A privilege escalation vulnerability in ACF Extended WordPress plugin allows attackers to gain admin access on unpatched sites, amid ongoing reconnaissance campaigns targeting vulnerable plugins.

A critical vulnerability in the WordPress ecosystem has exposed approximately 50,000 websites to complete administrative takeover. The flaw in Advanced Custom Fields: Extended (ACF Extended) plugin enables unauthenticated attackers to bypass security controls and create administrator accounts, forging a path to full site compromise.
The Vulnerability Mechanics
Tracked as CVE-2025-14533, this privilege escalation vulnerability affects ACF Extended versions 0.9.2.1 and earlier. The security weakness resides in how the plugin handles user creation and updates through its 'Insert User/Update User' form actions. Despite administrators configuring role restrictions in field settings, the vulnerable plugin versions fail to enforce these limitations during actual operations.
"In the vulnerable plugin iteration, attackers can arbitrarily set a user's role to 'administrator' regardless of field configuration," explains Wordfence's threat analysis team. "This bypass occurs when a role field exists within the form structure, effectively handing over the keys to the kingdom."
Attack Scope and Mitigation
While ACF Extended currently runs on 100,000 WordPress sites, only installations using specific user creation/update forms with role fields mapped are vulnerable. Security researcher Andrea Bocchetti discovered the flaw and reported it to Wordfence on December 10, 2025. The plugin developer responded swiftly, patching the vulnerability in version 0.9.2.2 released just four days later.
According to WordPress.org download statistics, approximately 50,000 sites remain unprotected by failing to update since the patch release. This leaves a significant attack surface despite no observed exploitation attempts to date.
Expanding Threat Landscape
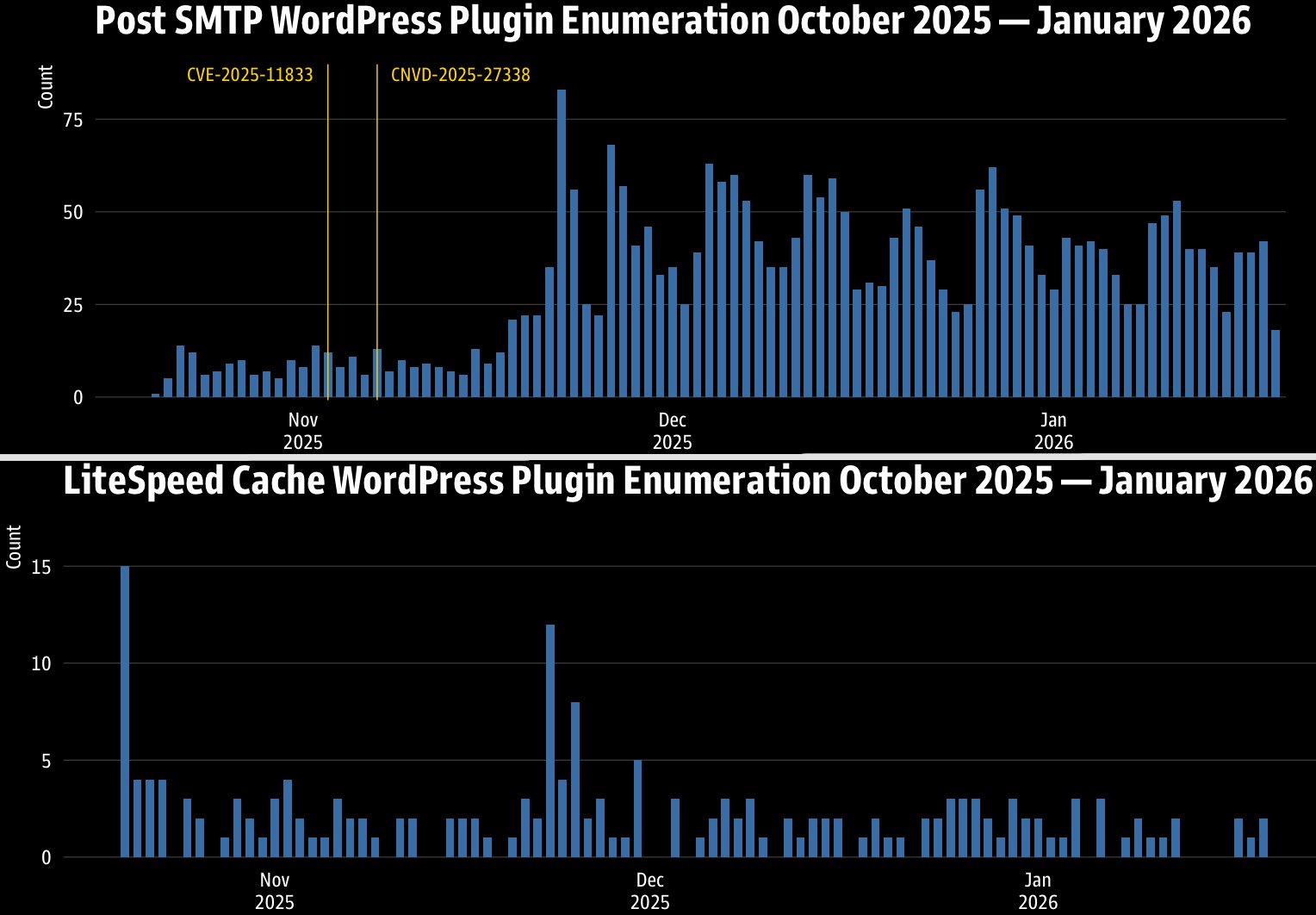
WordPress administrators face escalating threats beyond this single vulnerability. GreyNoise's latest threat intelligence report reveals aggressive reconnaissance campaigns targeting WordPress plugins. Between October 2025 and mid-January 2026, researchers observed:
- Nearly 1,000 unique IP addresses scanning for vulnerabilities
- Attacks originating from 145 autonomous systems (ASNs)
- Over 40,000 enumeration events targeting 706 distinct plugins
Top-targeted plugins include Post SMTP, Loginizer, LiteSpeed Cache, and Elementor. Notably, attackers are actively exploiting known vulnerabilities in Post SMTP (CVE-2025-11833) and LiteSpeed Cache (CVE-2024-28000), both previously documented as under active attack.
Essential Protection Steps
- Immediately update ACF Extended to v0.9.2.2 or newer from the official repository
- Audit user accounts: Check for unexpected administrator-level accounts
- Prioritize patch deployment for other high-risk plugins:
- Post SMTP (update to v3.1.2+)
- LiteSpeed Cache (update to v6.1+)
- Implement web application firewalls with virtual patching capabilities
- Monitor authentication logs for suspicious account creation patterns
- Subscribe to vulnerability alerts through services like Wordfence Intelligence
"As with any privilege escalation vulnerability, this can be used for complete site compromise," Wordfence researchers emphasize. With attackers systematically mapping vulnerable WordPress installations, timely patching remains the most effective defense against these evolving threats.

Comments
Please log in or register to join the discussion