The AISURU/Kimwolf botnet has launched a record-breaking 31.4 Tbps DDoS attack, leveraging over 2 million compromised Android devices and residential proxy networks to mount increasingly sophisticated hyper-volumetric attacks that have doubled in frequency throughout 2025.
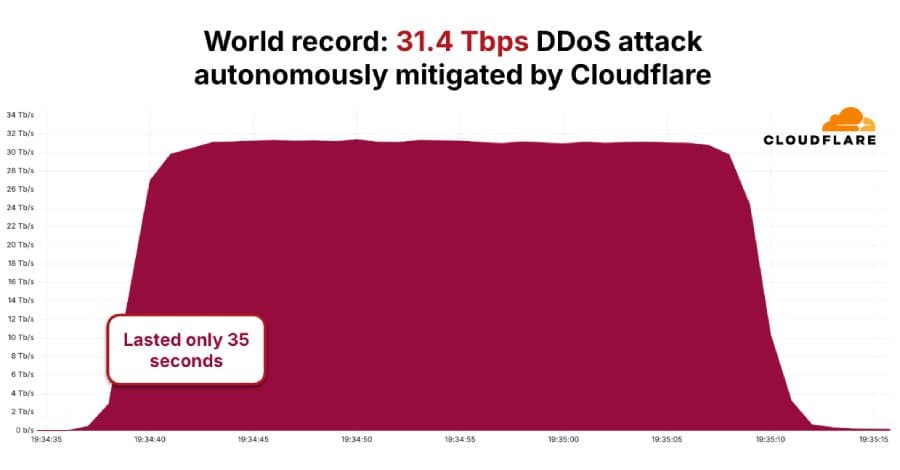
The cybersecurity landscape faced a new milestone in November 2025 when the AISURU/Kimwolf botnet executed a record-setting distributed denial-of-service (DDoS) attack that peaked at 31.4 Terabits per second, lasting just 35 seconds but representing a quantum leap in attack capabilities.
Record-Breaking Attack Volume
The November 2025 assault marks the largest DDoS attack ever recorded, according to Cloudflare, which automatically detected and mitigated the hyper-volumetric HTTP DDoS attack. This record-breaking event is part of a broader trend that saw DDoS attacks surge by 121% throughout 2025, with organizations facing an average of 5,376 attacks automatically mitigated every hour.
The Botnet's Expanding Arsenal
AISURU/Kimwolf has demonstrated remarkable versatility in its attack patterns. Beyond the 31.4 Tbps record, the botnet was responsible for "The Night Before Christmas" campaign that began December 19, 2025. During this campaign, the average hyper-volumetric DDoS attacks reached 3 billion packets per second (Bpps), 4 Tbps, and 54 million requests per second (Mrps), with maximum rates touching 9 Bpps, 24 Tbps, and 205 Mrps.
Massive Scale of Compromise
At the heart of AISURU/Kimwolf's capabilities lies an unprecedented scale of compromise. The botnet has ensnared more than 2 million Android devices, with the majority being compromised, off-brand Android TVs. These devices are often compromised through residential proxy networks like IPIDEA, which has become a central focus of law enforcement and security efforts.
The IPIDEA Connection
Google recently disrupted the IPIDEA proxy network and initiated legal action to take down dozens of domains used to control devices and proxy traffic through them. The company partnered with Cloudflare to disrupt IPIDEA's domain resolution, significantly impacting their ability to command and control infected devices and market their products.
IPIDEA's operation was particularly sophisticated, enrolling devices using at least 600 trojanized Android apps that embedded various proxy software development kits (SDKs). Additionally, the Beijing-based company distributed over 3,000 trojanized Windows binaries disguised as OneDriveSync or Windows updates. The company also advertised several VPN and proxy apps that silently turned users' Android devices into proxy exit nodes without their knowledge or consent.
Infrastructure Scale
Behind the scenes, IPIDEA operated at least a dozen residential proxy businesses that masqueraded as legitimate services. All these offerings were connected to a centralized infrastructure under IPIDEA's control, creating a complex web of seemingly independent services that funneled through a single command structure.
2025 DDoS Landscape
The year 2025 saw DDoS attacks more than double to an incredible 47.1 million total incidents. Cloudflare mitigated 34.4 million network-layer DDoS attacks in 2025, compared to 11.4 million in 2024. In Q4 2025 alone, network-layer DDoS attacks accounted for 78% of all DDoS attacks.
Hyper-Volume Attack Surge
Hyper-volumetric attacks increased by 40% in Q4 2025 compared to the previous quarter, jumping from 1,304 to 1,824 attacks. The spike in attack frequency has been complemented by an increase in size, with attacks growing by over 700% compared to the large attacks seen in late 2024.
Geographic and Sector Targeting
Cloudflare's analysis revealed several key trends in attack patterns:
- Most attacked sectors: Telecommunications, service providers, and carriers led the list, followed by information technology, gambling, gaming, and computer software verticals.
- Most attacked countries: China, Hong Kong, Germany, Brazil, the U.S., the U.K., Vietnam, Azerbaijan, India, and Singapore faced the highest volume of attacks.
- Attack sources: Bangladesh surpassed Indonesia to become the largest source of DDoS attacks, with other top sources including Ecuador, Indonesia, Argentina, Hong Kong, Ukraine, Vietnam, Taiwan, Singapore, and Peru.
Growing Sophistication
"DDoS attacks are rapidly growing in sophistication and size, surpassing what was previously imaginable," Cloudflare noted in their analysis. "This evolving threat landscape presents a significant challenge for many organizations to keep pace. Organizations currently relying on on-premise mitigation appliances or on-demand scrubbing centers may benefit from re-evaluating their defense strategy."
The combination of massive scale, sophisticated infrastructure, and increasingly powerful attacks suggests that DDoS capabilities will continue to evolve rapidly. Organizations must adapt their defensive strategies to address this growing threat, potentially moving beyond traditional on-premise solutions to more comprehensive, cloud-based protection systems.
The AISURU/Kimwolf botnet represents not just a technical achievement in terms of raw attack power, but also demonstrates the evolving nature of cybercrime infrastructure, where legitimate-seeming services mask sophisticated attack networks capable of unprecedented disruption.
Comments
Please log in or register to join the discussion