New research reveals how modern infostealer malware aggregates credentials, session data, and behavioral patterns to build detailed identity profiles that bridge personal and corporate environments.

Modern infostealer malware has evolved beyond simple credential harvesting into sophisticated identity profiling tools. According to recent analysis by Specops Software, attackers now routinely collect browsing histories, session cookies, local files, and system metadata alongside passwords. This aggregated data enables threat actors to connect disparate online identities to real individuals and organizations.
Researchers examined over 90,000 infected devices through 800 million rows of stolen data. "The biggest risk is how easily infostealer data ties multiple accounts and behaviors back to one real person," explains the Specops research team. The datasets revealed patterns showing how attackers connect Windows usernames, reused credentials across services, browsing habits, and local file artifacts to build comprehensive identity profiles.
Identity Convergence Across Environments
Three categories of services appeared most frequently in compromised systems:
Professional platforms: LinkedIn (900k+ records), GitHub, Microsoft Teams, and corporate email domains. These provide job titles, organizational affiliations, and access paths into enterprise networks.
Personal identity services: Facebook, YouTube, and social media containing real names, photos, and connection graphs that validate user identities.
- High-risk services: Government portals (IRS, Canada Revenue Agency) and sensitive platforms like adult content sites. Access to these creates extortion opportunities when linked to real identities.
Notably, even security-conscious users appeared in the datasets through services like Shodan and mil.gov domains. "Technical awareness doesn't equal immunity," the report notes, highlighting how personal device compromises create enterprise risk.
Breaking the Attack Chain
Infostealers succeed through predictable user behaviors: password reuse across accounts, browser-stored credentials, and installation of unauthorized software. Since stolen data often circulates for months before detection, mitigation requires assuming some credentials are already compromised.
Practical defenses focus on disrupting credential reuse:
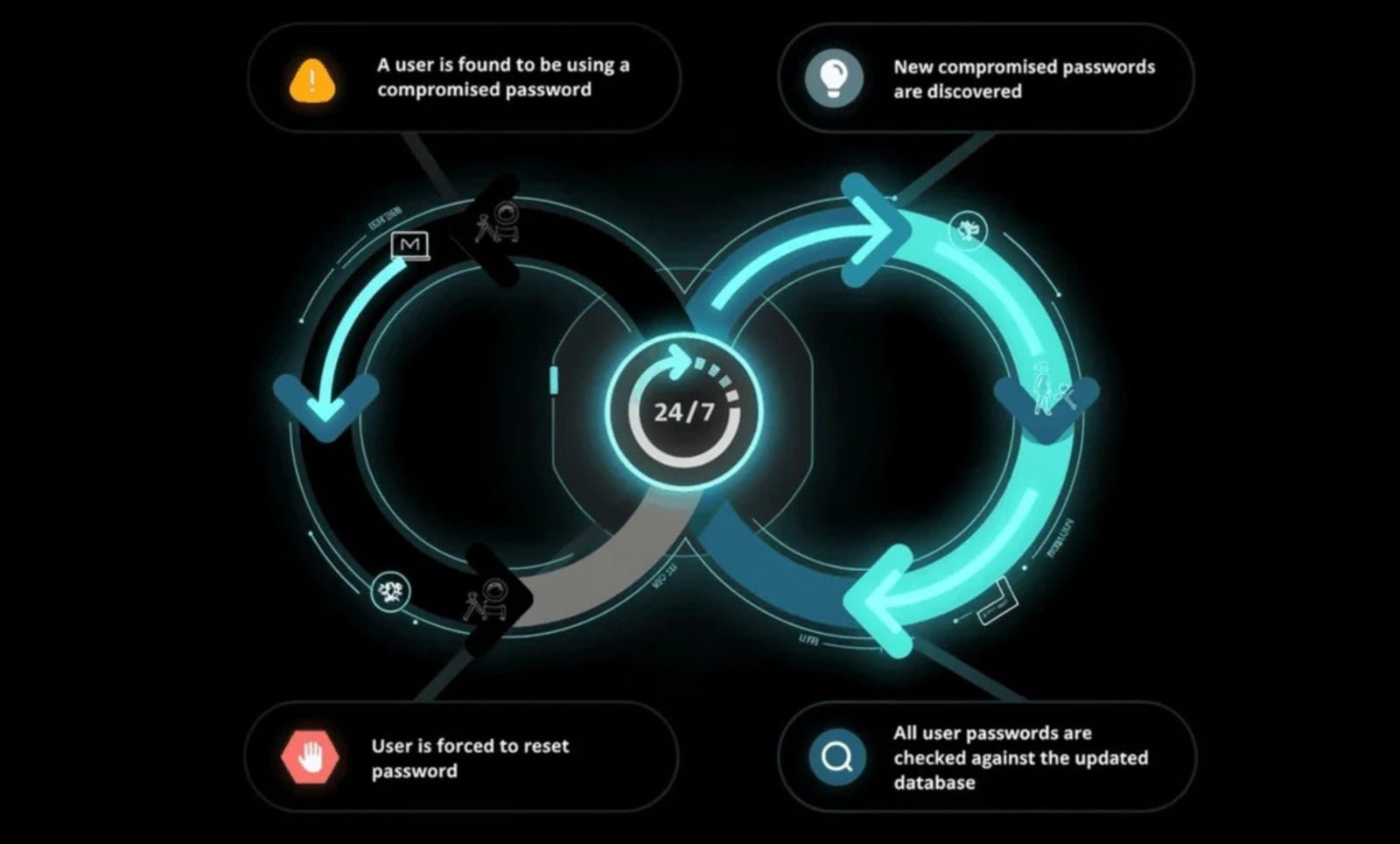
- Continuous compromised password scanning: Traditional password policies only check credentials at creation/reset. Solutions like Specops Password Policy actively scan Active Directory against databases of 5.4+ billion known compromised credentials
- Phrase-based passwords: Encourage longer passphrases instead of complex character combinations that users reuse
- Session monitoring: Detect anomalous logins from unexpected locations/devices
"Credentials harvested from personal devices are routinely tested against corporate environments," the researchers warn. By implementing continuous scanning and blocking known compromised passwords (even if they meet complexity requirements), organizations can reduce attackers' operational window. This shifts password security from static compliance to active threat containment.
For technical teams, the research underscores that identity protection now extends beyond corporate perimeters. As infostealers increasingly bridge personal and professional digital lives, disrupting credential reuse chains remains one of the most effective countermeasures against identity-based attacks.

Comments
Please log in or register to join the discussion