Researchers demonstrate how trusted bootloaders signed by Microsoft can be exploited to bypass UEFI Secure Boot protections, enabling both legitimate recovery tools and potential malware to run unsigned code without user intervention.

UEFI Secure Boot, introduced in 2013 as a critical defense against bootkits, faces fundamental challenges as security researchers demonstrate how its trusted verification mechanisms can be systematically undermined. The technology, mandatory on modern Windows devices, relies on cryptographic signatures to validate boot components. However, new research reveals how commercially signed bootloaders contain exploitable functionality that completely circumvents these protections.
The Shim Vulnerability
Most Linux distributions rely on the Microsoft-signed shim bootloader to establish a trust chain. Shim functions as a trust bridge, verifying subsequent components like GRUB2 using embedded certificates rather than UEFI's global database. Crucially, shim includes MokManager - a graphical interface allowing users to manually approve untrusted executables during first launch. While designed for legitimate use cases like adding distribution-specific keys, this mechanism creates an entry point for exploitation.
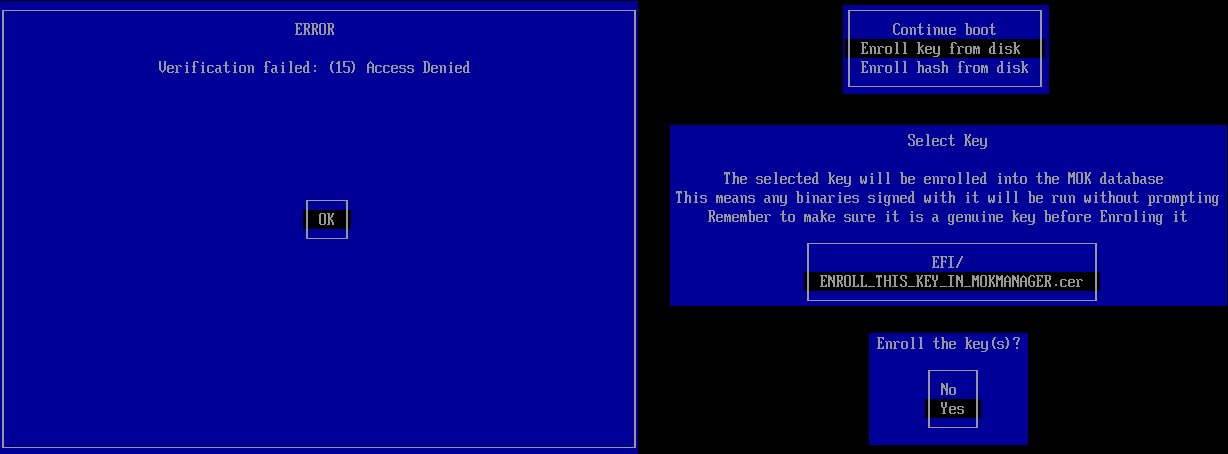 Shim's MokManager interface enabling manual approval of untrusted executables
Shim's MokManager interface enabling manual approval of untrusted executables
Weaponizing Trusted Bootloaders
Security researcher ValdikSS developed two proof-of-concept tools exploiting this trust model:
Super UEFIinSecureBoot Disk: Combines Fedora's signed shim with modified Linux Foundation PreLoader and GRUB2 components. After initial user approval via MokManager, it disables signature verification entirely, functioning like Secure Boot is disabled.
Silent UEFIinSecureBoot Disk: Uses Kaspersky Rescue Disk 18's commercially signed bootloader, which unexpectedly allowed module loading (insmod command). By modifying GRUB's chainloader module to bypass UEFI LoadImage checks, it achieves completely silent execution of unsigned EFI files without first-boot prompts.
The architecture enables booting unsigned operating systems, kernels, and utilities while Secure Boot remains technically "enabled" - ideal for legitimate recovery scenarios but equally dangerous for stealth malware installation.
Security vs. Functionality Tradeoffs
This research highlights inherent tensions in Secure Boot's implementation:
- Legitimate access needs: Enterprise IT teams require methods to boot recovery tools without disabling security features or requiring BIOS passwords.
- Verification gaps: Trusted bootloaders like Kaspersky's contain unexpected capabilities (module loading) that bypass containment mechanisms.
- Revocation limitations: Microsoft can revoke compromised certificates via Windows Update, but this breaks legitimate software until vendors re-sign their bootloaders.
Counterpoint: The Defense Perspective
Microsoft's certification requirements theoretically prevent GPLv3 licensing (due to tivoization concerns) and mandate code audits. However, this research proves the verification process fails to identify potentially dangerous functionality in approved bootloaders. While revocation provides a safety net, the months-long gap between vulnerability discovery and certificate revocation leaves systems exposed.
Implications and Outlook
This exploit methodology fundamentally undermines Secure Boot's promise of verified boot integrity. System administrators gain powerful recovery tools like Super UEFIinSecureBoot Disk, but attackers gain persistence mechanisms that bypass modern hardware security. The anticipated revocation of Kaspersky's bootloader signature will temporarily close one vector, but the structural vulnerability remains: any signed bootloader with module-loading capabilities can be weaponized.
As UEFI firmware becomes more locked-down on corporate devices, these techniques highlight how security mechanisms designed to protect users can be subverted into tools that bypass administrative controls without detection.

Comments
Please log in or register to join the discussion