Multiple threat actors continue exploiting CVE-2025-8088, a WinRAR path traversal flaw, to deploy malware via malicious archives, impacting Ukrainian military targets and spreading commodity malware.

Security researchers warn that a high-severity path traversal vulnerability in WinRAR (CVE-2025-8088) remains actively exploited by both state-sponsored groups and financially motivated hackers six months after its discovery. The flaw allows attackers to bypass security mechanisms and plant malware in critical system locations using Alternate Data Streams (ADS).
Google Threat Intelligence Group (GTIG) researchers explain: "The exploit chain often involves concealing the malicious file within the ADS of a decoy file inside the archive. While the user typically views a decoy document, such as a PDF, within the archive, there are also malicious ADS entries, some containing a hidden payload while others are dummy data." When victims extract the archive, WinRAR unwittingly writes malicious files to arbitrary locations—typically Windows Startup folders—enabling automatic execution during system boot.
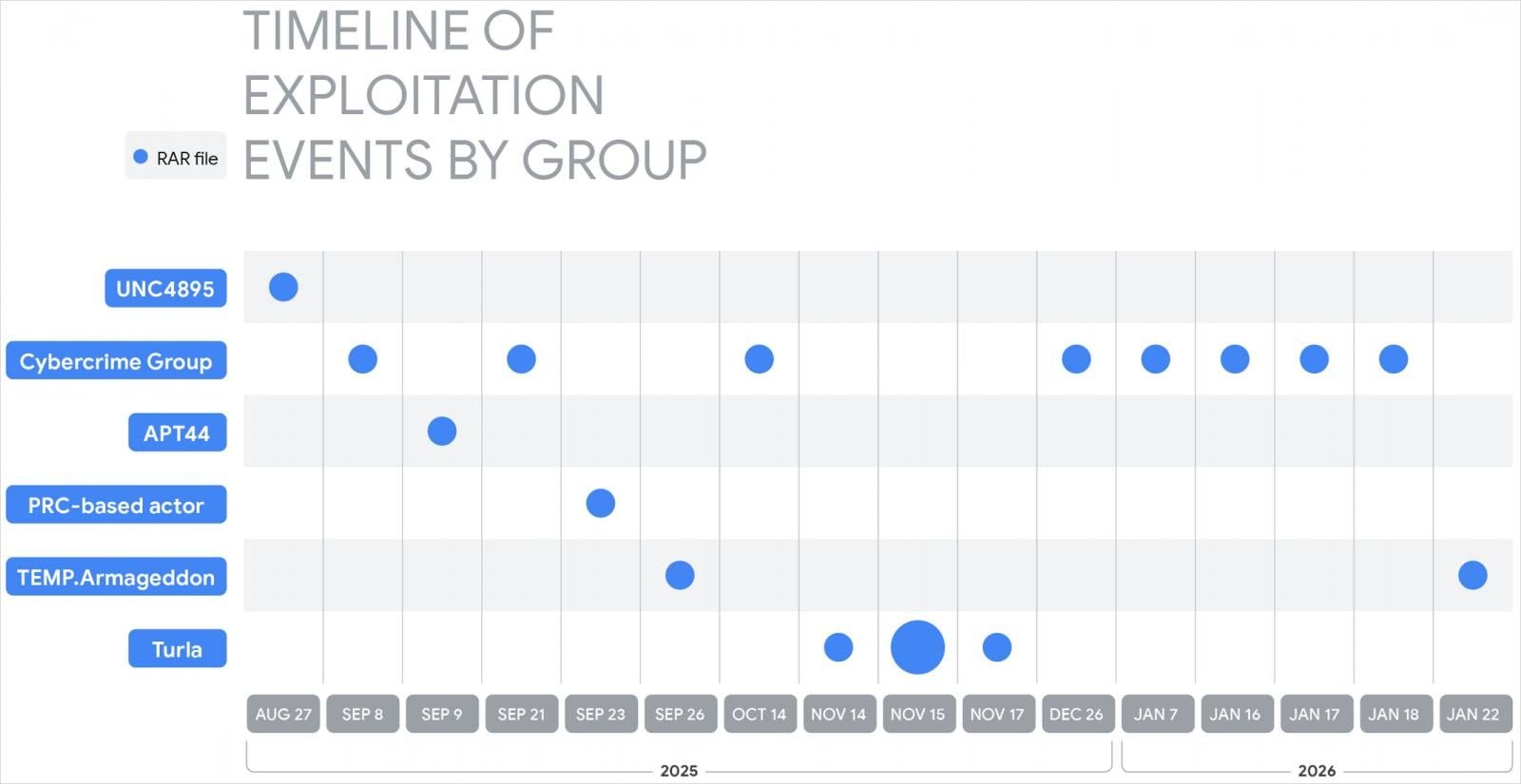
According to GTIG's latest findings, exploitation began on July 18, 2025—weeks before ESET's initial disclosure—and persists today. The timeline shows sustained attacks across multiple threat groups:
State-sponsored actors:
- UNC4895 (RomCom) targeting Ukrainian military units with NESTPACKER malware
- APT44 (FROZENBARENTS) deploying Ukrainian-language decoys
- Turla distributing STOCKSTAY malware via army-themed lures
- China-linked groups deploying POISONIVY RAT
Financially motivated actors:
- Distributing XWorm, AsyncRAT, and Telegram bot backdoors
- Installing malicious Chrome extensions for banking theft
Evidence indicates most attackers sourced working exploits from specialized suppliers like "zeroplayer," who advertised WinRAR exploits alongside other high-value vulnerabilities last July. Google notes this reflects "the commoditization of exploit development," enabling attackers to rapidly weaponize vulnerabilities for prices ranging from $80,000 to $300,000.
Practical Mitigation Steps
- Update immediately: Install WinRAR 7.01 or newer—the fixed version released in August 2025
- Scan existing archives: Use tools like RarLabs' inspection utilities to detect malicious ADS streams
- Disable suspicious auto-extraction: Configure Windows to block LNK/HTA/BAT file execution from temp directories
- Deploy application control: Restrict WinRAR's write permissions to designated folders using Microsoft Defender Application Control
- Educate users: Train staff to avoid opening archives from untrusted sources, especially military-themed or urgent financial lures
As GTIG emphasizes, "This vulnerability significantly lowers the barrier for initial access," making prompt patching critical given the ongoing exploitation by both sophisticated APTs and commodity malware distributors.

Comments
Please log in or register to join the discussion