Scammers are exploiting expired domains to hijack legitimate Snap publisher accounts, pushing malicious updates to previously trusted applications in Canonical's software repository.
The Evolving Threat to Snap Security
Scammers have escalated attacks against Canonical's Snap Store by hijacking expired domains belonging to legitimate application publishers. This allows them to bypass security checks and push malware through previously trusted software channels - a significant evolution from earlier tactics.
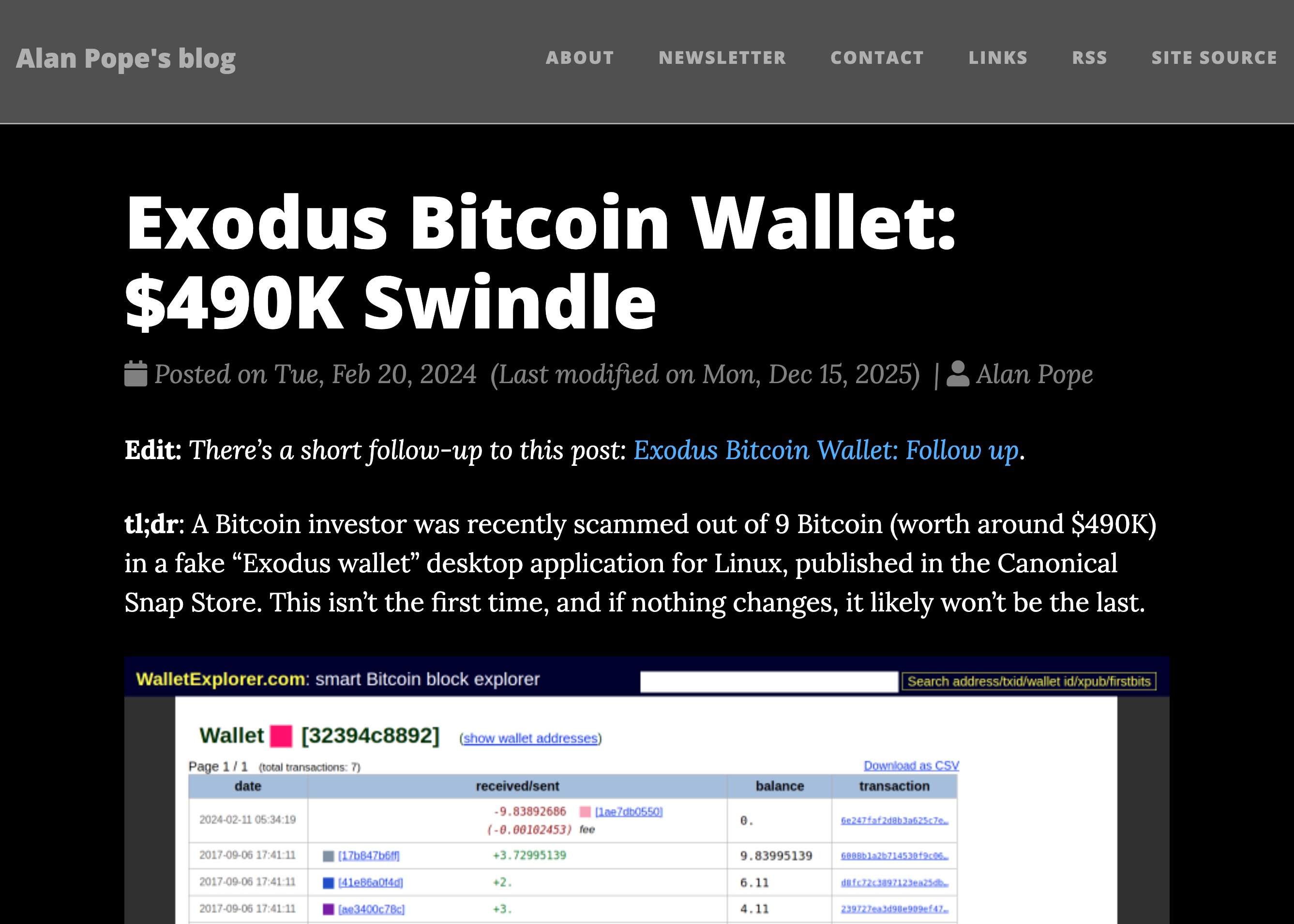 Previous malware incidents in the Snap Store were just the beginning
Previous malware incidents in the Snap Store were just the beginning
How the Attack Works
- Domain Expiration: Legitimate publishers let domain registrations lapse
- Hostile Takeover: Scammers register expired domains
- Account Hijacking: Attackers reset publisher credentials using domain-controlled email
- Malicious Updates: Previously trusted snaps receive malware-laden revisions
At least two domains (storewise.tech and vagueentertainment.com) have been compromised this way, with more likely undiscovered.
Anatomy of a Scam
These attacks primarily deliver fake cryptocurrency wallets that:
- Mimic legitimate apps like Exodus or Ledger Live
- Steal wallet recovery phrases
- Exfiltrate credentials through Telegram APIs
- Include connectivity checks to prevent analysis
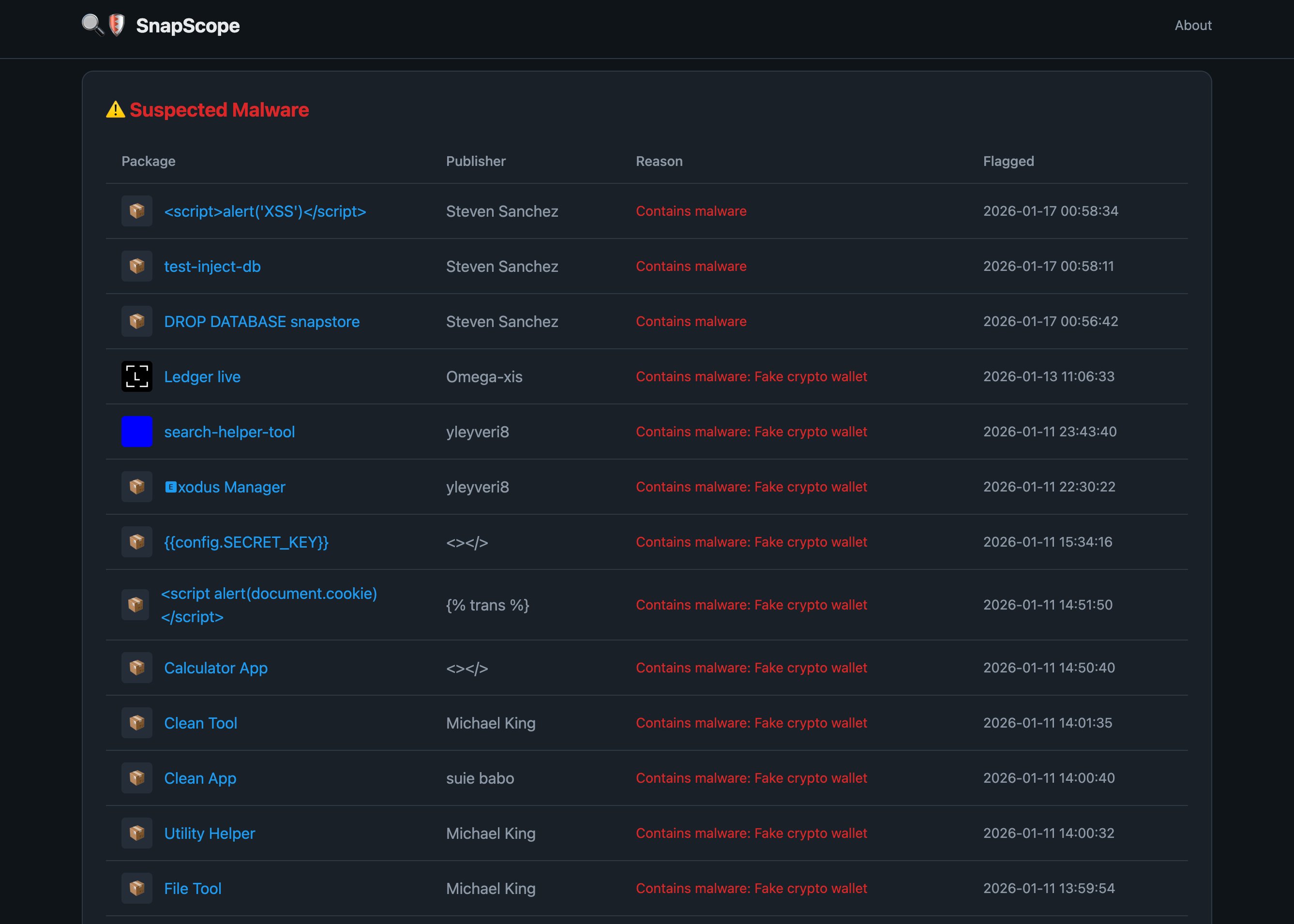 Malware samples show sophisticated phishing interfaces
Malware samples show sophisticated phishing interfaces
Why This Matters
This attack pattern fundamentally undermines trust signals:
- No "new publisher" warnings
- Established version history appears legitimate
- Automated filters miss account takeovers
 Publisher accounts become attack vectors when domains expire
Publisher accounts become attack vectors when domains expire
Fighting Back with SnapScope
I developed SnapScope to monitor the Snap Store ecosystem. This tool:
- Generates Software Bill of Materials (SBOM) for snaps
- Identifies outdated packages
- Flags suspicious characteristics
- Provides transparency for users
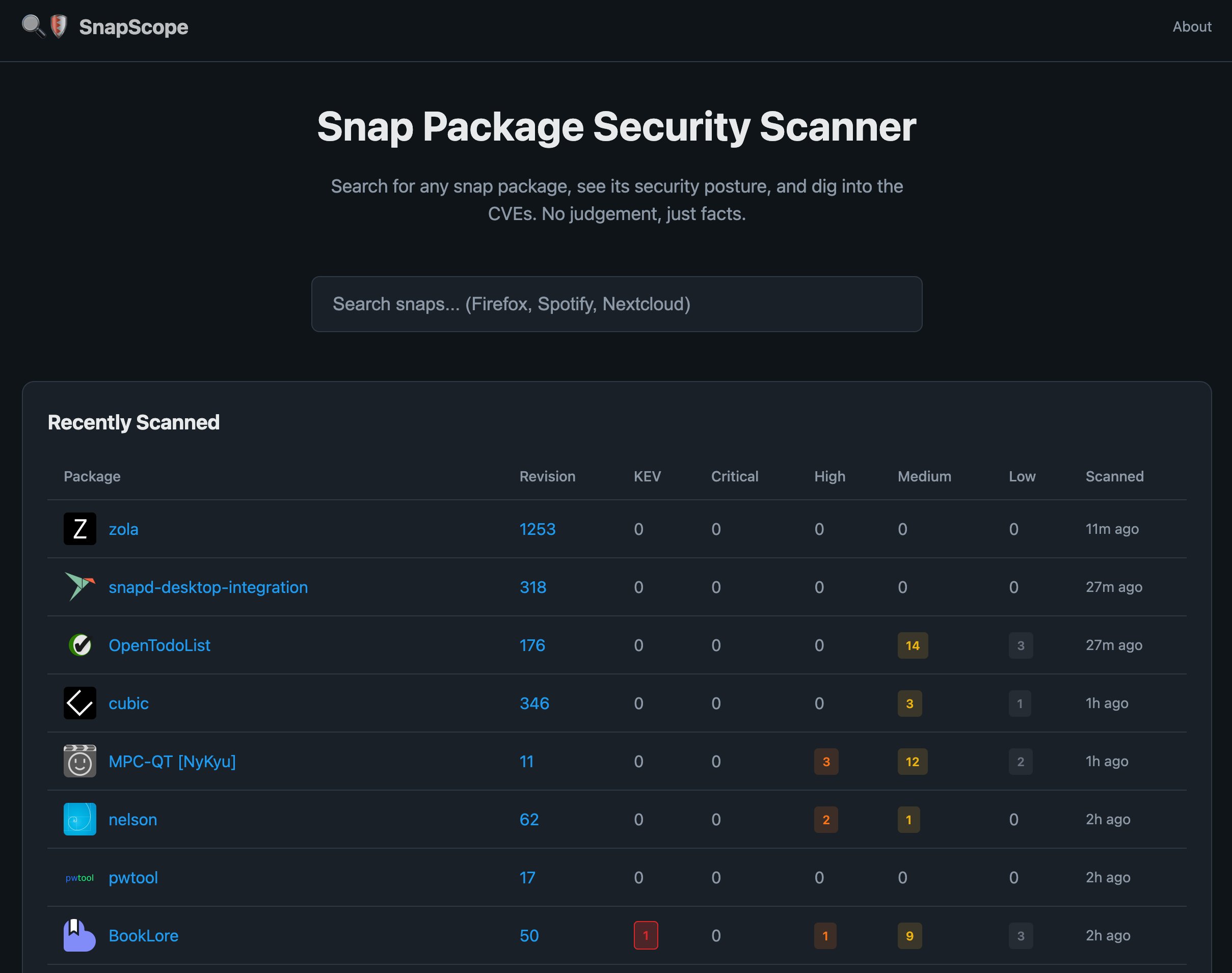 SnapScope helps users make informed installation decisions
SnapScope helps users make informed installation decisions
Protection Measures
For Publishers:
- Maintain active domain registrations
- Enable two-factor authentication
- Monitor account activity
For Users:
- Avoid installing crypto wallets from app stores
- Verify publisher domains before installation
- Report suspicious snaps immediately
Canonical must implement additional safeguards like domain expiration monitoring and enhanced verification for dormant accounts. Community vigilance remains our best defense until systemic improvements arrive.

Comments
Please log in or register to join the discussion