AWS has launched VPC encryption controls, a feature designed to provide visibility and enforcement of in-transit encryption for traffic within and between VPCs. While the tool addresses significant compliance challenges for regulated industries, its pricing model—$110 per month per non-empty VPC—has sparked debate within the community regarding the cost of essential security controls.
AWS has officially rolled out VPC encryption controls, a new capability aimed at solving a persistent headache for cloud architects: verifying that traffic actually stays encrypted as it moves between services. For organizations operating under strict regulatory frameworks like HIPAA, PCI DSS, or FedRAMP, proving that data is encrypted in transit isn't just a best practice—it's a mandatory requirement.
Until now, achieving this level of assurance often meant piecing together disparate monitoring solutions, managing complex public key infrastructure (PKI), or manually tracking encryption status across network paths using spreadsheets. As Sébastien Stormacq, a principal developer advocate at AWS, notes, this manual approach creates significant operational complexity.
How VPC Encryption Controls Work
The new feature operates in two distinct modes: monitor and enforce.
When you first activate the feature, you'll likely start in monitor mode. This gives administrators visibility into the encryption status of traffic flows within the VPC. It identifies resources that are unintentionally allowing plaintext traffic, giving you a clear picture of where your security posture might be lacking before you commit to stricter controls.
Once you've identified and remediated the gaps, you can switch to enforce mode. In this state, AWS ensures that all new resources are created exclusively on compatible Nitro-based instances. More importantly, any unencrypted traffic using incorrect protocols or ports is actively dropped.
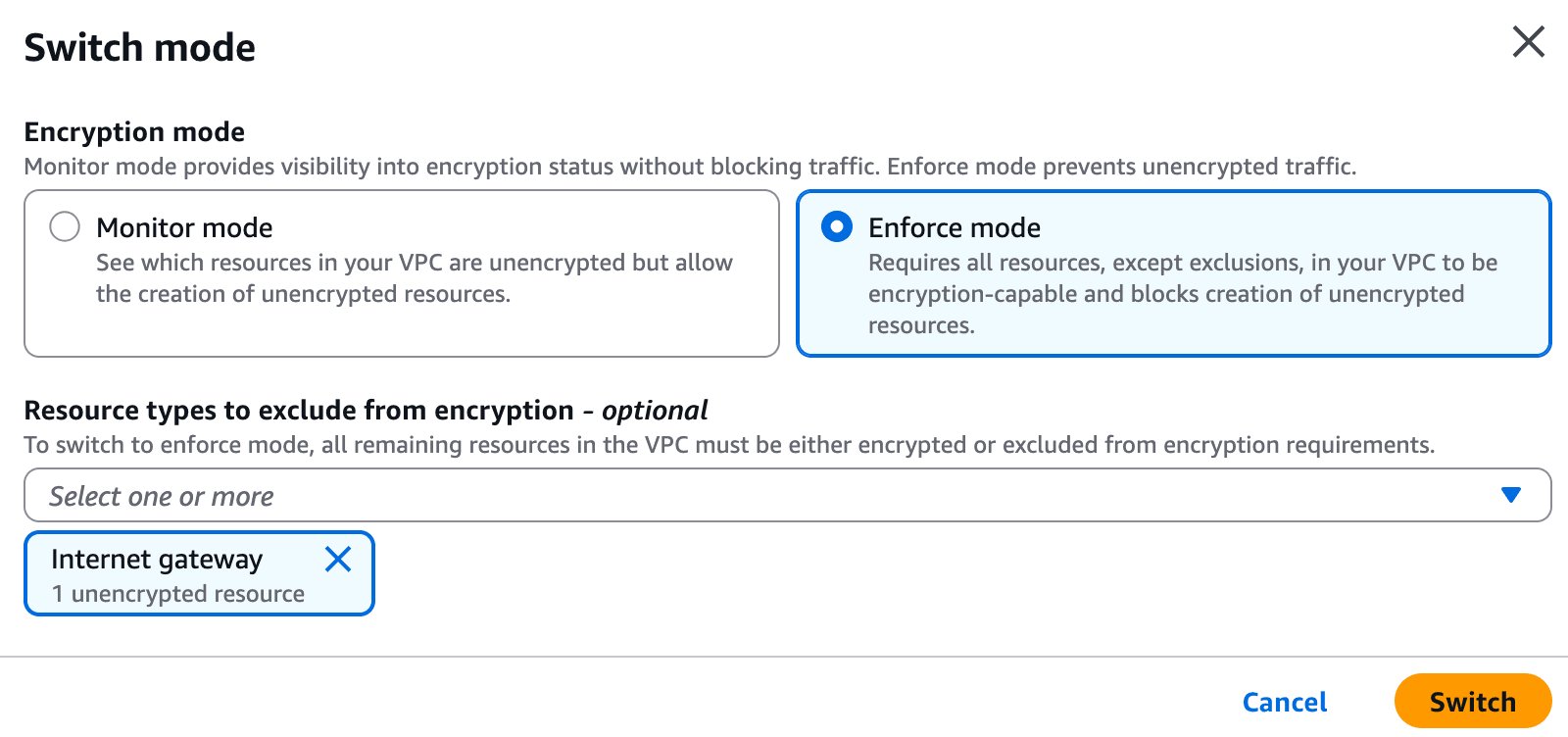
However, enforce mode isn't something you can simply flip on. It requires that all existing resources within the VPC are already migrated to encryption-compliant infrastructure. If you have any resources running on non-Nitro hardware or using protocols that don't support encryption, AWS will block you from enabling enforcement.
The Migration Path and Exclusions
This requirement means the migration effort can be substantial. You'll need to upgrade to supported hardware and ensure all communication protocols are compatible. For resources that simply cannot encrypt traffic—such as internet gateways or NAT gateways where traffic leaves the AWS network—you can configure specific exclusions. These exclusions are tracked and can be reported on, which is crucial for audit purposes.
Anish Kumar, writing about the feature's security implications, highlights the audit value: "For your cloud security posture, you can answer the question: 'Is all traffic in my VPC estate encrypted in transit?' with confidence and evidence. And from a compliance audit perspective, you can show the encryption-status in your flow logs and exclusions list."
The Cost Debate
While the technical capabilities have been generally well-received, the pricing model has drawn criticism. Starting March 1, 2026, the feature will cost $0.15 USD per hour per non-empty VPC, which totals approximately $110 per month per VPC.
Many community members have argued that fundamental security controls should be included in the base service offering rather than treated as a premium add-on. User kei_ichi expressed this sentiment clearly: "That feature should be enabled by default and free."
Chris Farris, an AWS Security Hero and cloud security consultant, offers a pragmatic perspective in his re:Invent recap: "Let's start with why you should avoid this - $110 per month per non-empty VPC. This is absolutely worth it if you need 'To meet stringent compliance standards like HIPAA and PCI DSS' and 'demonstrate compliance with encryption standards.'"
Farris points out that while the migration effort is significant, if auditors are requiring manual compliance verification anyway, the cost might be justified as an automation and documentation expense.
Availability and Next Steps
VPC encryption controls are currently available in select regions, including Northern Virginia (us-east-1), Ireland (eu-west-1), London (eu-west-2), and Singapore (ap-southeast-1). The feature is free to use until March 1, 2026, giving teams time to evaluate the tool and plan their migration strategy.
For organizations considering adoption, the path forward involves:
- Assessment: Enable monitor mode to identify current encryption gaps
- Migration: Upgrade non-compliant resources to Nitro-based instances
- Configuration: Set up exclusions for resources that cannot encrypt
- Enforcement: Switch to enforce mode once all resources are compliant
- Documentation: Use the generated reports for compliance audits
The feature represents a step toward making encryption compliance more manageable at scale, though the pricing structure suggests AWS views this as a premium compliance tool rather than a baseline security feature.

For more details, see the official AWS blog post on VPC encryption controls and the VPC documentation.

Comments
Please log in or register to join the discussion