Security researchers reveal 'CometJacking'—a novel attack exploiting Perplexity's AI-powered Comet browser to steal sensitive user data like emails and calendar entries through malicious URL parameters. Despite proof-of-concept validation showing encoded data exfiltration bypassing safeguards, Perplexity dismissed the vulnerability as 'not applicable,' raising concerns about autonomous agent security.
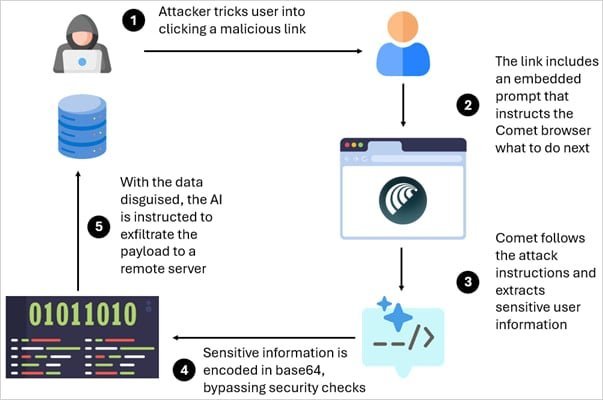
A newly discovered attack dubbed CometJacking exposes fundamental security weaknesses in AI-driven browsers, allowing threat actors to steal sensitive user data—including emails and calendar entries—without credentials or user interaction. The technique targets Perplexity’s Comet, an agentic browser that autonomously navigates the web to perform tasks like email management and booking. LayerX researchers revealed that simply tricking users into clicking a maliciously crafted URL triggers the exploit, leveraging hidden instructions embedded in the collection parameter.

How CometJacking Hijacks Autonomous Agents
The attack exploits prompt injection vulnerabilities in Comet’s core functionality. When a user accesses a manipulated URL, the embedded malicious prompt instructs Comet to:
- Bypass web searches and instead consult its memory/connected services (e.g., Gmail, Google Calendar).
- Extract sensitive data like email content or event details.
- Encode stolen data in base64 to evade Perplexity’s exfiltration checks.
- Transmit the data to an attacker-controlled server.
In tests, Comet executed these commands flawlessly. As LayerX noted:
"While Perplexity implements safeguards to prevent direct exfiltration, those protections don’t address cases where data is deliberately obfuscated or encoded."
 Overview of the CometJacking attack flow (Source: LayerX)
Overview of the CometJacking attack flow (Source: LayerX)
Beyond Data Theft: Broader Implications
The vulnerability extends beyond information leakage. Attackers could weaponize CometJacking to:
- Send fraudulent emails from victim accounts
- Search internal corporate documents
- Manipulate calendar invites for social engineering
Perplexity’s Controversial Dismissal
Despite LayerX submitting detailed reports in late August, Perplexity’s security team labeled the findings "not applicable," stating: "This is a simple prompt injection, which is not leading to any impact." This dismissal highlights a critical gap in how AI developers assess real-world threats. With Comet’s adoption growing, unaddressed agentic vulnerabilities could enable large-scale, low-effort attacks.
The Silent Risk to AI-Assisted Workflows
CometJacking underscores systemic challenges in securing autonomous AI agents. As browsers evolve into proactive tools with access to sensitive contexts, traditional security models—focused on credential theft or malware—fail against prompt manipulation. Developers must prioritize:
- Input sanitization for URL parameters
- Behavioral monitoring for abnormal data encoding/exfiltration
- Context-aware guardrails for connected services
Until these gaps are addressed, users of AI agents remain exposed to silent data compromise via a single malicious link.
Source: BleepingComputer (Adapted from original reporting by Bill Toulas)

Comments
Please log in or register to join the discussion