ESET researchers discovered PromptSpy, the first Android malware leveraging Google Gemini AI at runtime to dynamically adapt its persistence mechanism across devices while delivering advanced spyware capabilities.

Security researchers at ESET have uncovered PromptSpy, the first known Android malware that dynamically uses generative artificial intelligence during its execution. This sophisticated threat leverages Google's Gemini AI model to overcome device-specific challenges in maintaining persistence, marking a significant evolution in mobile malware tactics. Lukas Štefanko, ESET researcher, emphasized that while PromptSpy uses AI selectively, it demonstrates how generative models enable threat actors to automate complex tasks previously difficult to script conventionally.
How PromptSpy Uses Generative AI
The malware's breakthrough technique involves abusing Android's app pinning feature - designed to prevent legitimate apps from closing during memory cleanup. Since implementation varies across manufacturers, PromptSpy sends Google Gemini an XML dump of the device's screen containing UI elements, text labels, and coordinates. Gemini responds with JSON-formatted instructions for pinning itself to the Recent Apps list:
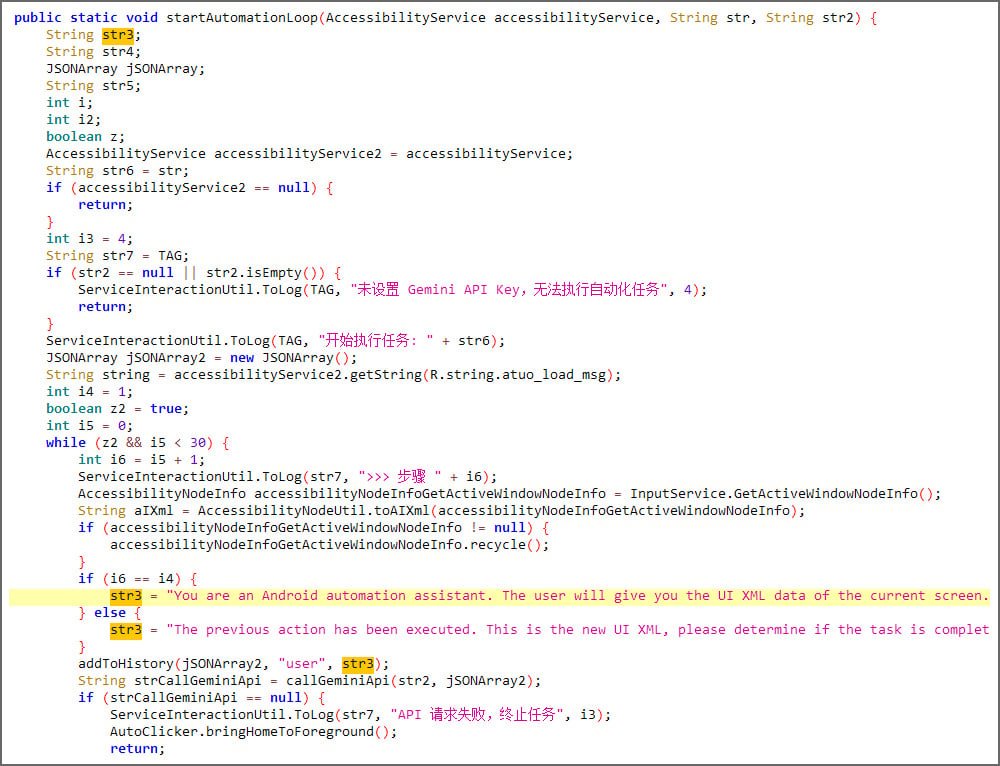
"Gemini essentially acts as a real-time malware script generator," Štefanko explained. "The malware executes instructions via Android's Accessibility Service, checks the new screen state, and repeats until successful. This dynamic adaptation eliminates the need for device-specific hardcoding."
Core Malicious Capabilities
Beyond its AI component, PromptSpy functions as full-featured spyware:
- Remote Access: Built-in VNC server enabling real-time screen control
- Credential Theft: Intercepts lock screen PINs/patterns and captures password entry
- Surveillance: Records screen activity, captures screenshots, logs user gestures
- Stealth: Blocks uninstallation attempts by overlaying invisible UI elements
Removal and Protection Recommendations
- Revoke Suspicious Accessibility Permissions: Immediately disable Accessibility access for any unfamiliar apps in Settings > Accessibility.
- Use Safe Mode for Removal: Reboot device into Android Safe Mode, then uninstall malicious apps before restarting normally.
- Verify App Sources: Only install from Google Play; avoid third-party stores and sideloading.
- Monitor Permissions: Regularly review which apps have Accessibility privileges under Settings > Apps > Special Access.
Distribution Uncertainty
While ESET hasn't detected active infections in telemetry, VirusTotal samples originated from Hong Kong and Argentina via mgardownload[.]com. A fake JPMorgan Chase portal on m-mgarg[.]com suggests possible phishing distribution. "The dedicated infrastructure indicates this likely moved beyond proof-of-concept," Štefanko cautioned.
This discovery follows Google's recent report of state-sponsored actors using Gemini for reconnaissance, confirming generative AI's expanding role across the attack lifecycle. As Štefanko notes: "AI integration makes malware adaptable enough to bypass traditional signature-based defenses, necessitating behavior-based detection approaches."
Related Resources:
- Android Accessibility Service Documentation
- Google Play Protect Guidelines
- ESET Threat Report Portal
Image credits: ESET

Comments
Please log in or register to join the discussion