Open-source framework Clan transitions from experimental project to production-ready sovereign computing platform, enabling user-controlled networks and applications through novel networking abstractions, secure micro VMs, and accessible management tools.
The Sovereign Computing Imperative
Clan represents a fundamental rethinking of digital infrastructure, positioning user sovereignty as non-negotiable in an era of escalating technological control. This open-source framework enables individuals and groups to construct private networks where machines operate under exclusive user control through composable, reproducible systems. The 2025 stable release marks Clan's transition from experimental project to production-ready infrastructure, responding to urgent needs for alternatives to extractive technology models that dominate mainstream platforms.
Foundational Networking Innovations
Reliable peer-to-peer connectivity forms Clan's bedrock. Traditional virtual private networks force users into binary choices between centralization and fragility. Clan introduces a networking abstraction layer allowing multiple overlay technologies—including Tor and public internet—to coexist simultaneously. Machines automatically select optimal connections through declarative tagging systems, while sensitive routing details remain encrypted until deployment.
This approach yields tangible reliability improvements. Command-line tools now infer network configurations from system definitions, eliminating manual host specification. Connection failures gracefully degrade to alternative pathways without exposing machines unnecessarily to public networks. The architecture deliberately avoids centralized choke points while accommodating future protocols, moving toward networking that "merely functions" without obscuring underlying complexity.
Micro VMs: Sovereign Application Containers
Applications represent the next sovereignty frontier. Proprietary platforms leverage heavy sandboxing and pre-connected services, while peer-to-peer alternatives often compromise security or usability. Clan bridges this gap through micro virtual machines—lightweight, hardware-isolated environments launching in milliseconds. These combine:
- Strong security boundaries: Hardware-enforced separation prevents compromised applications from affecting host systems
- Native performance: GPU acceleration via virtio techniques enables Wayland-based graphical applications
- P2P integration: Pre-configured Clan networks enable direct machine communication without intermediaries
- User-centric permissions: D-Bus portals mediate controlled resource access through explicit consent
When integrated with Nix's reproducible builds and Clan's mesh networking, micro VMs create a local application platform where even conventionally cloud-dependent software can operate in self-hosted environments. Early experiments show promise for extending this model to portable Clan environments beyond NixOS.
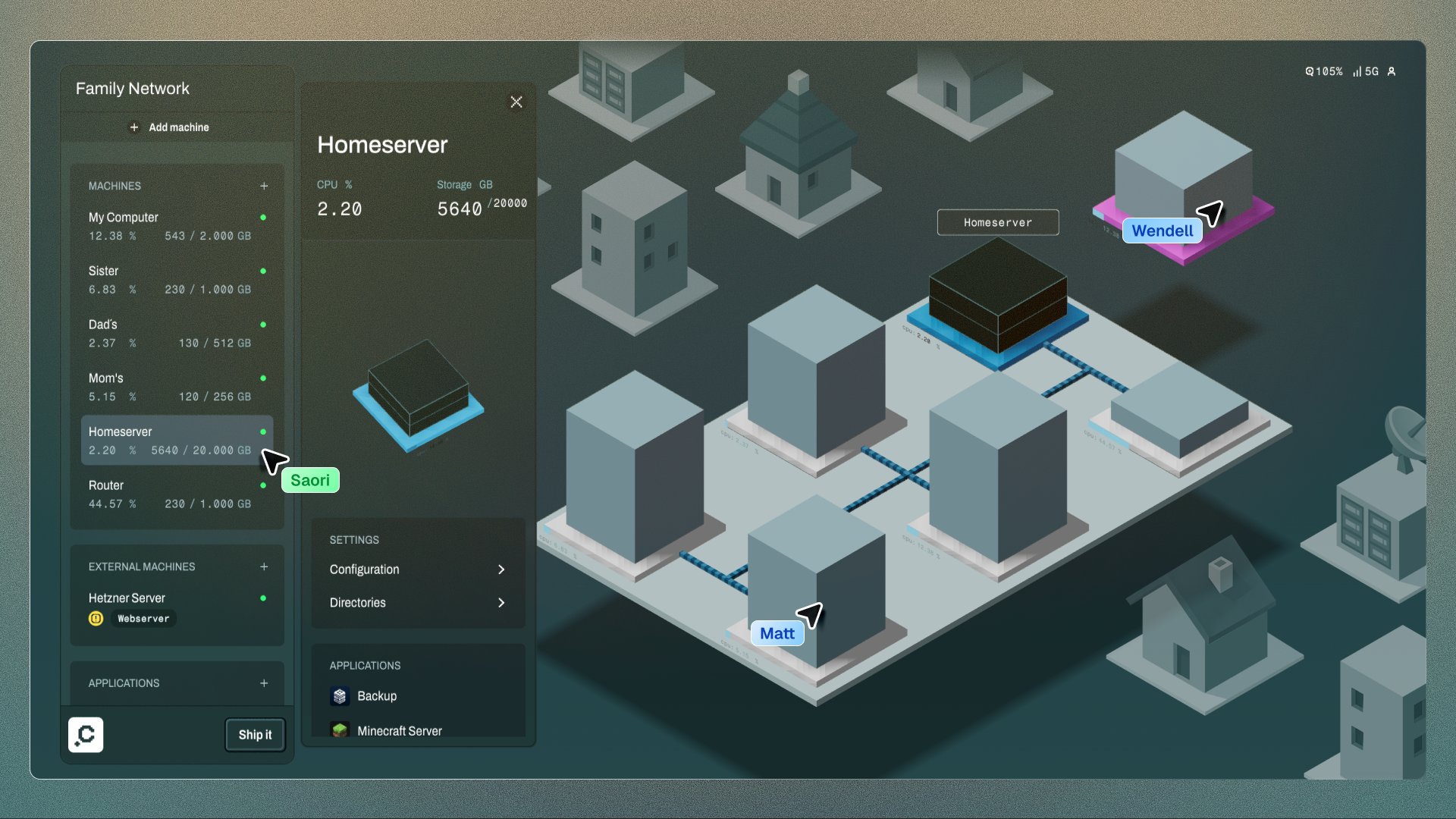
Democratizing Infrastructure Management
Complex configuration remains a barrier to sovereignty. Clan's new graphical interface tackles infrastructure management's hardest aspects—machine bootstrapping, secret rotation, and cross-service coordination—through visual abstractions. The GUI complements rather than replaces command-line tools, reflecting Clan's declarative framework through:
- Secret lifecycle management: Services declare secret requirements for automatic generation and rotation
- Multi-machine service layers: Infrastructure definitions apply across machine groups via tags
- Visual topology mapping: Relationships between machines and services become intuitively navigable
This approach extends to macOS systems via nix-darwin integration, acknowledging real-world heterogeneity. The inventory system shifts focus from individual machines to fleet management, while service exports enable automatic inter-component wiring without manual glue code.
Future Vistas: Spaces and Local Intelligence
Clan's trajectory points toward fundamentally reimagined computing paradigms. The forthcoming Spaces environment embeds sovereignty at the operating system level, creating distinct digital realms for different activities—work, social, creative—each with customized tools and access rules. These isolated environments maintain persistent peer connections resistant to external disruption.
Local large language models present another frontier under strict sovereignty constraints. When self-hosted within Clan's isolated environments, LLMs could serve as:
- Accessibility layers: Translating natural language into system actions without requiring technical expertise
- Coordination mediators: Facilitating interaction within Spaces without centralized platforms
- Discovery engines: Enabling service negotiation between sovereign Clans through locally-indexed descriptions
This contrasts sharply with proprietary cloud-based AI, maintaining Clan's commitment to inspectability and user control.
Ecosystem Growth and Scaling Challenges
ClanHub represents a strategic approach to sustainable growth—a community space for services requiring less core integration. This separation of concerns allows fundamental networking and security work to proceed while accommodating community innovation. Early examples like Friedow's monitoring service demonstrate how ClanHub could host specialized components while maintaining ecosystem coherence.
Scalability testing reveals intriguing possibilities for decentralized infrastructure. Blockchain systems—notoriously dependent on centralized node operators—could leverage Clan for communal node hosting. The framework's reproducibility and security models might address decentralization gaps at infrastructure, application, and protocol layers, though significant usability challenges remain for non-technical adoption.
The Sovereignty Tradeoff
Clan's approach necessitates confronting inherent tensions. Strong security boundaries and decentralization introduce complexity that challenges mainstream usability expectations. While the GUI and natural language interfaces lower barriers, sovereign computing still demands more user responsibility than managed platforms. This reflects Clan's core philosophical stance: genuine autonomy requires accepting the burden of control, rejecting convenience-focused compromises that inevitably enable extraction.
The project's significance transcends its technical components. By demonstrating that sovereign systems can match proprietary platforms in security and approach them in usability, Clan challenges the inevitability of centralized digital futures. As corporate and government control intensifies, such alternatives become increasingly vital—not as niche solutions, but as blueprints for a repluralized internet built from sovereign spaces rather than monolithic platforms.
Comments
Please log in or register to join the discussion