Securing Your Essentials: How AirTag Wallets Are Redefining Personal Item Tracking
Losing a wallet isn't just an inconvenience; it’s a security crisis. Apple’s AirTag, leveraging the vast Find My network...

Beyond the Hype: The Flipper Zero's Legitimate Power in Security and Hardware Testing
The Flipper Zero exploded into mainstream consciousness via sensationalized social media clips, often depicting it as a ...

OpenAI Unleashes ChatGPT Agent: The Next Evolution in AI-Assisted Task Automation
For years, the promise of AI agents that could autonomously execute complex tasks; like booking flights or analyzing bus...
RunAgent Emerges as Universal AI Agent Platform, Solving Polyglot Development Headaches
The fragmentation of modern tech stacks; where Python dominates AI development but applications span JavaScript frontend...

CHIPS: How Partitioned Cookies Are Reshaping Web Privacy Without Breaking Functionality
For years, third-party cookies have been the silent enablers of cross-site tracking, allowing services to monitor user a...

Gemini Code Assist Evolves: Agent Mode and IDE Upgrades Redefine AI Pair Programming
Google's Gemini Code Assist has taken a significant leap forward with the introduction of agent mode and substantial I...

Critical Cisco ISE Flaw: Unauthenticated Attackers Can Execute Commands as Root
A critical vulnerability in Cisco's Identity Services Engine (ISE) has sent shockwaves through the cybersecurity communi...

Salt Typhoon's Stealthy Siege: Nine-Month National Guard Breach Exposes Critical Network Vulnerabilities
In a stark reminder of the fragility of national cybersecurity defenses, the Chinese state-sponsored hacking group Salt ...

KeySmart iPro Review: The Tech-Enhanced Key Organizer That Never Gets Lost
For developers and tech enthusiasts drowning in key chaos, the KeySmart iPro Key Holder offers a surprisingly elegant so...

TCL's 2024 QM8 Mini LED TV: A Budget Powerhouse That Outshines Premium Competitors
The Mini LED Revolution Hits Main Street In an era where premium TVs command astronomical prices, TCL's 2024 QM8 Mini ...
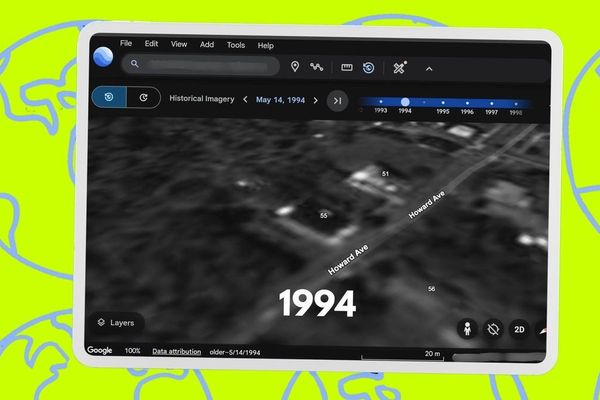
Unlocking Digital Time Travel: How Google Earth's Hidden Slider Reveals 80 Years of Urban Evolution
The recent viral surge in nostalgic Google Street View explorations has captivated users rediscovering personal historie...

China's Sodium-Ion Gambit: How E-Scooters Are Electrifying the Battery Revolution
On a bustling street in Hangzhou, rows of sleek electric mopeds glisten under the sun; not as mere vehicles, but as harb...
The Embedded Anxiety: When Web Developers Eye the Hardware Frontier
In a revealing Hacker News comment, a developer voiced a common yet often unspoken dread: "I have multiple smaller Pico ...