Ukraine's CERT-UA exposes sophisticated attacks leveraging instant messaging platforms to deliver malware against defense personnel.
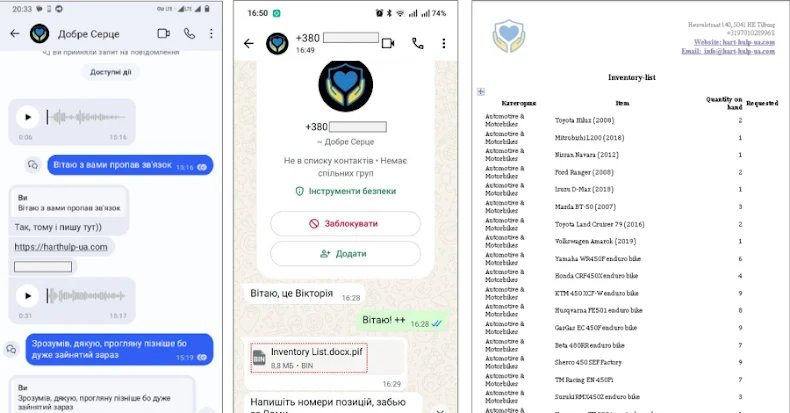
The Computer Emergency Response Team of Ukraine (CERT-UA) has uncovered a sophisticated malware campaign targeting Ukrainian defense forces between October and December 2025. Dubbed PLUGGYAPE, this Python-based backdoor infiltrates systems through compromised Signal and WhatsApp communications, marking a concerning evolution in Russian cyber operations against Ukrainian military infrastructure.
Attack Methodology: Trusted Platforms Turned Weapons
The Russian hacking group Void Blizzard (also tracked as UAC-0190 or Laundry Bear) orchestrated attacks by impersonating charity organizations. Targets received messages containing malicious links to domains like harthulp-ua[.]com and solidarity-help[.]org. These redirected users to password-protected archives containing PyInstaller-generated executables that deployed PLUGGYAPE.
CERT-UA analysts observed attackers demonstrating detailed knowledge of targets' organizations and operations, using Ukrainian phone numbers and native-language communication to establish credibility. Audio and video calls were occasionally employed to enhance deception. The agency noted: "Widely used messengers available on mobile devices and personal computers are de facto becoming the most common channel for delivering software tools for cyber threats."
Technical Evolution of PLUGGYAPE
Recent PLUGGYAPE variants feature enhanced anti-analysis capabilities:
- Environment checks to prevent execution in virtualized systems
- WebSocket and MQTT protocols for command-and-control (C2) communications
- Dynamic C2 retrieval from paste services like rentry[.]co and pastebin[.]com
The malware fetches base64-encoded C2 addresses from these public platforms, enabling real-time infrastructure updates when servers are disrupted. The December 2025 update added MQTT protocol support, providing attackers with redundant communication channels and improved operational resilience.
Related Campaigns Targeting Ukrainian Infrastructure
CERT-UA simultaneously reported two additional threat clusters:
- UAC-0239 deployed FILEMESS (a Go-based stealer) and OrcaC2 framework via VHD attachments, harvesting sensitive documents and enabling remote system control.
- UAC-0241 used ZIP archives delivering LNK files that triggered HTA execution, ultimately deploying password-stealing tool LaZagne and GAMYBEAR backdoor against educational institutions.
Practical Defense Recommendations
For organizations handling sensitive defense operations:
- Verify charity communications: Independently confirm donation requests through official channels before engaging
- Restrict script execution: Block arbitrary PowerShell/mshta.exe executions via application control policies
- Monitor paste sites: Deploy solutions to detect organizational mentions on services like Pastebin
- Network segmentation: Isolate critical systems from general messaging platforms
- Behavioral analysis: Implement endpoint detection that flags PyInstaller artifacts and abnormal WebSocket/MQTT traffic
CERT-UA emphasizes that attackers increasingly leverage legitimate infrastructure and localized social engineering. Continuous security awareness training remains critical, particularly regarding unexpected messages—even from seemingly trustworthy sources.
For ongoing threat intelligence, monitor official CERT-UA advisories at cert.gov.ua.

Comments
Please log in or register to join the discussion