongle with partial markings that protected Software West's RPG II compiler
The accounting software, originally developed for IBM mainframes before being ported to MS-DOS, relied on a compiler that injected copy-protection logic into every executable it produced. When launched without the dongle, programs like the Source Entry Utility (SEU.EXE) displayed abrupt error messages and exited. Analysis revealed these executables contained a dedicated routine communicating with the parallel port hardware.
Using the Reko decompiler, Brant examined the 16-bit executables and discovered a compact routine in segment 0800 that handled dongle communication. Surprisingly, this routine didn't accept any input parameters and always produced the same output when executed - a critical vulnerability. The disassembly showed the code:
- Detected the primary parallel port address
- Performed write/read operations with the port
- Accumulated results in BH and BL registers
- Returned a fixed 16-bit value in BX
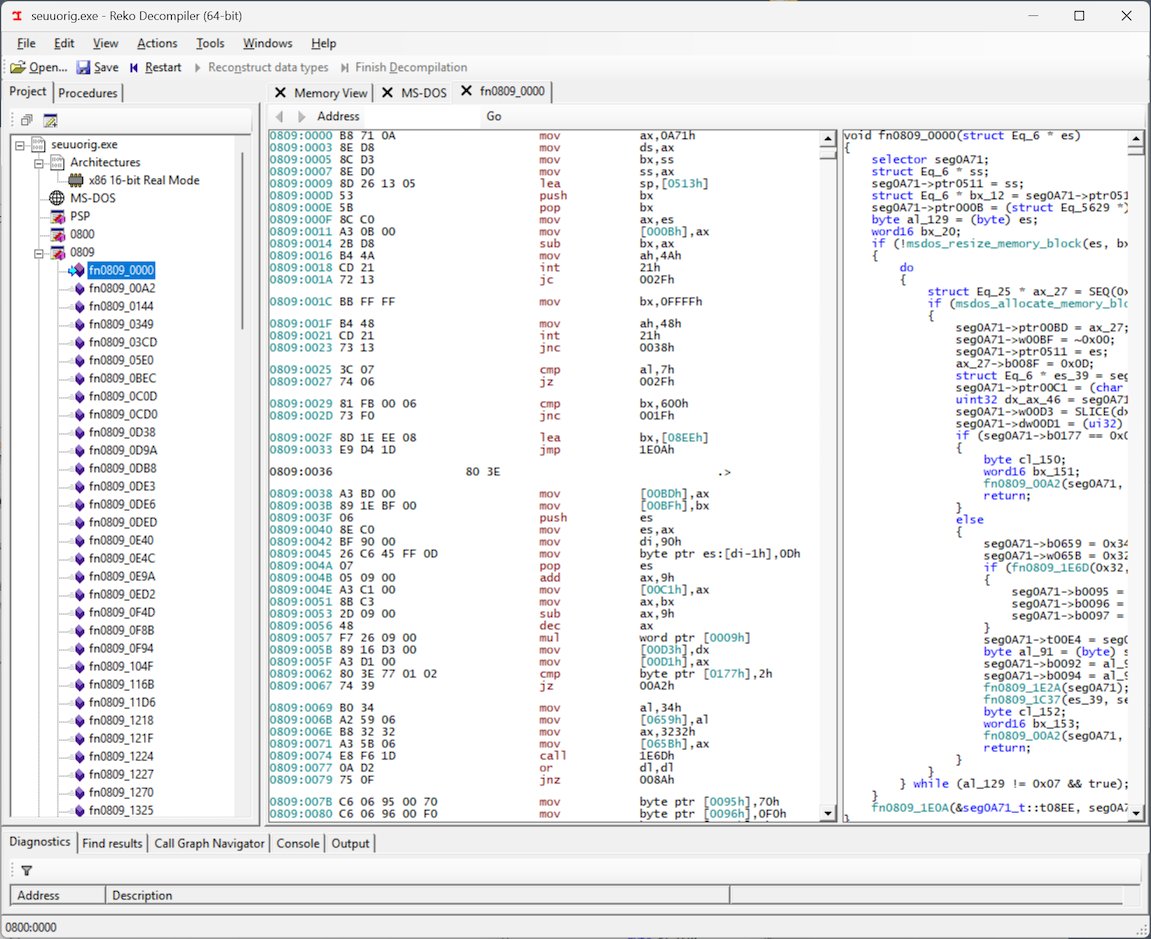
Reko decompiler showing the parallel port communication routine
The protection's weakness became apparent when Brant realized the routine consistently returned values where BH was always 0x76. This reduced the possible valid combinations to just 256 options (00-FF in BL). A brute-force script tested each possibility in DosBox, quickly identifying 0x06 as the correct value - making the full magic number 0x7606.
With this knowledge, patching became straightforward. Replacing the first four bytes of the routine with MOV BX, 7606h followed by RETF bypassed the dongle check entirely. Notably, the compiler (RPGC.EXE) contained the same routine and would propagate this patched protection logic to any programs it compiled.
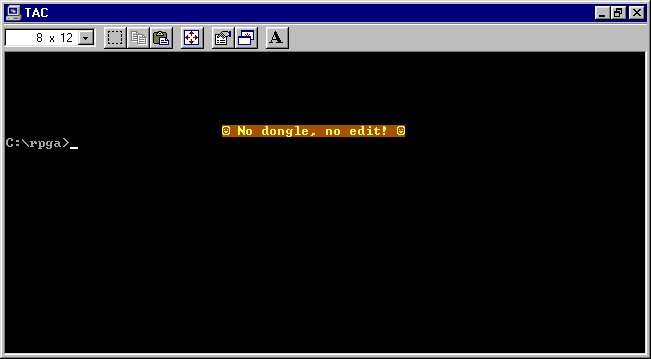
The SEU editor's dongle error message that initiated the investigation
This case raises questions about early copy protection effectiveness. Despite patent protections and hardware implementation, the security relied entirely on a static response value. Some argue such measures were primarily psychological deterrents rather than robust security, while others note they reflected technical constraints of the era. Software historian Laine Nooney observes that 1980s dongles often prioritized low manufacturing cost over sophisticated security.
The RPG II compiler software, now freed from its hardware dependency, represents a significant artifact in computing history. Brant plans to preserve and distribute the compiler after removing sensitive information, noting that copies appear unavailable elsewhere. This case underscores how reverse engineering can rescue legacy systems while revealing fascinating insights about early software protection methodologies.
RPG II software running in a DOS window on Windows 98

Comments
Please log in or register to join the discussion