A new campaign attributed to the Russian threat group 'Void Blizzard' is targeting Ukrainian Defense Forces officials through fake charity websites and messaging apps, delivering an updated version of the PluggyApe backdoor malware.
Ukrainian Defense Forces officials faced a sophisticated malware campaign between October and December 2025 that exploited charitable giving themes to compromise their systems. The attacks delivered a backdoor called PluggyApe and are attributed with medium confidence to the Russian threat group known as 'Void Blizzard' or 'Laundry Bear.'

This same threat actor gained notoriety in 2024 for breaching the Dutch police's internal systems and stealing sensitive officer information. Laundry Bear consistently targets NATO member states in operations aligned with Russian geopolitical interests, focusing on data theft from files and email systems.
Attack Chain: From Charity Lure to Backdoor
The campaign begins with instant messages sent through Signal or WhatsApp. Recipients receive messages directing them to websites allegedly operated by charitable foundations. These sites prompt victims to download password-protected archives containing purported documents of interest.
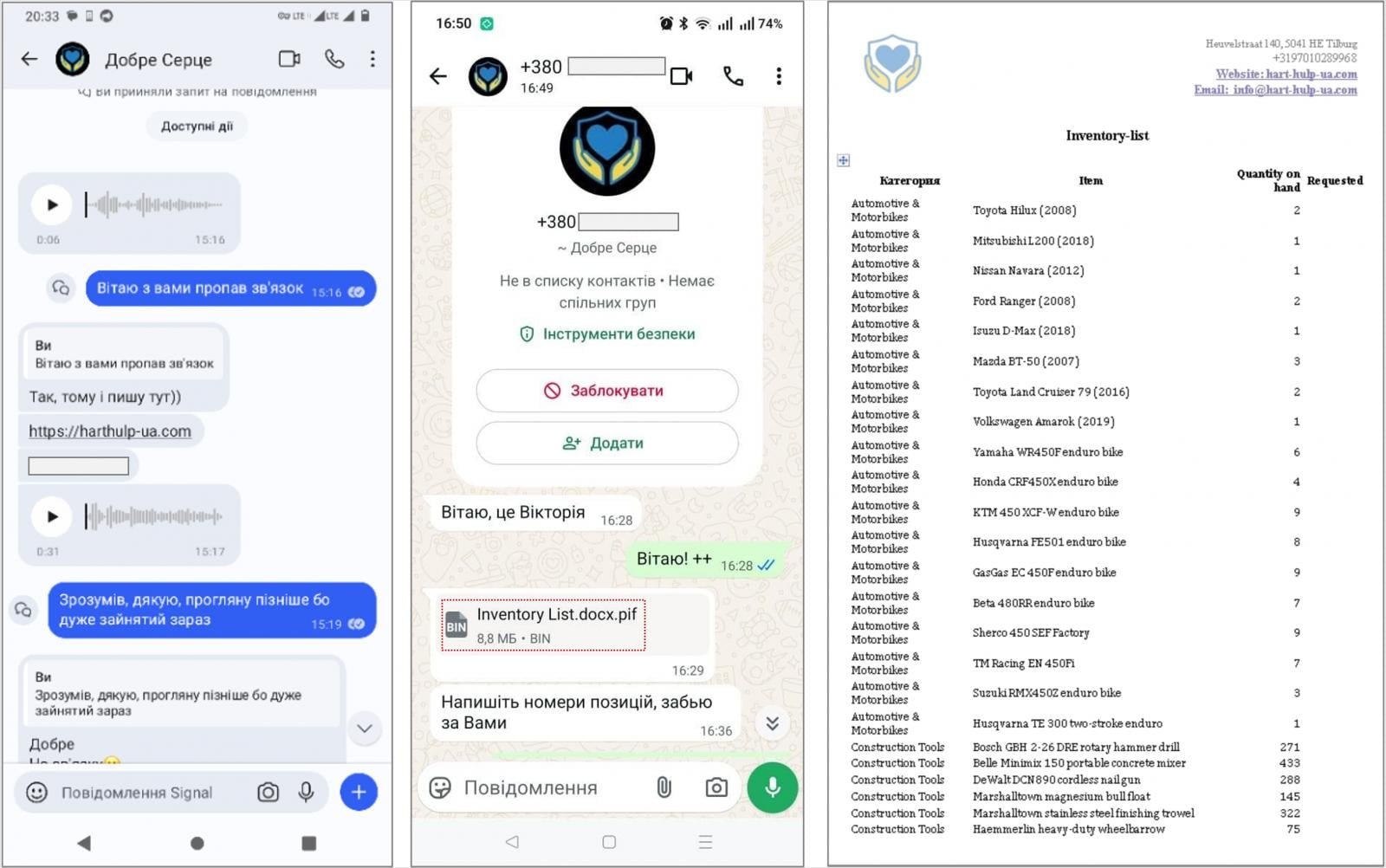
However, the archives contain executable PIF files with names like .docx.pif and the PluggyApe payload. In some variations, attackers send the malicious files directly through messaging apps without the intermediate website visit.
The PIF file is actually an executable created with PyInstaller, an open-source tool that bundles Python applications into single executable packages containing all required dependencies. This approach helps the malware run on target systems without requiring Python to be installed.
PluggyApe Version 2: Enhanced Evasion
PluggyApe functions as a backdoor that performs initial host profiling, sends system information plus a unique victim identifier to attackers, then awaits code execution commands. It establishes persistence through Windows Registry modifications.
Earlier PluggyApe campaigns used .pdf.exe extensions for the loader. Starting in December 2025, the threat actors switched to PIF files and released PluggyApe version 2, which includes significant improvements:
- Better obfuscation to evade detection
- MQTT-based communication for C2 traffic (unusual for malware, as MQTT is typically used for IoT device communication)
- Additional anti-analysis checks to thwart security researchers
A particularly clever technique involves fetching command-and-control addresses from external sources like rentry.co and pastebin.com rather than hardcoding them. The C2 addresses are published in base64-encoded form, allowing attackers to update their infrastructure quickly if domains get blocked or taken down.
Mobile Devices: The New Front Line
CERT-UA emphasizes that mobile devices have become prime targets for these attacks. Organizations often provide less monitoring and protection for phones and tablets compared to traditional endpoints, creating a security gap that attackers exploit.
The threat actors demonstrate impressive operational preparation. They use compromised accounts or phone numbers from Ukrainian telecommunication operators and communicate in fluent Ukrainian, sometimes including audio and video calls. As CERT-UA explains, "The attacker may demonstrate detailed and relevant knowledge about the individual, the organization, and the specifics of its operations."
This level of social engineering makes detection extremely difficult, as the initial contact appears completely legitimate.
Technical Indicators and Defense
Organizations should monitor for:
- Files with double extensions like
.docx.pifor.pdf.exe - PyInstaller-created executables from untrusted sources
- Registry modifications for persistence
- Network traffic to rentry.co, pastebin.com, or similar paste services fetching base64-encoded data
- Unusual MQTT traffic patterns from Windows systems
CERT-UA has published a complete list of indicators of compromise, including deceptive websites posing as charity portals, in their full report.
Broader Context: State-Sponsored Cyber Operations
This campaign reflects the evolving nature of state-sponsored cyber operations. Rather than relying solely on technical exploits, Russian threat actors increasingly combine social engineering with legitimate infrastructure. By using compromised operator accounts and fluent local language communication, they bypass traditional security awareness training that focuses on obvious grammar mistakes or foreign-language lures.
The shift to MQTT-based C2 communication represents an interesting technical evolution. While most malware uses HTTP/HTTPS or custom protocols, MQTT provides a lightweight publish-subscribe model that can blend into network traffic more easily, especially in environments with IoT devices.
For Ukrainian organizations and other potential targets of similar campaigns, the key defense lies in treating mobile device security with the same rigor as traditional endpoints, implementing strict controls on file downloads from messaging apps, and training personnel to verify charity solicitations through separate, trusted channels rather than clicking links in unsolicited messages.
The full CERT-UA report contains additional technical details and IoCs for security teams to implement in their detection rules.

Comments
Please log in or register to join the discussion