Experimental transformations between image and audio domains uncover artifacts with implications for steganography detection and multimedia forensics.

What happens when you apply image processing techniques to audio data, or audio processing methods to images? A recent technical exploration by security researcher Michał Zalewski (lcamtuf) reveals surprising cross-domain artifacts with potential implications for multimedia security practices.
When Pixel Techniques Meet Audio
Zalewski's experiment applied image downsampling techniques—where pixel blocks are averaged into single values—to audio waveforms. While this creates visually pleasing pixel art in images, it introduces metallic-sounding artifacts in audio due to stairstep waveform patterns:
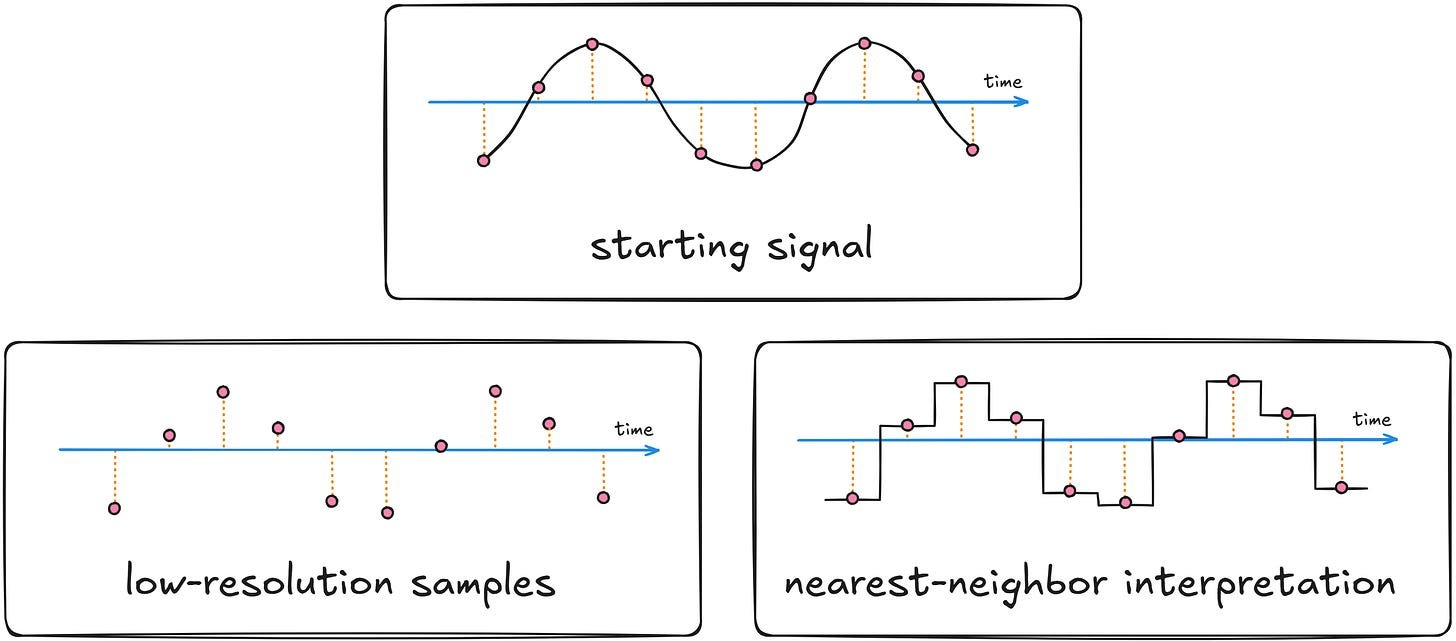
"Our eyes don't mind stairstep patterns on screen, but the cochlea interprets abrupt jumps as wideband noise," Zalewski explains. This occurs because auditory processing detects frequency components invisible in visual representations.
Similarly, reducing audio bit depth (sample value quantization) creates high-frequency hiss that's more perceptually intrusive than equivalent visual quantization artifacts. Both cases demonstrate how domain-specific human perception shapes effective data representation.
Frequency Domain Vulnerabilities
The inverse experiment—applying audio processing to images—revealed different challenges. Audio techniques like echo effects produced blurred or double-exposure visuals when applied to images. More significantly, frequency-domain transformations using Fast Fourier Transforms (FFT) exposed reconstruction risks:
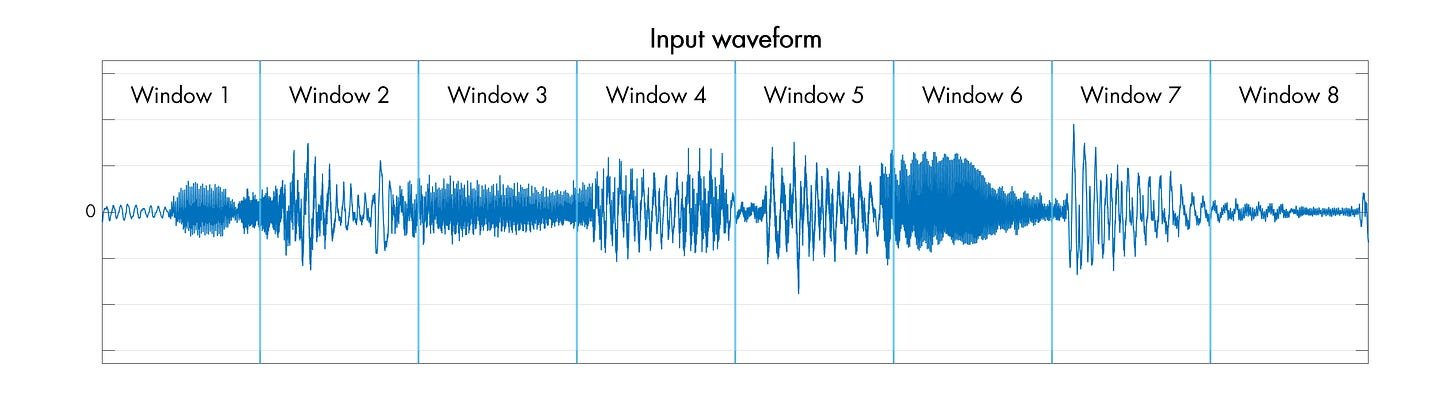
Straightforward FFT windowing creates discontinuities at slice boundaries, causing audible clicks in audio or visual artifacts in images. Zalewski implemented the Hann window function solution—a sinusoidal attenuation curve that enables seamless reconstruction:
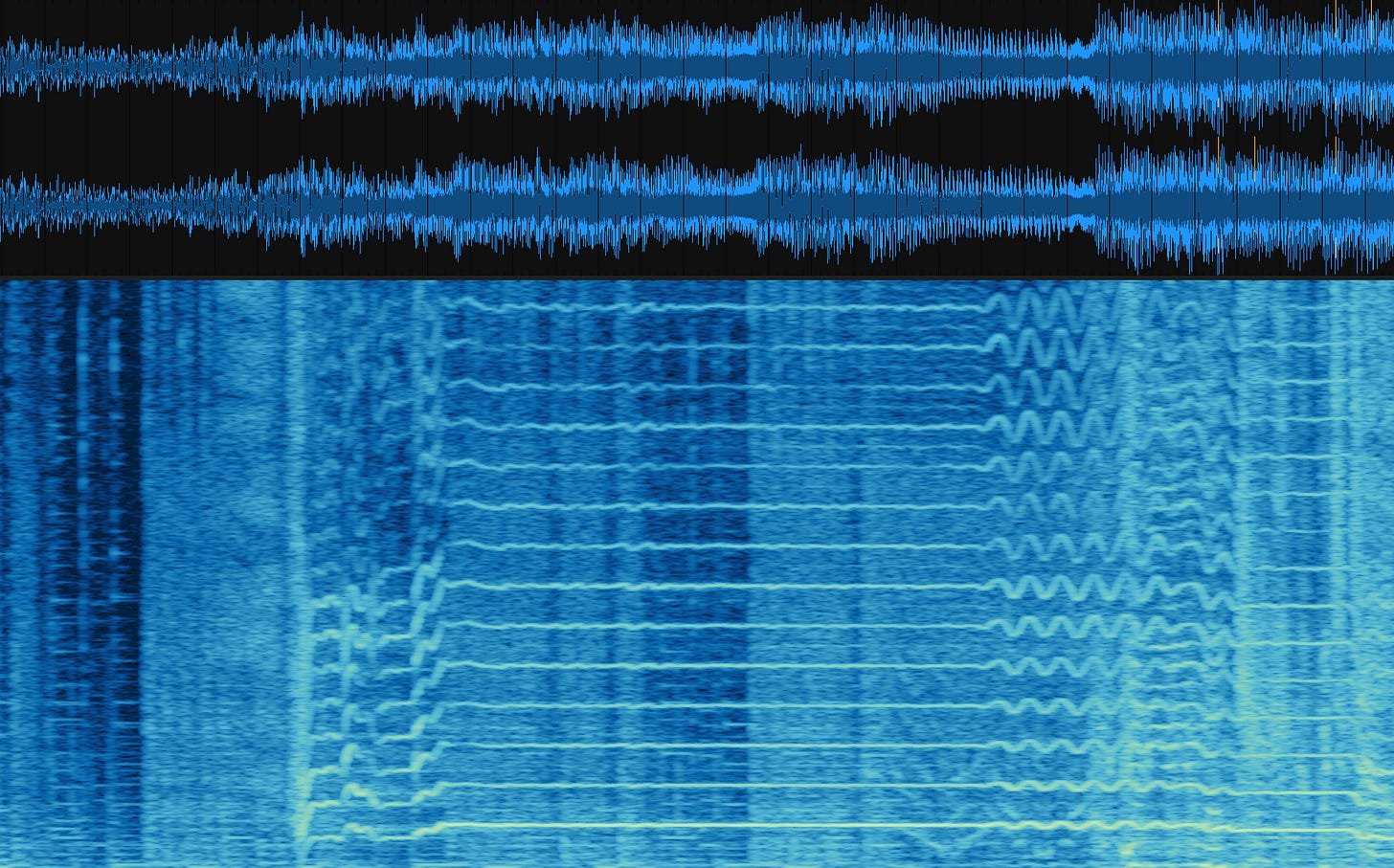
"The Hann function ensures waveform continuity by overlapping and weighting windows so their artifacts cancel out mathematically," the researcher notes. This technique is fundamental to reliable spectrogram analysis used in forensic audio examination.
Security Implications
These experiments highlight critical considerations for security professionals:
Steganography Detection: Unexpected artifacts in downsampled or quantized media may reveal hidden data manipulation. Metallic audio artifacts or unnatural pixel patterns could indicate covert channels.
Forensic Analysis: Understanding domain-specific artifact profiles helps distinguish intentional tampering from processing artifacts in multimedia evidence.
Sensor Data Integrity: Systems processing multiple sensor types (visual/audio) must account for cross-domain transformation risks that could mask or create anomalies.
Watermarking Resilience: Audio watermarking systems using frequency-domain techniques must implement proper windowing to avoid detectable reconstruction artifacts.
Zalewski's open-source implementations demonstrate these effects practically. Security teams working with multimedia should audit signal processing pipelines for domain-appropriate techniques, particularly when handling evidentiary material or implementing data-hiding schemes.
"These aren't just academic quirks," Zalewski concludes. "They reveal how easily cross-domain assumptions can create detectable artifacts—something both attackers and defenders should understand."

Comments
Please log in or register to join the discussion