Microsoft Defender for Cloud's Kubernetes runtime gating feature is now generally available, introducing proactive vulnerability blocking at deployment time across multi-cloud environments.

Containerized applications have transformed cloud development but introduced critical security gaps. In Kubernetes environments, vulnerable container images remain a primary attack vector, with traditional post-deployment scanning leaving systems exposed during crucial deployment windows. Microsoft Defender for Cloud addresses this with Kubernetes runtime gating, now generally available, which acts as a security checkpoint before containers enter production.
How Runtime Gating Redefines Container Security
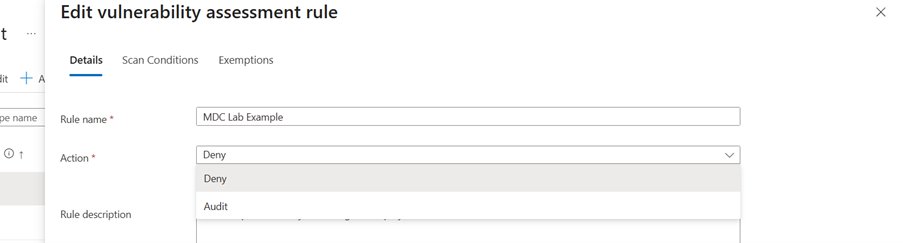 The solution operates through three integrated components:
The solution operates through three integrated components:
- Agentless Vulnerability Scanning: Continuously scans container registries, storing signed security artifacts detailing vulnerabilities (Microsoft's scanning documentation).
- Admission Controller: Deployed to Kubernetes clusters when enabled, this component evaluates deployment requests against organizational policies.
- Policy Enforcement Engine: Applies rules in two operational modes:
- Audit Mode: Allows deployments while logging policy violations
- Deny Mode: Blocks non-compliant images from deployment
Strategic Implementation for Multi-Cloud Environments
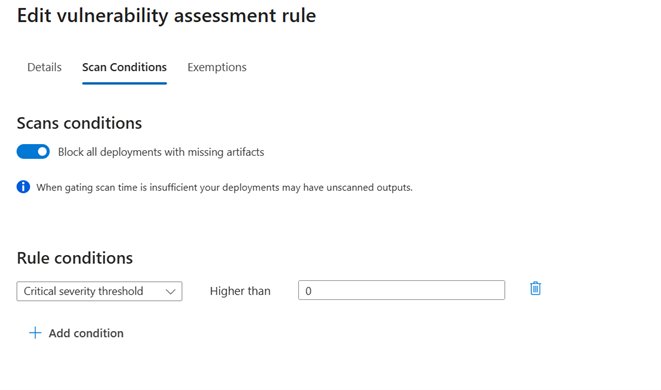 Unlike point solutions requiring custom integration, Defender's approach provides consistent policy enforcement across platforms:
Unlike point solutions requiring custom integration, Defender's approach provides consistent policy enforcement across platforms:
- Azure Kubernetes Service (AKS): Native integration with Azure Policy
- Amazon EKS/Google GKE: Unified rules applied through Defender's admission controller
- Hybrid Deployments: Single policy framework for on-premises and cloud clusters
Comparative analysis reveals distinct advantages:
| Feature | Microsoft Defender | AWS GuardDuty | Google GKE Policy Automation |
|---|---|---|---|
| Deployment blocking | Native | Requires Lambda functions | Limited native controls |
| Multi-cloud consistency | Unified policies | Per-account configuration | Limited cross-cloud support |
| Vulnerability integration | Direct scan artifact linking | Separate Inspector service | Requires Artifact Registry setup |
| Policy management | Centralized in Defender | Distributed | GKE-specific |
Business Impact and Use Cases
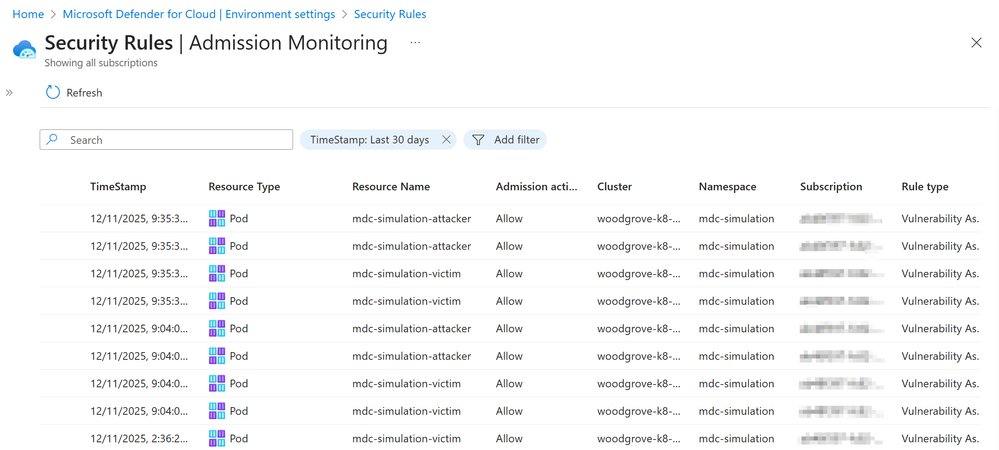 Organizations report measurable outcomes:
Organizations report measurable outcomes:
- Financial Sector: Automated blocking of containers with critical CVEs reduced patching emergencies by 65%
- Healthcare Compliance: Enforced HIPAA requirements by denying deployments without vulnerability artifacts
- DevOps Efficiency: Shift-left implementation reduced deployment failures by 41% after audit-mode tuning periods
Operationalizing DevSecOps
Successful implementation requires cross-team alignment:
- Policy Development: Security and platform teams define risk thresholds (e.g., "block images with >2 critical CVEs")
- Phased Rollout: Begin in audit mode, analyze logs (Admission action inventory), transition to deny mode
- CI/CD Integration: Combine with pipeline scanning tools like Defender CI/CD extension
Strategic Positioning in Cloud Security
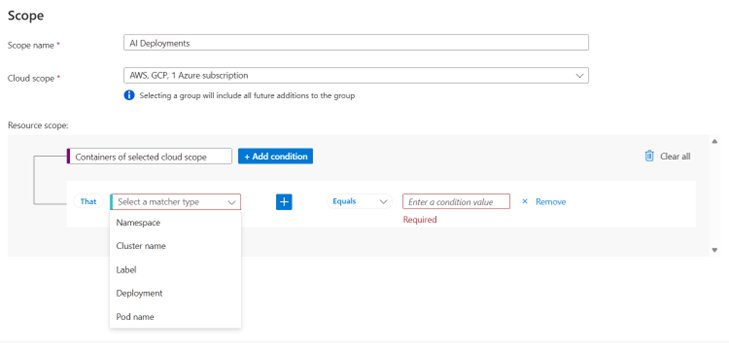 This capability completes Microsoft's container security lifecycle approach:
This capability completes Microsoft's container security lifecycle approach:
- Pre-Deployment: CI/CD scanning
- Registry: Continuous vulnerability assessment
- Deployment: Runtime gating
- Production: Runtime threat detection
For enterprises operating in multi-cloud environments, runtime gating eliminates inconsistent security practices across platforms. A manufacturing client simultaneously blocked vulnerable deployments on Azure and AWS clusters using identical policies, reducing configuration drift by 78%.
Implementation Considerations
- Pricing: Included in Defender for Containers plan ($0.20 per cluster hour + $0.20 per vCore)
- Migration Path: Existing Defender users enable feature without agent redeployment
- Limitations: Currently supports Kubernetes 1.16+; Windows containers require additional configuration
Runtime gating represents a fundamental shift from reactive vulnerability management to proactive risk prevention. By integrating this capability into existing Kubernetes workflows, Microsoft enables organizations to maintain deployment velocity while enforcing uncompromising security standards across hybrid and multi-cloud environments.
Additional Resources:

Comments
Please log in or register to join the discussion