Cloudflare's investigation into a Venezuelan routing anomaly shows recurring BGP leaks likely stem from configuration issues rather than malicious activity, highlighting opportunities for improved internet security protocols.

When cybersecurity analysts spotted unusual internet routing patterns in Venezuela amid political developments, Cloudflare's data team examined the Border Gateway Protocol (BGP) anomalies. Their findings point toward recurring technical misconfigurations rather than deliberate interference.
Between December and January, Venezuela's state-run ISP CANTV (AS8048) originated eleven separate route leaks. These incidents followed a consistent pattern where the provider improperly redistributed routes between its upstream networks. Specifically, routes belonging to Venezuelan telecom Dayco Telecom (AS21980) were leaked from Italian provider Sparkle (AS6762) to Colombian network V.tal GlobeNet (AS52320).
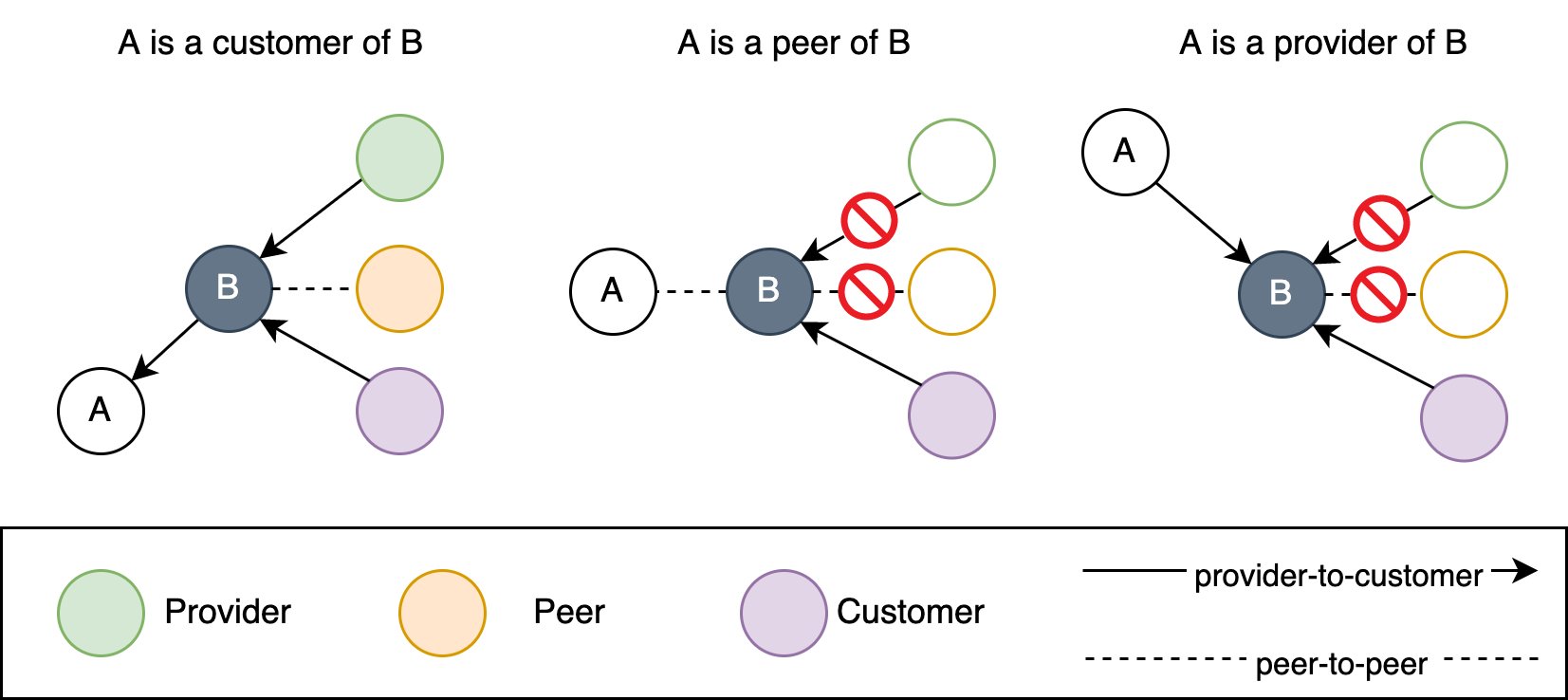
Route leaks occur when networks violate established internet routing relationships. Normally, providers follow valley-free routing principles where traffic flows upward from customers to providers without backtracking. When a customer network like AS8048 redistributes routes between two providers, it creates inefficient paths that can overwhelm smaller networks.
Cloudflare's technical analysis revealed three key indicators suggesting accidental causes:
- Heavy AS prepending in the leaked routes made them less attractive for traffic
- The leaks occurred multiple times over several hours
- Historical data shows similar incidents throughout December
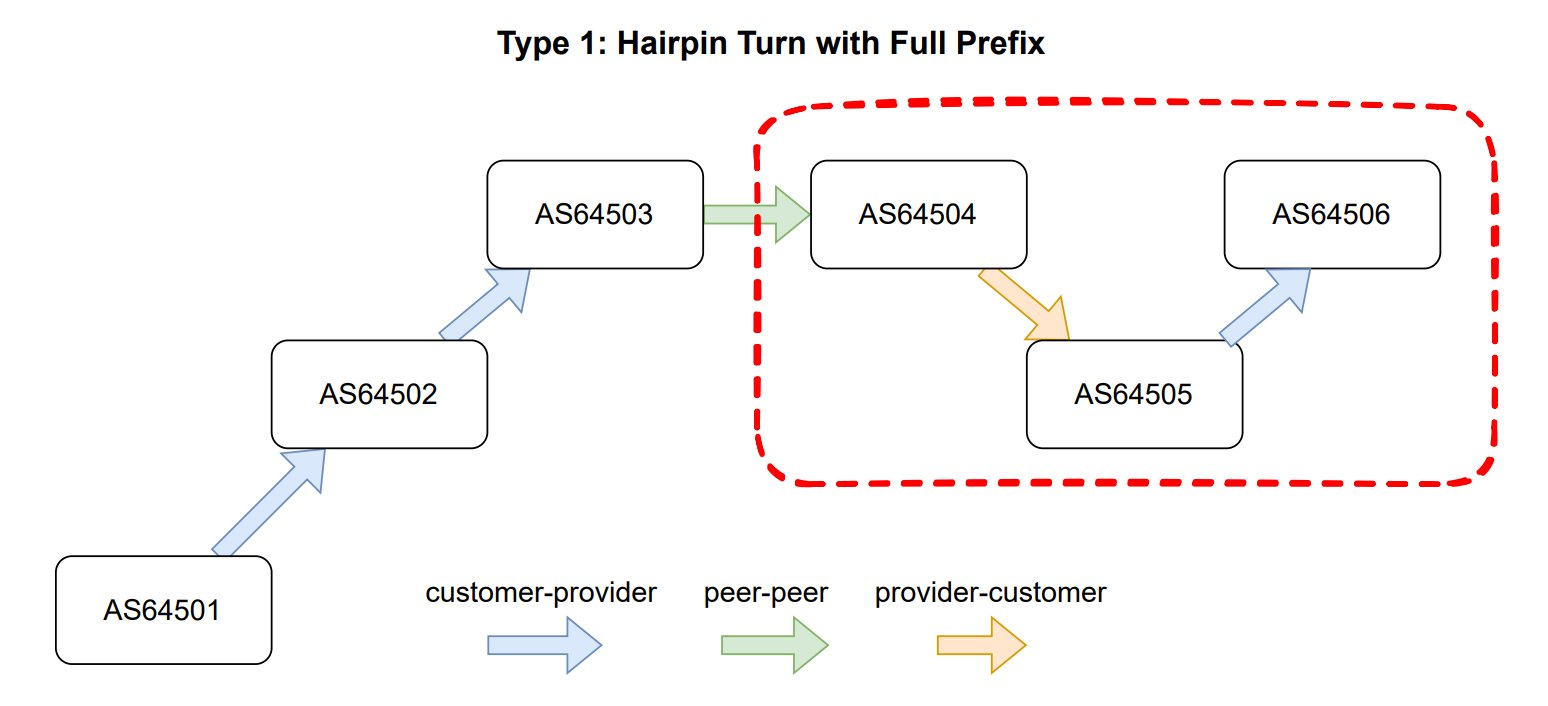
The findings highlight how common configuration errors can create significant internet disruptions. Cloudflare suggests wider adoption of emerging standards could prevent such incidents:
- ASPA (Autonomous System Provider Authorization): Path validation framework
- RFC9234: Defines BGP roles and Only-to-Customer attribute
- Peerlock: Sanity checks for route paths
These protocols would complement existing RPKI origin validation, creating layered security against both accidental leaks and intentional hijacking. Network operators can accelerate adoption by requesting vendor support for RFC9234 implementation.
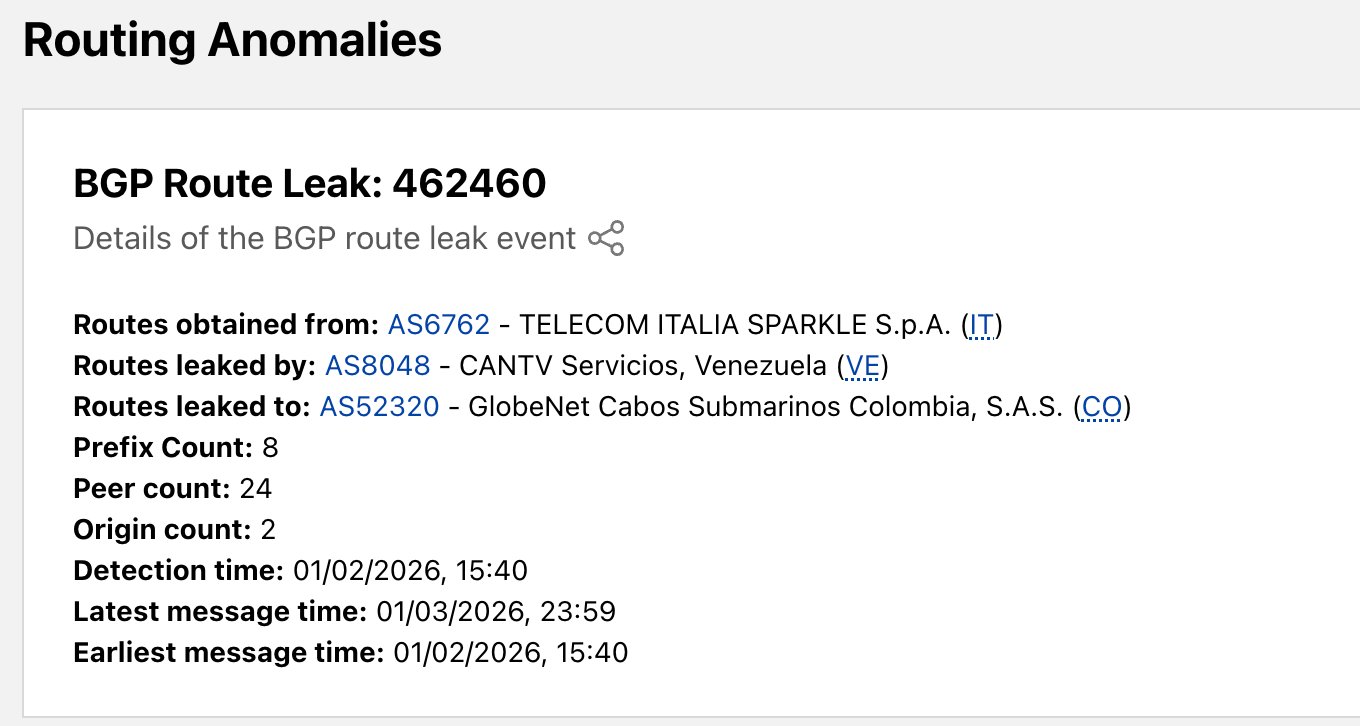
While geopolitical events understandably draw attention to network anomalies, this recurring pattern demonstrates how technical debt in routing infrastructure creates vulnerabilities. The solution lies in collaborative industry efforts to modernize BGP security rather than attributing isolated incidents to malicious actors.

Comments
Please log in or register to join the discussion