Mandiant has publicly released a comprehensive dataset of rainbow tables designed to crack Net-NTLMv1 authentication hashes in under 12 hours on consumer hardware, a move aimed at finally eliminating the decades-old, insecure protocol from enterprise networks.
Mandiant is releasing a massive dataset of rainbow tables specifically designed to crack Net-NTLMv1 authentication hashes, a protocol known to be insecure since the 1990s. The goal is to make the threat so tangible and easy to demonstrate that organizations can no longer justify keeping it enabled.
Despite being officially deprecated and cryptographically broken for over two decades, Net-NTLMv1 remains stubbornly present in many Active Directory environments. Mandiant consultants regularly encounter it in active attacks, where it serves as a critical link in privilege escalation chains. The protocol's persistence isn't due to technical necessity but inertia and a lack of perceived immediate risk. By releasing these tables, Mandiant aims to lower the barrier for defenders to prove the protocol's insecurity, moving the conversation from theoretical risk to demonstrable, immediate compromise.
The release is a direct collaboration between Mandiant's frontline threat intelligence and Google Cloud's computational resources. The dataset allows security professionals to recover authentication keys using consumer hardware costing less than $600, eliminating the need for expensive cloud services or specialized hardware. This democratization of attack capability is intended to accelerate the final push to disable Net-NTLMv1 across the industry.
The Cryptographic Flaw at the Heart of Net-NTLMv1
Net-NTLMv1's vulnerability stems from its use of the Data Encryption Standard (DES) algorithm, which has been considered weak for years. The protocol's design allows for a known plaintext attack (KPA) if an attacker can capture a Net-NTLMv1 hash without Extended Session Security (ESS) for the specific plaintext "1122334455667788".
The attack chain begins when an attacker obtains a Net-NTLMv1 hash. This is commonly achieved through tools like Responder, configured with the --lm and --disable-ess flags, forcing connections to use the vulnerable protocol. Attackers often coerce authentication from high-value targets like domain controllers using tools such as PetitPotam or DFSCoerce. The resulting hash contains the DES-encrypted password hash of the authenticating object—whether a user or computer account.
 Figure 1: DFSCoerce against a domain controller to trigger authentication
Figure 1: DFSCoerce against a domain controller to trigger authentication
Once the hash is captured, it must be parsed into its DES components. The Net-NTLMv1 hash is essentially a concatenation of three DES ciphertexts. Each ciphertext corresponds to a 64-bit segment of the NT hash, encrypted with a DES key derived from the password. The known plaintext "1122334455667788" provides the necessary input for a known plaintext attack.
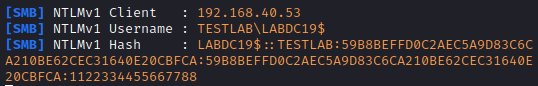 Figure 2: Net-NTLMv1 hash obtained for a domain controller machine account
Figure 2: Net-NTLMv1 hash obtained for a domain controller machine account
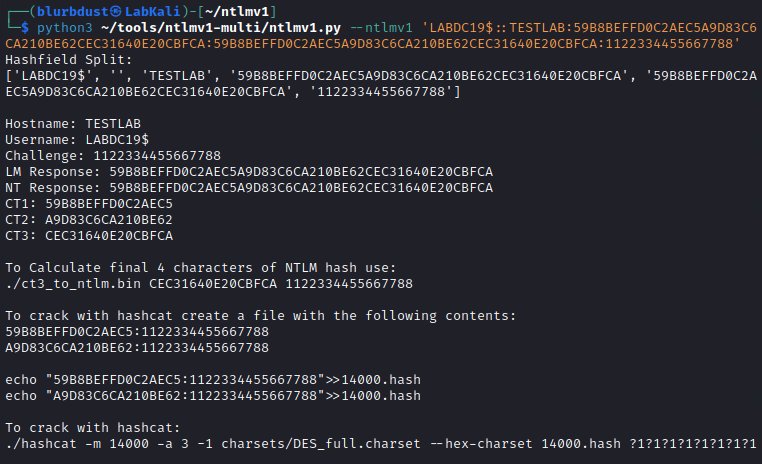 Figure 3: Parsing the Net-NTLMv1 hash into its DES components
Figure 3: Parsing the Net-NTLMv1 hash into its DES components
The rainbow tables Mandiant released are precomputed tables of DES keys and their corresponding ciphertexts. Instead of brute-forcing each key—a computationally expensive process—these tables allow an attacker to perform a time-memory trade-off, looking up ciphertexts to find the original keys almost instantly.
 Figure 4: The Net-NTLMv1 hash is processed into three separate DES ciphertexts
Figure 4: The Net-NTLMv1 hash is processed into three separate DES ciphertexts
The Attack Workflow: From Hash to Domain Compromise
With the rainbow tables loaded, the cracking process becomes trivial. An attacker takes the parsed DES ciphertexts and searches the tables for matches. The tables are designed to work with tools like rainbowcrack or RainbowCrack-NG on CPUs, or GPU-optimized forks like rainbowcrackalack.
{{IMAGE:6}} Figure 5: Loading the DES components for cracking with the rainbow tables
The first hash is typically cracked in seconds, revealing one DES key. The process is repeated for the second ciphertext. Mandiant's dataset allows this entire process to complete in under 12 hours on a standard consumer-grade machine.
{{IMAGE:7}} Figure 6: The first hash is cracked, revealing the first DES key
{{IMAGE:8}} Figure 7: The second hash is cracked, with run statistics displayed
After obtaining the first two DES keys, the third key can be calculated directly using tools like ntlmv1-multi or looked up in a smaller table. With all three keys recovered, the attacker can reconstruct the full NT hash of the compromised account.
{{IMAGE:9}} Figure 8: Calculating the final key to complete the NT hash
The recovered hash is verified using Hashcat's NT hash shucking mode (-m 27000), confirming the attack's success.
{{IMAGE:10}} Figure 9: Verifying the cracked keys with Hashcat's NT hash shucking mode
The final step is privilege escalation. With the NT hash of a domain controller machine account, an attacker can perform a DCSync attack. Using tools from the Impacket suite, such as secretsdump.py, the attacker can impersonate the domain controller and extract password hashes for any account in the Active Directory forest, effectively taking over the entire domain.
{{IMAGE:11}} Figure 10: A DCSync attack is performed using the compromised machine account hash
Immediate Remediation: Disabling Net-NTLMv1
The only effective remediation is to disable Net-NTLMv1 entirely. This must be enforced at the local computer policy level and via Group Policy Object (GPO) across the enterprise.
Local Computer Policy:
Navigate to Local Security Settings > Local Policies > Security Options and set "Network security: LAN Manager authentication level" to "Send NTLMv2 response only."
Group Policy:
In the Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options path, apply the same setting: "Send NTLMv2 response only."
A critical caveat is that local administrators can modify these settings. Attackers with local admin access have been known to temporarily disable protections, execute their attack, and then revert the setting to avoid detection. Therefore, policy enforcement alone is insufficient.
Organizations must implement robust monitoring and alerting for Net-NTLMv1 usage. The primary indicator is Windows Security Event ID 4624 (An Account was successfully logged on). Within the event details, the "Authentication Package" field for "Package Name (NTLM only)" will show "LM" or "NTLMv1" when the vulnerable protocol is used. Any occurrence should trigger an immediate investigation.
Context and Community Impact
This release is not an isolated event but part of a long-standing security community effort. The insecurity of Net-NTLMv1 has been documented since at least 1999, with major presentations at DEFCON 20 in 2012. Tools like Hashcat have supported DES key cracking since 2016, and the concept of rainbow tables for time-memory trade-offs dates back to 2003.
By releasing a comprehensive, ready-to-use dataset, Mandiant and Google Cloud are removing the final technical barriers. The security community has already begun creating derivative works and hosting the tables, further amplifying their reach. This initiative demonstrates how combining deep threat intelligence with scalable cloud infrastructure can be used to dismantle entire classes of attacks, not just respond to individual incidents.
The message is clear: Net-NTLMv1 is not a legacy convenience but a critical vulnerability. With these tables, any defender can now prove the risk in their own environment. The protocol's days are numbered, and this release is designed to ensure that number is small.
Related Research and Resources
This project builds upon extensive prior research:
- Rainbow Table Theory and Practice
- Crack.sh NetNTLM Service
- Hashcat Forum Discussion on NTLMv1
- InternalAllTheThings: Capturing and Cracking Net-NTLMv1
- Hackndo: Stop Using NTLMv1
- Praetorian: NTLMv1 vs NTLMv2
- TrustedSec: Practical Attacks Against NTLMv1
- NetNTLMtoSilverTicket GitHub
- Shuck.sh: NTLM Hash Shucking
The dataset is available for download via gsutil or the Google Cloud Research Dataset portal. Verification instructions and community-hosted versions are also available.
Mandiant's release of these rainbow tables is a strategic move to force a final decision on Net-NTLMv1. By making the attack trivial to execute, they remove the excuse of complexity and place the responsibility squarely on organizations to close this decades-old security gap.

Comments
Please log in or register to join the discussion